Blog & newsroom
-

What is the FTP/S EPSV command and when do you use it?
EPSV is a command issued by an FTP/S client to signal the server that it wishes to enter into what is known…
Learn More
-

Setting up a trading partner for automated FTP/S
Overview As explained in the first section of the article Preparing Trading Partner Servers For SFTP Automation, the process of establishing an…
Learn More
-
Using a remote FTP/S service as network storage for your MFT server
JSCAPE MFT Server’s Network Storage module (formerly known as Reverse Proxy) makes it possible to extend the storage of your managed file…
Learn More
-

Setting up a HTTPS to HTTP reverse proxy
Overview Today, we’ll teach you how to set up a HTTPS to HTTP reverse proxy. This service can come in handy if…
Learn More
-
Using a remote SFTP service as network storage for your MFT server
JSCAPE MFT Server’s Network Storage module (formerly known as Reverse Proxy) allows you to utilize various remote services and storage solutions as…
Learn More
-

How to reverse proxy HTTP in 3 simple steps
Overview There may be instances when you’d want external users to access HTTP servers located behind your corporate firewall. A secure way…
Learn More
-

How to set up an SFTP reverse proxy in JSCAPE MFT gateway
Overview An SFTP reverse proxy adds another layer of security to SFTP services. In addition to SFTP’s ability to encrypt data in…
Learn More
-

How to send messages to amazon SQS queues using JSCAPE MFT server
In this post, you’ll learn how to configure JSCAPE MFT Server to send messages to Amazon SQS queues. Amazon SQS queues are…
Learn More
-

Sending SMS notifications of JSCAPE MFT server events via amazon SNS
In a previous post, we outlined the steps of setting up JSCAPE MFT Server to publish messages to Amazon SNS. This setting…
Learn More
-

MFT security Tip: Use digital certificates for server authentication
For today’s MFT security tip, let’s talk about using digital certificates for server authentication. Ideally, when your users attempt to connect to…
Learn More
-

How to publish messages to amazon SNS using JSCAPE MFT server
In this post, you’ll learn how to publish messages to an Amazon SNS (Simple Notification Service) topic using JSCAPE MFT Server. There…
Learn More
-

JSCAPE MFT server 11.2 released
JSCAPE, the leader in platform and protocol independent managed file transfer solutions, is pleased to announce the latest release of MFT Server,…
Learn More
-
How MFT server boosts your Multi-Cloud strategy
Most cloud adopters are starting to discover the benefits of a multi-cloud strategy. These businesses have learned that, in many cases, multi-cloud…
Learn More
-
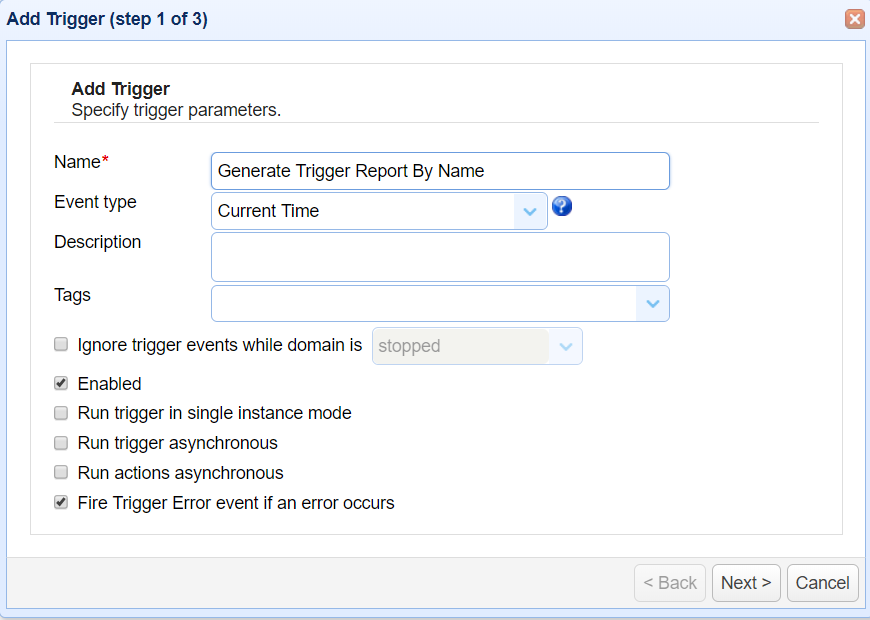
Generate trigger report by custom date using TriggerReportByCustomDate action
This custom trigger action is used to export the details of thetrigger executions for a single trigger by name and custom date…
Learn More
-

MFT security tip: replace default admin passwords
For today’s MFT security tip, let’s talk about replacing default admin passwords. Most software applications come with default admin passwords. You normally…
Learn More
-

How to use google storage as the file storage system of your MFT server
In this tutorial, you’ll learn how to configure JSCAPE MFT Server so that files uploaded to it are streamed directly to Google…
Learn More
-

MFT security tip: encrypting Data-at-Rest
For today’s security tip, we talk about data-at-rest encryption. When your users upload files to your file transfer server, those files are…
Learn More
-

Preparing trading partner servers for SFTP automation
Overview In order to keep transactions secure, you and your trading partners likely use SFTP and other encrypted protocols for your automated…
Learn More
-

MFT security tip: including uppercase and lowercase letters in passwords
In today’s security tip, we talk about including uppercase and lowercase characters in passwords. This is related to our previous video about…
Learn More
-

Logging MFT server log data in a database
By default, JSCAPE MFT Server records domain logs in log files. While in most cases, this will do, some organizations prefer to…
Learn More
-

MFT security tip: use long passwords
It’s time for another MFT Security tip. Today, let’s talk about long passwords and why you would want to require your users…
Learn More
-
Setting SFTP algorithms on your SFTP server
Overview In this post, we’ll discuss the algorithms in a typical SFTP server and explain their basic functions. We’ll cover algorithms for…
Learn More
-

File transfer security tip: disable FTP
Last week, we published the blog post ‘The Ultimate Guide To Hardening Your Secure File Transfer Server‘, where we shared several tips…
Learn More
-
JSCAPE MFT gateway 4.0.4.85 (Patch)
Patch was made addressing the following issues for versions 4.0.3 to 4.0.4:
Learn More
-
JSCAPE MFT server 11.1.5 (Patch)
Patch was made addressing the following issues:
Learn More
-
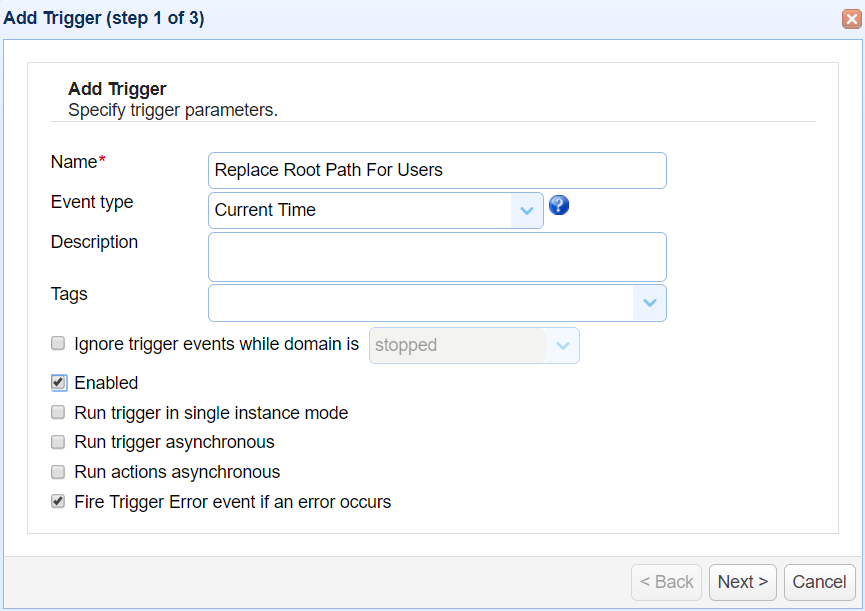
Replace path of all users using ReplaceUsersPath action
This custom trigger action is used to replace all users path.
Learn More
-

Replace root path of the users using ReplaceUsersPath action
This custom trigger action is used to replace the users default root path.
Learn More
-

How well does your MFT vendor meet your needs?
A lot of the companies who come to us for their managed file transfer (MFT) needs aren’t first time MFT customers. Many…
Learn More
-

The ultimate guide to hardening your secure file transfer server
While inherently secure file transfer servers like JSCAPE MFT Server are packed with lots of security features, many of those features need…
Learn More
-

Complete list of JSCAPE MFT server event types
JSCAPE MFT Server users can easily look up a description of each trigger event type by simply clicking the question mark icon…
Learn More
-
Guide on how to set up an SFTP server
Overview This post is for those of you who want to dive right into the steps of setting up a SFTP server.…
Learn More
-

How to prevent duplicate trigger actions
One of the challenges of setting up an MFT Server active-active high availability cluster is in preventing duplicate trigger executions, especially for…
Learn More
-

Roles of server and client keys in secure file transfers – part 2
This is a continuation of Part 1. To preserve confidentiality in secure file transfers, public keys are given to end users while…
Learn More
-

Roles of server and client keys in secure file transfers – part 1
Overview [Last updated on Feb 2019] Secure file transfers typically employ public key cryptography. This cryptographic system involves the use of two…
Learn More
-

Segregating files received from different AS2 trading partners
Files coming in via unauthenticated AS2 file transfers are stored in one common directory. However, in most cases, you would like to…
Learn More
-
JSCAPE releases flagship MFT server to amazon AWS marketplace
JSCAPE, the leader in platform and protocol independent managed file transfer solutions, is pleased to announce the release of its flagship MFT…
Learn More
-

[Video] blocking suspicious IP addresses when MFT server is behind MFT gateway
This is a video version of the tutorial “How To Block Suspicious IP Addresses When MFT Server Is Behind MFT Gateway“. Here,…
Learn More
-

Keeping B2B transactions running through extreme weather conditions
A lot of people don’t take business continuity initiatives seriously. But when a polar vortex in the US, a blizzard in the…
Learn More
-

Use azure files as the file storage system on JSCAPE MFT server
We just published a video version of the blog post, Using Azure Files As The File Storage System Of Your MFT Server.…
Learn More
-
JSCAPE MFT gateway 4.0.1.80 (Patch)
Patch was made addressing the following issues:
Learn More
-
JSCAPE MFT server 11.1
JSCAPE is pleased to announce the release of MFT Sever 11.1.See Enhanced Cloud Integration Added to MFT Server for release details.
Learn More
-
Enhanced cloud integration added to MFT server
JSCAPE, the leader in platform and protocol independent managed file transfer solutions, is pleased to announce the latest release of MFT Server,…
Learn More
-

How to schedule automated file uploads from your server to google storage
We’ve already showed you how to configure JSCAPE MFT Server to monitor a directory for newly added files and then upload those…
Learn More
-

Video: How to connect and upload files from your server to an azure file share
We just published a video version of the tutorial “How To Connect And Upload Files From Your Server To An Azure File…
Learn More
-
Generate failed trigger report using FailedTriggerReport action
This custom trigger action is used to export the details of the Failed Trigger executions in excel format
Learn More
-

How to generate a trigger report using an action
This custom trigger action is used to export the details of thetrigger executions for a single trigger by name in excel format
Learn More
-

How to block suspicious IP addresses when MFT server is behind MFT gateway
If you’ve been using JSCAPE MFT Server, you probably already know it has a built-in feature that enables it to block suspicious…
Learn More
-

Using azure files as the file storage system of your MFT server
It’s possible to configure JSCAPE MFT Server so that the files your users and other client applications upload to your server are…
Learn More
-

How to connect & upload files to azure storage
In this tutorial, we’re going to show you a simple method that will enable you to connect your server to a Microsoft…
Learn More
-

How to leverage cloud storage services when dealing with high volume file transfers
Companies who deal with high volume file transfers on a regular basis quickly run out of storage space. So, with all the…
Learn More
Browse by category
-
(23)
-
(43)
-
(7)
-
(38)
-
(57)
-
(40)
-
(19)
-
(622)
-
(3)
-
(390)
-
(106)
-
(5)
-
(19)
-
(199)
-
(22)
-
(86)
