Why do some organizations excel in protecting their sensitive data during file transfers while others fall prey to cyber threats? What constitutes a fortified IT infrastructure capable of withstanding attacks?
Securing data isn’t about locking it away. Reality demands continuous data flow, collaboration with international teams, vendor onboarding and critical information sharing across platforms.
This post discusses 13 data security solutions that can be implemented when transferring files. From advanced authentication methods to cutting-edge encryption, these strategies ensure that opening your organization’s gates doesn’t mean compromising the security of sensitive information.
Discover ways to implement these solutions across on-premise, SaaS or hybrid environments and significantly enhance your security posture to safeguard intellectual property and maintain robust data privacy.
How does a robust security posture protect sensitive data?
Data breaches can lead to devastating outcomes, including significant financial losses, damage to your reputation or even legal consequences. How does maintaining a robust security posture defend against threats and improve efficiency and reliability?
Let’s start with understanding today’s threat landscape.
What are the critical threats to data security in today’s cybersecurity landscape?
Today’s cybersecurity landscape features a wide range of threats that jeopardize the integrity and confidentiality of critical data. Unfortunately, these threats are both internal and external. Cybercriminals may orchestrate external threats such as malware, phishing and denial-of-service (DDoS) attacks. In contrast, insider threats may arise from accidental mishandling of sensitive data or intentional sabotage by a disgruntled employee.
A recent Redwood webinar highlighted that working with third parties and internal threats are major security concerns, emphasizing the dual nature of security risks, both internal and external. Understanding the dichotomy of these risks is the best way to prepare yourself for an attack by a bad actor.
Implementing data security solutions
Enterprise organizations must proactively adopt a comprehensive security strategy to protect digital assets, regardless of their source. This section will explore 13 effective data security solutions, illustrating each with practical examples from JSCAPE MFT by Redwood. These examples will demonstrate how these solutions can be integrated into your security framework to enhance data protection across various platforms.
1. Multi-factor authentication (MFA): Implement MFA across all systems to significantly reduce the risk of unauthorized access. By requiring users to provide multiple verification forms beyond just the standard username and password, you can ensure the identity of who is accessing your data.
This process typically combines two or more credentials, such as passwords, biometric data like fingerprints, a security token or a code sent to the user’s phone. For instance, Redwood Software’s award-winning managed file transfer (MFT) solution JSCAPE MFT can authenticate a user by requiring their usual Domain User Authentication (what the user knows) and phone authentication (what the user possesses). JSCAPE MFT currently supports these MFA service types.
2. Encrypting files and virtual paths: Encryption scrambles data into characters that mean nothing to the viewer, keeping prying eyes out. Within JSCAPE, encryption can be applied in two primary ways to secure files, enhancing your data protection strategy: event-based triggers or setting up encryption directly on virtual paths.
Encrypting files with triggers: This method involves setting up a trigger that listens for the File Upload event and then automatically applies the PGP Encrypt File action. This targeted encryption approach allows for selective data security based on predefined criteria such as filename and file type, ensuring that sensitive data can be protected.
Encrypting files on virtual paths: 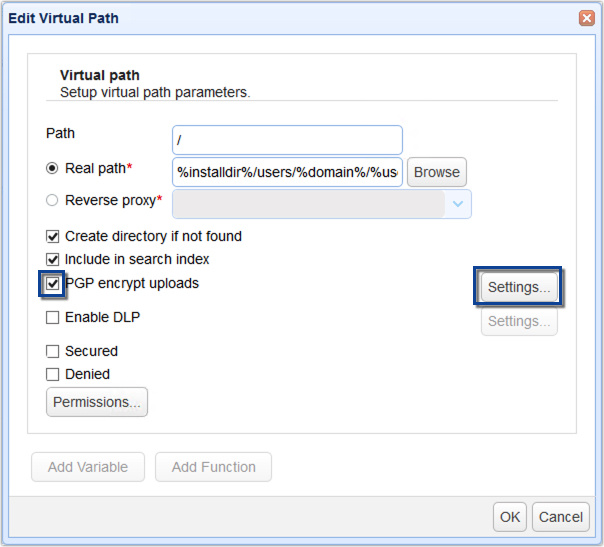
Virtual paths in a file system enable you to map user access to specific physical paths within your domain, streamlining user management and permission settings. These paths can be defined at the User, User Template or Group levels, allowing for centralized control over resource access without the need to manage permissions at the operating system level.
For a broader approach, enable PGP encryption directly on a virtual path to encrypt all files uploaded to that path. To do this, select the virtual path and edit its settings to enable the PGP Encrypt Uploads option. You will then choose an encryption key from the JSCAPE’s built-in key management module or a personal key created through the user interface.
Both methods ensure that sensitive data handled by JSCAPE remains secure through encryption, enhancing your organization’s overall data protection strategy.
3. Comprehensive access management: Get granular with access controls and role-based access management to ensure that employees can only access the data necessary for their roles.
Administrative roles allow you to restrict access within the application by using criteria such as domain, module and tagged data. For instance, you could create a role that permits an administrator to manage triggers only within a specified domain. Another role might restrict an administrator’s visibility to users in a specific location. These examples illustrate how administrative roles can be tailored to specific operational needs, enhancing security and operational efficiency.
4. Proactive threat detection and management: Deploy Intrusion Detection Systems (IDS) to monitor and respond to threats in real-time. Real-time Notifications and Alerts keep you and your trading partners updated on key file transfers.
Discover how Redwood’s threat protection systems can enhance your security infrastructure. Book a demo session to learn more about real-time threat management and discover why an enterprise file transfer solution is necessary.
5. Regular security audits and compliance checks: Conduct frequent security audits to assess the effectiveness of security measures and ensure compliance with regulatory standards. Auditing helps identify vulnerabilities and enforce security policies consistently.
6. Data loss prevention (DLP) strategies: Overview in JSCAPE MFT Enterprise. JSCAPE MFT Enterprise is essential for identifying and safeguarding sensitive data. The SECURITY > DLP Rules module utilizes regular expressions to detect sensitive data at rest, such as credit card numbers, United States social security numbers, United Kingdom national insurance numbers and IBAN account numbers, preventing their unauthorized distribution across all supported file transfer protocols.
MFT Server’s DLP capabilities can be enhanced by either the built-in DLP processor or through integration with an external DLP provider via an ICAP server. This dual approach ensures thorough enforcement of data protection policies, which is crucial for maintaining compliance with security regulations and protecting sensitive information within the server.
7. Advanced firewalls and network security: Advanced Firewalls act as gatekeepers that enforce access policies between your secure internal network and untrusted outside networks, like the Internet. Specify which connections between external clients and your servers should be allowed or denied. This way, you have a barrier against external threats by filtering incoming and outgoing traffic based on an organization’s security policies.
Segmenting the network and using firewalls to create controlled zones that isolate sensitive data and restrict lateral movements are crucial. Additionally, continuous monitoring of firewall traffic and regular security audits will ensure that your team identifies potential vulnerabilities and addresses them promptly.
8. Cloud security (JSCAPE MftaaS): In the JSCAPE SaaS architecture, each customer is isolated within a dedicated zone, enhancing cloud security by segregating user environments. Access to these SaaS environments is secured via HTTPS/TLS 1.2+, ensuring that data transmissions are protected against unauthorized access and cyber threats. Leveraging the robust security measures of the Amazon Web Services infrastructure, JSCAPE provides an additional layer of security, aligning with best practices in cloud security and compliance standards, like helping organizations follow HIPAA and PCI DSS. This architecture supports stringent data protection and privacy regulations, making it a secure choice for managing sensitive information in cloud environments.
9. Supply chain and third-party risk management: Assess and manage risks associated with third-party vendors and supply chains. This risk management includes conducting security audits of vendors and ensuring third-party services comply with the organization’s security standards. This may mean third parties access your environment using a firewall or via DMZ streaming, keeping your organization secure by isolating the entrances used by your partners.
10. Data backup and disaster recovery: Implement robust data backup and disaster recovery procedures to maintain data integrity and ensure business continuity:
Data security solutions for file transfer can be enhanced by configuring synchronization of all configuration changes to a failover server. The role of a failover server is to seamlessly assume the responsibilities of a production server if it becomes unavailable. JSCAPE MFT stands out from other MFT software solutions by enabling the failover server to rapidly take over without disruption, ensuring continuous operation and data security
11. Proactive trigger management: Trigger management in MFT servers is critical to data security solutions. By setting up event-based triggers to execute only upon actions by a particular user, time frame, event type and more, you can prevent file transfer automation from inadvertently moving malicious data into your organization.
12. Privacy and data protection policies: Develop and enforce privacy policies that comply with data protection laws and regulations. This effort includes managing data access, storage and transfer procedures to protect user privacy and ensure legal compliance. Because these security best practices are constantly evolving, it’s important to choose an MFT solution like JSCAPE which is constantly investing in its solution. This ensures your solution stays up to date without requiring you to become an expert in privacy and data security yourself.
13. Security posture assessment tools: Effective use of security posture assessment tools is crucial. Your IT experts not only want to protect the organization; they also want to understand how at risk they are of becoming a victim of an attack or breach. This can be done by taking a comprehensive look at your organization’s security posture:
- Inventory IT assets: Catalog all hardware, software and cloud resources to understand the organization’s complete attack surface.
- Map the attack surface: Use the tools to analyze and identify vulnerabilities, misconfigurations and potential cyber threat entry points, pinpointing critical areas of weakness.
- Assess cyber risk and resilience: Evaluate the likelihood and impact of potential attacks and assess the organization’s readiness to detect, respond and recover from security incidents.
- Prioritize and remediate vulnerabilities: Leverage insights from the risk assessment to prioritize and fix the most critical vulnerabilities, enhancing your security framework.
- Continuously monitor and improve: Maintain ongoing vigilance with continuous monitoring to adapt to new threats and ensure a robust and compliant security posture.
- Incident response and management Develop and maintain an incident response plan that outlines procedures for addressing security breaches. This plan should include containment, investigation and recovery steps to minimize damage and restore operations as quickly as possible.
Now, let’s explore tips for selecting the right solutions to protect your IT infrastructure effectively.
Tips for selecting the right data security solutions
When determining which data security solutions will best serve your organization, assess your company’s needs, including the type of data you handle, regulatory requirements, the scale of your operations and your existing security posture. Here are a few expert tips to guide the selection process:
Understand your data: Begin by taking inventory of the types of data your enterprise manages. Are you transferring financial data, personal data, intellectual property or other forms of sensitive data? The classification will help identify the level and type of protection required. Assessing this helps in the data discovery process and ensures that IT departments handle sensitive information with the appropriate security controls.
Evaluate regulatory compliance: Adhering to regulations such as SOX for financial reporting and GDPR for data protection in the European Union is essential. Your choice of data security solutions should support and simplify the compliance process, ensuring you meet privacy regulations.
Consider scalability: As your business expands, your security requirements will also increase. Choose scalable solutions to handle growing data volumes and adapt to evolving security threats. These solutions should include robust cloud security capabilities for both on-premises and cloud data systems, providing comprehensive data protection across all your operational environments.
Assess existing infrastructure: Carefully evaluate your current IT environment to ensure compatibility with your existing infrastructure, which will minimize integration challenges and potential security gaps. This assessment should include a thorough review of endpoints, data centers and multi-cloud setups to guarantee that security tools integrate smoothly across all platforms.
Do you need additional support in assessing your existing IT infrastructure? Request a demo session with one of our experts to learn what’s possible.
Establish budget constraints: Be realistic about what you can afford, but also recognize that skimping on data security can lead to the most costly breaches or velocity-reducing tech debt. Consider the long-term benefits of investing in robust cybersecurity measures, including advanced threat detection systems and secure data platforms.
Vendor reputation and support: Research potential providers’ reputations, the robustness of their customer service and the quality of their technical support. Do they invest in a feature roadmap and innovation, or are MFT solutions an add-on and afterthought?
Ensure that the vendors have a proven track record in security, particularly in areas such as encryption keys management, DLP and Identity and Access Management (IAM) systems. If the solution does not have regular updates, they cannot stay on top of security best practices and are forced to be reactive.
Conduct a risk assessment: A comprehensive assessment can help prioritize the threats to tackle first and the solutions that best mitigate them. This assessment includes understanding potential vulnerabilities, cyber threats and insider threats that could impact your organization.
Check for Flexibility and Customization: Select security solutions that enable you to tailor security protocols to meet your organization’s specific needs. This customization may include modifying access controls, security policies and data encryption methods to align precisely with your security requirements.
Prioritize user-friendliness: Solutions should be manageable and not require unreasonable training to use effectively, increasing the risk of human error. Choose a solution that junior- and senior-level IT managers can efficiently operate.
User-friendly interfaces and no/low-code automation can significantly reduce the chances of mistakes and improve security efficiency.
Look for integrated defense strategies: Opt for solutions that provide a layered approach to security, combining several tactics, such as firewalls, access management and multi-factor authentication, for a more robust defense. Integrated solutions help create a resilient security posture against various cyberattacks, including malware, ransomware and phishing.
Incorporate machine learning and AI: Use machine learning and AI technologies for real-time threat detection and behavior analytics. These tools can provide advanced insights into security risks and help automate complex security operations.
Implement zero trust architectures: Adopt zero trust principles to enforce strict access controls.
Zero Trust Architecture (ZTA) is a cybersecurity strategy introduced by John Kindervag in 2010 as a Principal Analyst at Forrester Research. Unlike traditional “defense-in-depth” approaches that operate under a trust model, ZTA operates under the assumption that all network traffic is potentially hostile.

The architecture is designed to incorporate security deeply within the network’s DNA, adhering to principles that require secure access for all resources, strict access controls based on necessity, verification over trust, thorough inspection of all incoming log traffic for malicious activity and network design that starts from the inside out.
By considering these factors, organizations can make decisions that strengthen their data security solutions and ensure robust protection against the dynamic and evolving landscape of cyber threats throughout the lifecycle of their data systems.
In the complex and ever-evolving world of cybersecurity, top enterprises are working hard to remain vigilant and proactive in implementing comprehensive data security solutions tailored to specific use cases, including their file transfer operations.
By adopting a strategic approach that includes robust authentication, encryption, threat detection and incident management, organizations can protect themselves against the myriad of cyber threats that pose risks to their operations and reputation.
Implementing these 13 data security solutions and referencing these tips for selection will empower your enterprise to meet compliance requirements and maintain a secure and resilient digital environment. Connect with a product expert to see how JSCAPE’s security features can strengthen the defenses of your IT infrastructure.





