Active vs. passive FTP simplified
Data connection mode
When your File Transfer Protocol (FTP) server runs behind a firewall or Network Address Translation (NAT) router, your users may sometimes encounter connectivity issues. One of the most common causes of FTP connection issues is the data connection mode being used. This mode can be either active or passive. Certain firewall configurations will only allow FTP connections if the data connection is set to a mode that works with a given configuration.
This blog will explain the differences between active and passive FTP data connection modes, how they impact firewall configurations and what mode we recommend you use going forward. Although active and passive modes are mentioned in RFC 959, the explanations can be too technical. Before we tackle the main discussion, let’s first review how FTP connections are designed.
FTP command channel and data channel
Every FTP connection consists of a command channel and a data channel. FTP commands and command responses go through the command channel, while the data or file transfers themselves pass through the data channel.
Your FTP server normally accepts command requests on TCP port number 21. Unless you configure it differently, an FTP command channel will use port 21 on the server side. As for the data channel, the server port number will depend on the data connection mode used. In active mode, the server port number for the data channel is usually port 20. In passive mode, this would be a random port number.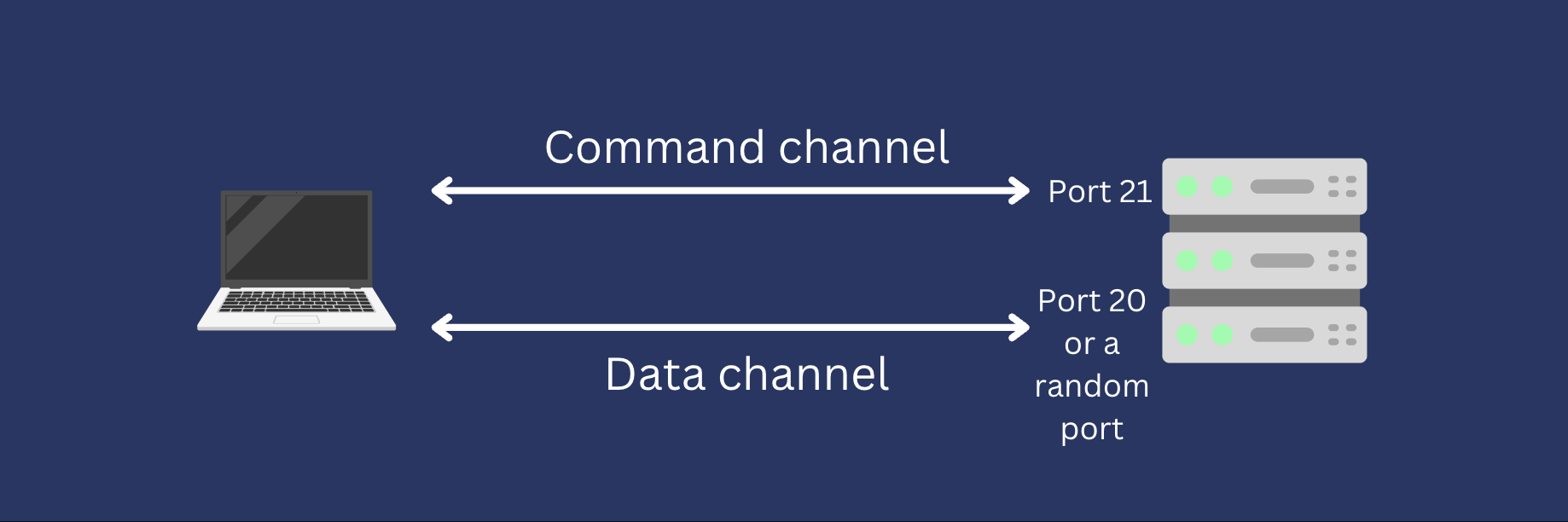 It’s worth noting that other file transfer protocols, such as SSH File Transfer Protocol (SFTP) and Hypertext Transfer Protocol (HTTP), use a single channel for both command and data transfers.
It’s worth noting that other file transfer protocols, such as SSH File Transfer Protocol (SFTP) and Hypertext Transfer Protocol (HTTP), use a single channel for both command and data transfers.
Are you still using an SFTP server but ready for unrivaled file transfer reliability?
If you're looking for reliable file transfer operations and the ability to scale and standardize these processes, let us show you what might be missing as you work towards enhanced performance.
Schedule a product demo with one of our specialists, who will reveal how to improve operational efficiency while keeping your data secure.
Want to try this for yourself?
This two-channel property is unique to the FTP protocol and its successor, FTP-over-SSL a.k.a FTPS. Indeed, FTPS connections are likewise susceptible to the same firewall connectivity issues that affect FTP. So, if you’re using FTPS instead of FTP, you also benefit from our discussion here.
If you need assistance using secure file transfer protocols or securing your FTP connections, you can schedule a demo with one of our experts.
Let’s now differentiate between active mode and passive mode FTP. Pay attention to the directions of the arrows in the diagrams below. The tails of those arrows indicate which machine—the client or the server—is initiating the command or data connection. For instance, it should be easy to see that the FTP client always initiates the command channel connection (the top arrow) regardless the mode used.
What is active mode FTP?
Older versions of FTP used to run on only one data connection mode, which we now call active mode. Since this mode is common in legacy FTP systems, many FTP software use this as the default mode.
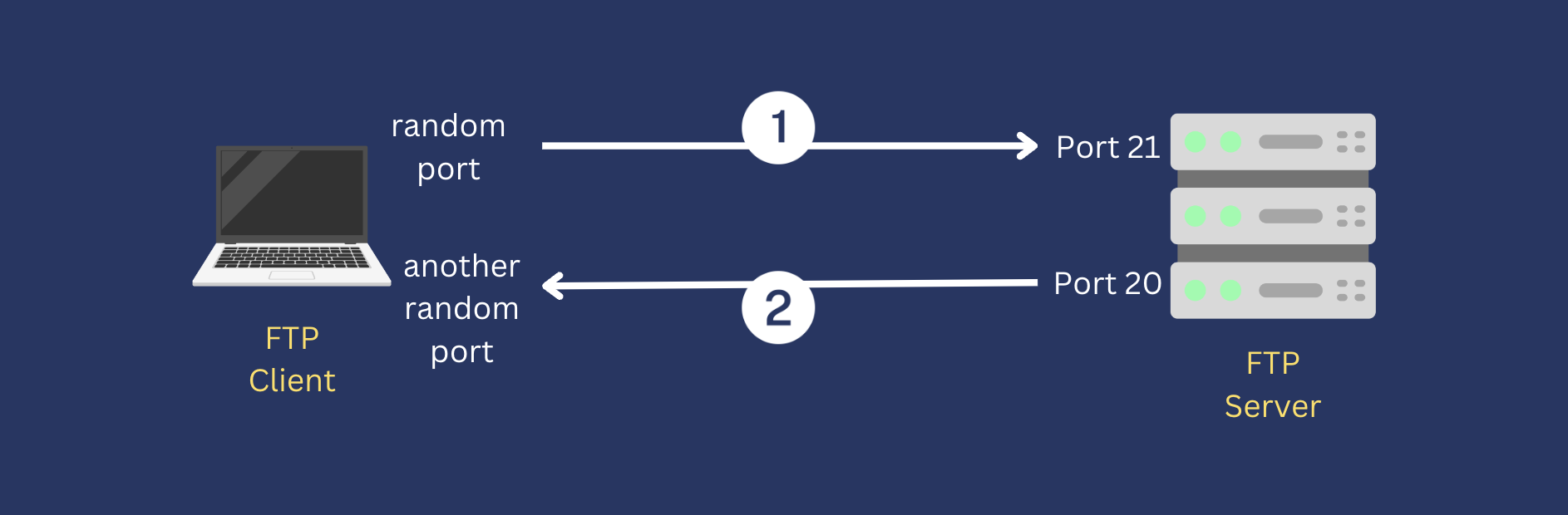
In active mode FTP, an FTP client and FTP server establish connections in the following manner. Please note that the entire process has been compressed into two steps, omitting certain steps, like ACK replies for simplicity.
-
A user typically connects to an FTP server on server port number 21 from a random port on its file transfer client. This client-side random port and server-side port 21 constitute the command channel or control connection. The client also sends the PORT command, while specifying what random client-side port the server should connect to. This second client-side port will be used later on for the data channel.
-
After that, the server connects from port 20 to the client-side port specified in step 1 for the data channel. So, in active mode, the FTP server initiates the data connection. Once the data connection is established, file transfers and directory listings are coursed through this connection.
What is passive mode FTP?
As hinted earlier, passive mode FTP is the more recent data connection mode. While older systems only support active mode, modern GUI-based or command-line FTP clients also support passive mode. Let’s now go over the simplified steps for establishing passive connections.
-
As in active mode FTP, the client initiates the command channel connection. Again, the FTP client connects to the FTP server TCP port 21. But instead of sending the PORT command, the client sends the PASV command. This tells the server that the client wishes to transfer files using passive mode. The server, in turn, picks a random port from its own set of ports for the data channel and then notifies the client about it.
-
Once the client has determined which server port to connect to for the data channel, it initiates the data channel connection. The client connects from a random port to the data port specified by the server in step 1. Once the data connection is established, data transfers and directory listings are made through this connection.

You’re ready to discuss the firewall considerations you need to make when dealing with FTP in either active or passive mode.

Firewall considerations
As mentioned earlier, the arrow tails in the two diagrams above indicate which machine—client or server—is initiating a connection. These dynamics can affect how a firewall responds to an FTP connection attempt.
Client-side firewalls
Most firewall configurations are lenient to outbound connections but more restrictive when it comes to inbound connections. So, for example, if you have a client-side firewall and an FTP client initiates a connection to a remote FTP server at port 21, the firewall will likely allow that connection to pass through. That’s because from the firewall’s point of view, the connection attempt is outbound.
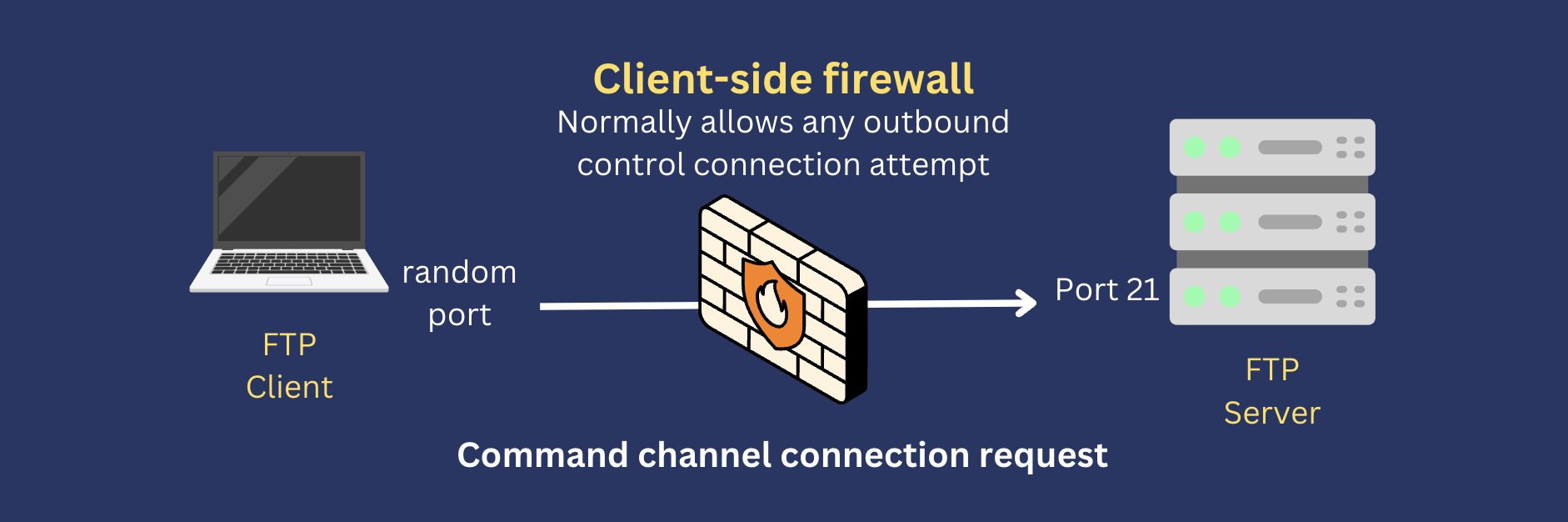
In fact, from any client-side firewall’s point of view, all FTP control connection attempts are outbound. So, FTP clients shouldn’t have a problem establishing a command channel with an FTP server. However, the same thing can’t be said for data connection attempts.
If the client uses active mode FTP, the server will initiate the data connection. Since the connection is inbound from the firewall’s point of view, that connection attempt will likely be blocked.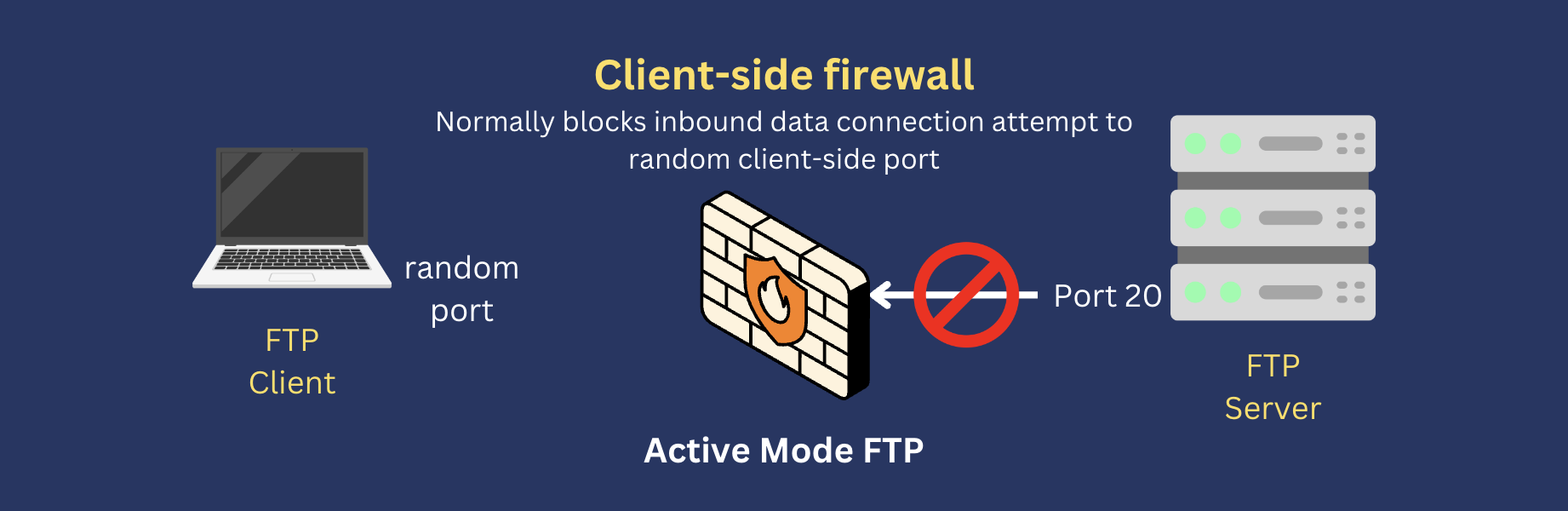
So, if a user encounters a connectivity issue while attempting to connect to your FTP server, check your server logs. If the logs show that the control or command connection is going through, determine whether the client is using active mode.
If it is, a client-side firewall is likely block the data channel connection. Bear in mind that any client-side firewall can do this. Most people use Microsoft Windows. So, in most cases, the first firewall to check would be your user’s Windows firewall.
You’re less likely to encounter similar issues with a passive FTP session. Passive FTP works better with client-side firewalls because both the command connection and the data connection will be client-initiated. So, from the firewall’s point of view, all connection attempts are outbound.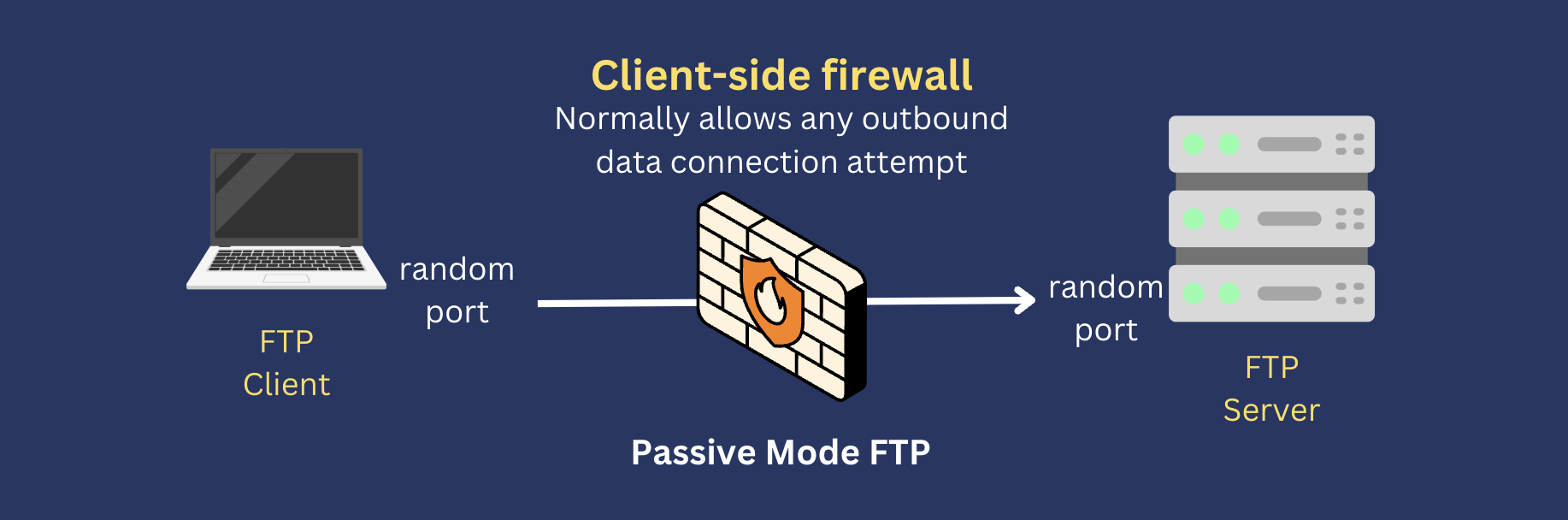
All right, that’s for client-side firewalls. Before we do server-side firewalls, here's a friendly reminder that you can test JSCAPE features inside your own environment with support from a product expert. Click here to request your no-obligation, risk-free trial.
Server-side firewalls
When you deploy an FTP server, you’ll want your server-side firewall to allow FTP clients to connect with that server. That means you’ll want to open port 21 on that firewall. This would allow any command channel connection attempt to pass through. But how about data channel connections?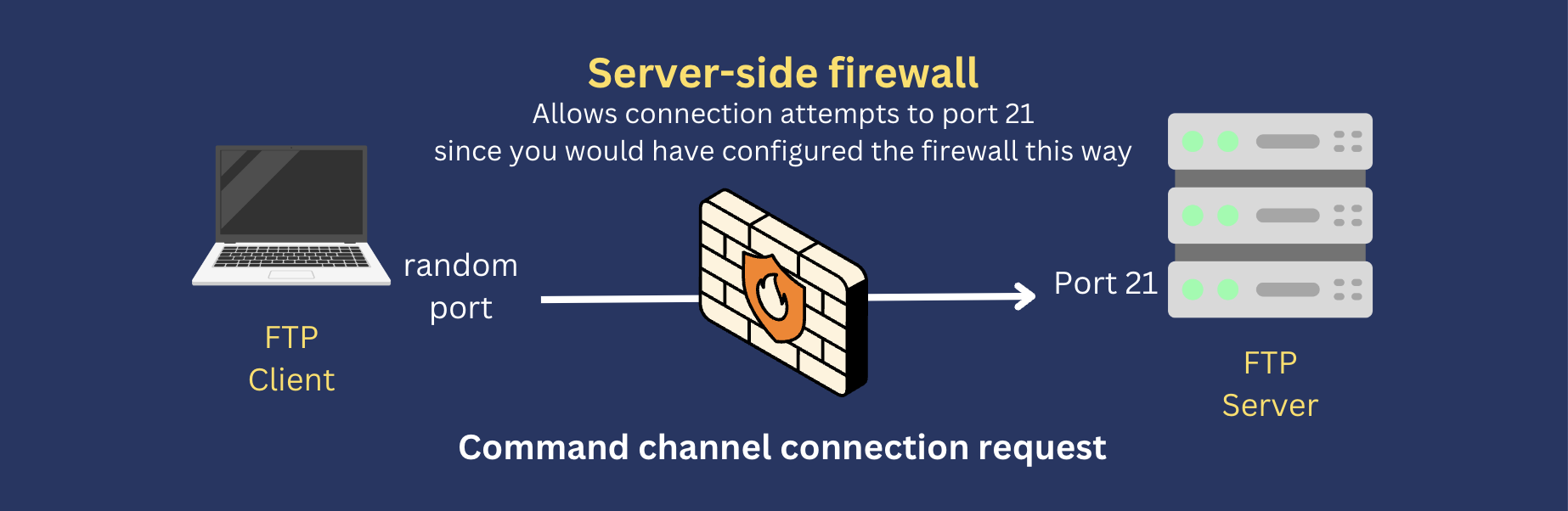 Normally, a server-side firewall won’t pose any problems to active mode FTP connections. That’s because the connection attempt is directed to the client, which means, from the firewall’s point of view, the connection attempt is outbound.
Normally, a server-side firewall won’t pose any problems to active mode FTP connections. That’s because the connection attempt is directed to the client, which means, from the firewall’s point of view, the connection attempt is outbound.
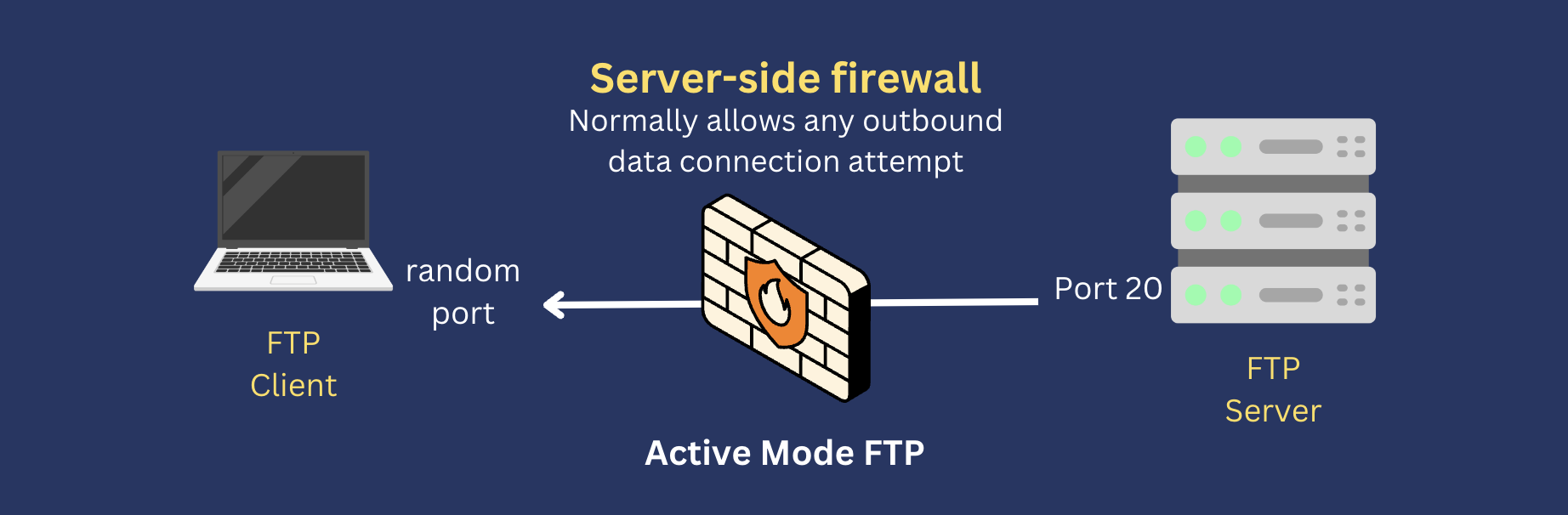
Since a passive mode FTP data connection attempt would be inbound to a server-side firewall, the firewall should block that attempt, right? Generally speaking, yes. That’s why you should explicitly open a range of ports on your server-side firewall when you’re using passive mode FTP.
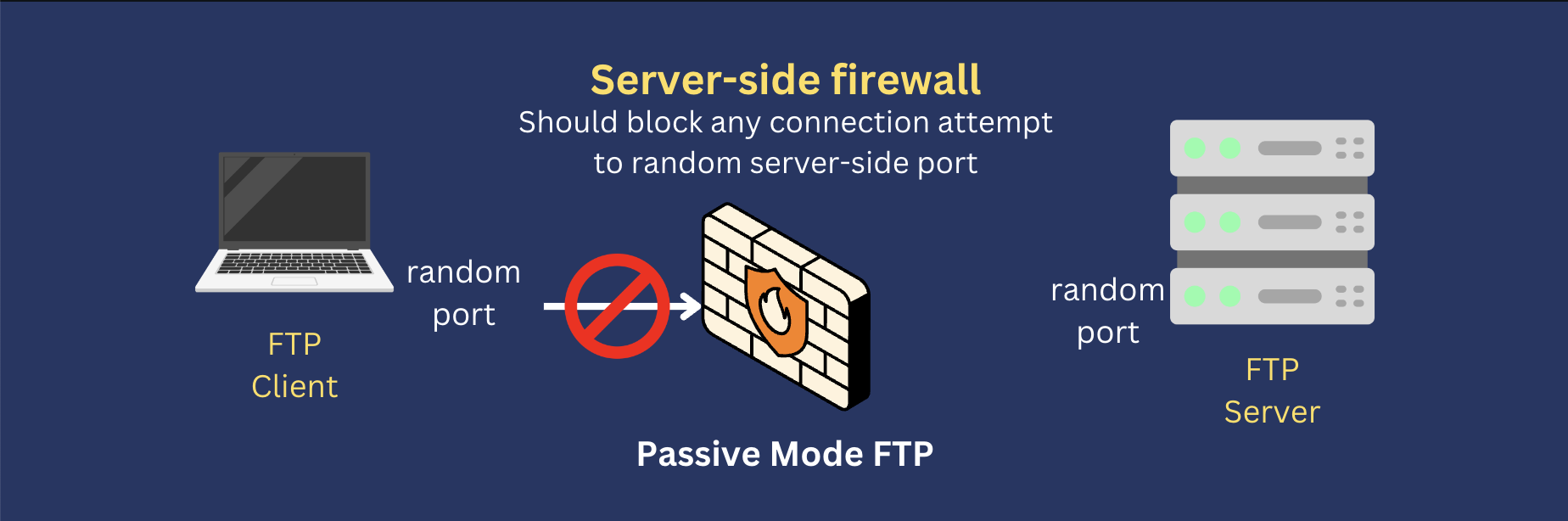
Active FTP vs. Passive FTP - Which is better?
Based on our discussion above, connection issues can happen on a client-side firewall or a server-side firewall. Apparently, a client-side firewall would normally block active mode FTP data connection attempts, while a server-side firewall would normally block passive mode FTP data connection attempts.
One way to address an active mode FTP connectivity issue is to allow inbound connections to certain client-side random ports on your client-side firewall. Similarly, one way to address a passive mode FTP connectivity issue is to allow inbound connections to certain server-side random parts on your server-side firewall. So, which option is better?
In real-world scenarios, you normally have no control over most client-side firewalls. For example, if you provide FTP file transfer services to customers, you have no control over those customers’ firewalls. So, while opening random ports on client-side firewalls can theoretically fix active mode FTP connectivity issues, the solution isn’t easy to implement.
A more realistic solution would be to use passive mode FTP and configure your server-side firewall accordingly. You likely own or at least manage your server-side firewall, so it’s much easier to change firewall settings there. So, yes, we recommend you use passive mode FTP moving forward. It’s going to be much easier to avoid connectivity issues that way.
Security considerations when setting up passive FTP
Before you go and start opening random ports on your server-side firewall, know that opening ports in wanton abandon can increase your exposure to internet-based cyber threats. The right approach is to configure a range of ports on your FTP server for passive mode FTP data connections and then only open those same range of ports on your firewall.
Setting your passive FTP port range
The specific number of ports you need to open for passive FTP largely depends on the expected number of concurrent connections or file transfers. When making a rough estimate, it’s important to understand that some file transfer sessions involve multiple files and each file will require one port. If a user downloads 10 files within a single logon, then 10 ports will be used.
So, when deciding how many passive ports you need to open, you must consider the possibility that a single client may open multiple concurrent passive connections. While no hard and fast rules dictate the ideal number of ports comprising a port range, you will want to project your maximum number of concurrent users and allocate a sizable allowance based on that estimate.
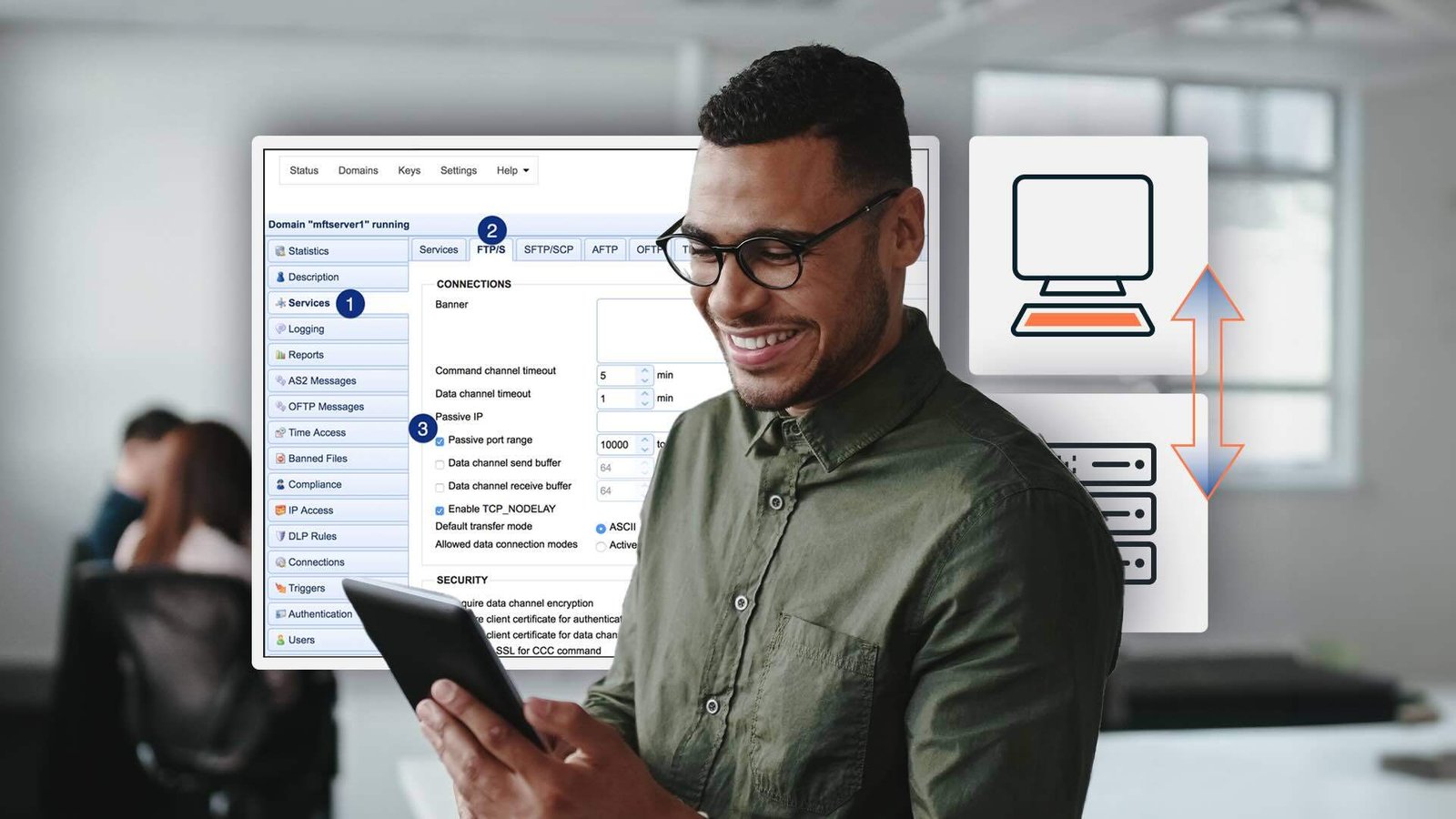
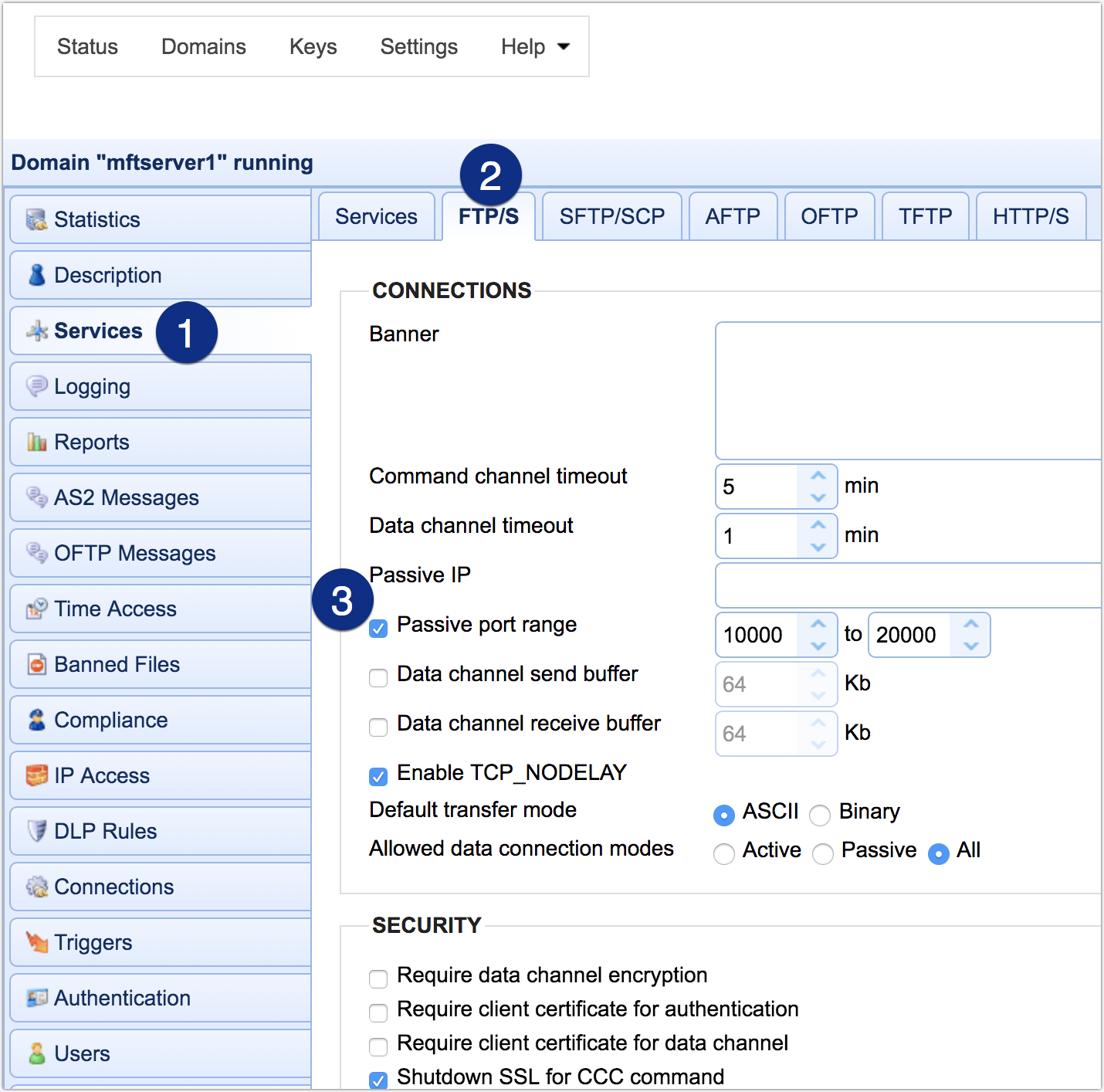
Your FTP server should allow you to set your passive port range. For example, if you’re using JSCAPE MFT Server by Redwood, you can specify your passive FTP port range by going to Services > Listeners > FTP/S tab. Tick the Passive port range checkbox and set a minimum and maximum number.
Because low ports (particularly those < 1024) are reserved, choose a high port range (i.e., large numbers). For example, you may set the range from 5000 to 6000. That’s just an example. Use your own set of values. If the IP address your FTP server uses in responding to passive connection requests is not routable through the Internet, you'll need to enter your public IP address in the Passive IP field.
Get Your Free Trial
Want to try this for yourself?
- Request a free trial
- Connect with a JSCAPE product expert
- Test JSCAPE MFT Server, a multi-protocol, platform-independent managed file transfer solution users are most likely to recommend, according to G2.