Category: SFTP
-

SFTP vs. FTPS: Which file transfer software is best for business use?
What is SFTP? SFTP is a file transfer protocol that’s normally packaged with Secure Shell (SSH), the network protocol most IT administrators…
Learn More
-

Choosing the right SFTP hosting for advanced file transfer workflows
Most Secure File Transfer Protocol (SFTP) hosting services can handle basic file transfer tasks, but not all are suitable for advanced workflows.…
Learn More
-

How to use SFTP compression
File Transfer Protocol (FTP) has very few advantages over Secure File Transfer Protocol (SFTP). However, if you measure the transfer speed between…
Learn More
-

Using SFTP with the Cloud
For several decades, SFTP, which stands for Secure File Transfer Protocol or SSH File Transfer Protocol, has been arguably the most widely…
Learn More
-

7 alternatives to an SFTP platform you probably didn’t know
Many of our customers use Secure File Transfer Protocol (SFTP) for their business file transfers. While SFTP is certainly a good choice…
Learn More
-
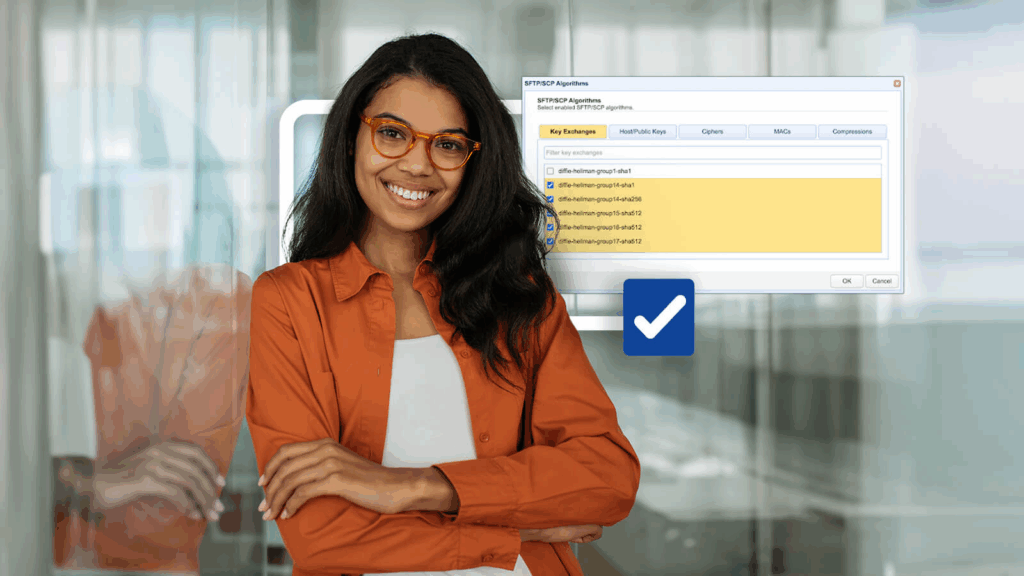
Fixing SSH/SFTP client connection issues involving Diffie-Hellman-Group1-SHA1
When you’re troubleshooting connectivity issues between Secure Shell (SSH)/Secure File Transfer Protocol (SFTP) clients and servers, it pays to inspect the error…
Learn More
-

When SFTP isn’t enough — signs you need an MFT solution
If SFTP is limiting your operations, consider an MFT solution for automation, protocol versatility, and advanced security. Explore our detailed blog post…
Learn More
-

AS2 vs SFTP—What’s the difference?
What is dropdown#toggle” data-dropdown-placement-param=”top” data-term-id=”292784916″>Applicability Statement 2 is a dropdown#toggle” data-dropdown-placement-param=”top” data-term-id=”292784930″>data transfers. It’s based on the dropdown#toggle” data-dropdown-placement-param=”top” data-term-id=”292784907″>EDI).
Learn More
-
SFTP vs. MFT: Benefits of an MFT solution
When you first start identifying the right file transfer solution for your organization, you’ll encounter these two acronyms: MFT and SFTP. SFTP…
Learn More
-

How To Automate An SFTP File Transfer
Automated secure file transfer protocol (SFTP) file transfers are traditionally done through scripts, but there’s a much easier way. In this tutorial,…
Learn More
-

What is AES encryption and how does it work?
Overview: What Is AES? First adopted by the U.S. government to protect classified information, Advanced Encryption Standard (AES) has long gained global…
Learn More
-

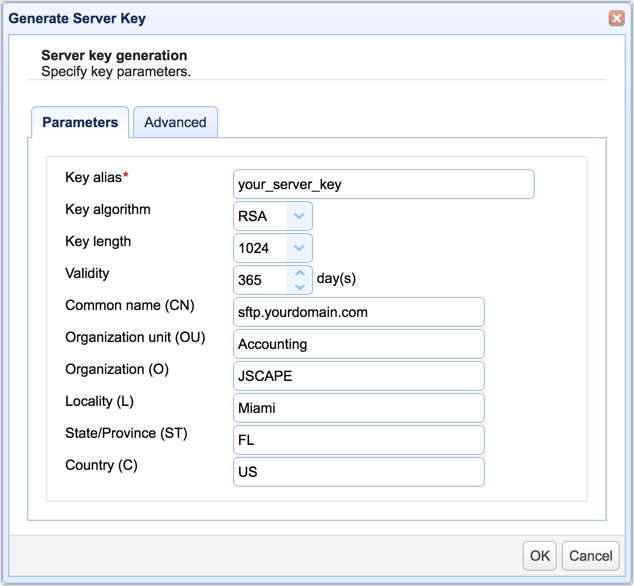
Two ways to generate an SFTP private key
One of the major security features of SSH FTP is public key authentication. This authentication method allows JSCAPE MFT Server to verify…
Learn More
-

Monitoring a remote SFTP server for newly added files
Most users of JSCAPE MFT Server are already familiar with directory monitors. You often use it to monitor a directory for newly…
Learn More
-

How to automatically transfer files from SFTP to azure blob storage via network storage
Let’s say you have trading partners who can only transfer files to you via SFTP. Incidentally, you also happen to have an…
Learn More
-

What Is HMAC (Hash-based message authentication code), And How Does It Secure File Transfers?
An Overview of HMAC Data integrity checks are vital to secure communications. They enable communicating parties to verify the integrity and authenticity…
Learn More
-

Active vs. passive FTP simplified
dropdown#toggle” data-dropdown-placement-param=”top” data-term-id=”295410482″>File Transfer Protocol (FTP) server runs behind a dropdown#toggle” data-dropdown-placement-param=”top” data-term-id=”295410497″>router, your users may sometimes encounter connectivity issues. One of…
Learn More
-

How to install an SFTP server on windows
Because Microsoft Windows doesn’t have a secure file transfer protocol server built in, we’ve put together a simple and easy-to-follow tutorial on…
Learn More
-
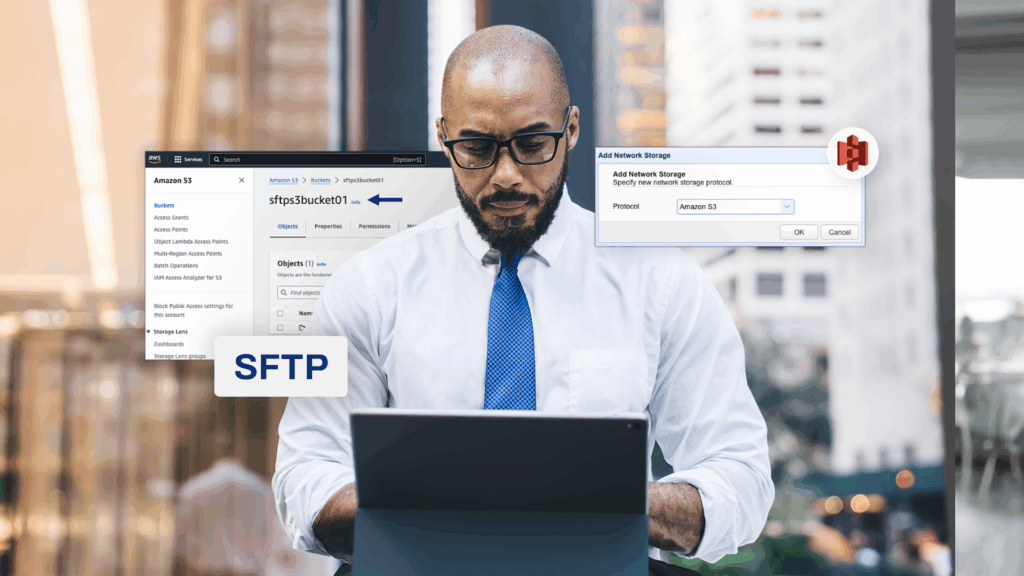
How to configure an SFTP-to-S3 file transfer
Many businesses use Secure File Transfer Protocol (SFTP) to transfer data between business units or to trading partners. With the growing adoption…
Learn More
-

Install A Linux SFTP Server Via Command Line And Configure Via Web UI
Overview Let’s say you want to install an SSH FTP server (SFTP) on a Linux machine devoid of a GUI. However, after…
Learn More
-

What port does SFTP use?
SFTP uses port number 22 by default, facilitating secure data movement over a single internet connection. This SFTP port assignment allows SFTP…
Learn More
-

How to monitor SFTP directories & download files
In this tutorial, we’re going to show you how to monitor directories on a remote SFTP server and then download any new…
Learn More
-

Why and How You Should Verify An SSH/SFTP Client Key’s Fingerprint Before Using It
In one of our previous posts, we talked about the importance of authenticating an SFTP host before logging into it and how…
Learn More
-

Understanding key differences between FTP, FTPS and SFTP
When it comes to moving files across networks, not many protocols are as established as File Transfer Protocol (FTP), File Transfer Protocol…
Learn More
-

How to use windows SMB share as network storage
When a user uploads files via FTP/S, SFTP, HTTP/S, or any supported file transfer protocol to JSCAPE MFT Server, those files don’t…
Learn More
-

How to test SFTP connectivity to remote hosts
Let’s say you’re trying to connect with a remote SFTP host, perhaps one of your own SFTP servers or one owned by…
Learn More
-

How to address the IT skills gap in manufacturing
While the IT skills gap is sometimes exaggerated, there are some industries where the tech talent shortage is really a major issue.…
Learn More
-
Using a remote SFTP service as network storage for your MFT server
JSCAPE MFT Server’s Network Storage module (formerly known as Reverse Proxy) allows you to utilize various remote services and storage solutions as…
Learn More
-

How to set up an SFTP reverse proxy in JSCAPE MFT gateway
Overview An SFTP reverse proxy adds another layer of security to SFTP services. In addition to SFTP’s ability to encrypt data in…
Learn More
-

Preparing trading partner servers for SFTP automation
Overview In order to keep transactions secure, you and your trading partners likely use SFTP and other encrypted protocols for your automated…
Learn More
-
Setting SFTP algorithms on your SFTP server
Overview In this post, we’ll discuss the algorithms in a typical SFTP server and explain their basic functions. We’ll cover algorithms for…
Learn More
-
Guide on how to set up an SFTP server
Overview This post is for those of you who want to dive right into the steps of setting up a SFTP server.…
Learn More
-

What is FIPS compliance & should i enable it for file transfers?
JSCAPE MFT Server encrypted file transfer protocols like SFTP and those secured through TLS (e.g. HTTPS, FTPS, AS2, OFTP, and WebDAVS) can…
Learn More
-

How to set up an SFTP active-active high availability cluster
The problem with using a single SFTP server Organizations in different industries like finance, healthcare and retail rely on an SFTP server…
Learn More
-

How to set up an SFTP Active-Passive cluster
This post was originally published on September 17, 2016 but was updated and republished on September 28, 2018. Overview In this quick…
Learn More
-

How to fetch files from multiple SFTP servers and then send to a trading partner
Learn how to configure JSCAPE MFT Server to fetch files from multiple SFTP servers and then send those files to a trading…
Learn More
-
Check whether specified date is a holiday
This custom trigger function checks to see if the supplied date matches against a list of holidays in defined input file. Two…
Learn More
-

Should we start using 4096 bit RSA keys?
Theoretically, RSA keys that are 2048 bits long should be good until 2030. If so, isn’t it a bit early to start…
Learn More
-

Video: Monitoring a directory for new files and automatically uploading to a SFTP server
Demonstrates how to configure JSCAPE MFT Server so that it monitors a directory for newly added files and then upload each file…
Learn More
-

Video: how to setup an SFTP server with JSCAPE
In this video, you’ll learn how to set up server and client keys on your SFTP server. This will enable your SFTP…
Learn More
-

Video: install an SFTP server on windows with JSCAPE MFT server
Learn how to install an SFTP Server on Windows with JSCAPE MFT Server in this video tutorial.
Learn More
-

Video: how to automatically forward files from FTP to SFTP
In this video tutorial, we’ll show you how to automatically forward FTP uploads to an SFTP server.
Learn More
-

How to setup public key authentication on an SFTP server
In today’s video we’ll teach you how to set up SFTP public key authentication on JSCAPE MFT Server. Public key authentication allows…
Learn More
-

Video: using an SFTP client on windows, mac, & linux
In this video, you’ll learn how to use SFTP on AnyClient. In addition to SFTP, AnyClient also supports other file transfer protocols…
Learn More
-

New video: creating a SFTP reverse proxy on JSCAPE MFT server
Last month, we published the article entitled “How To Set Up A SFTP Reverse Proxy On JSCAPE MFT Server“. That post attracted…
Learn More
-

How to set up a SFTP reverse proxy on JSCAPE MFT server
Overview JSCAPE MFT Server has a reverse proxy feature that allows you to map it to a user’s or group’s virtual path.…
Learn More
-

Top 5 FTP alternatives for businesses
Overview In our last post, we talked about the importance of applying the CIA Triad to enterprise file transfers. Interestingly, one of…
Learn More
-

Applying the CIA triad to your enterprise file transfer
Overview As one of the basic building blocks of information security, the CIA Triad is likewise a vital piece in establishing secure…
Learn More
-

The SSH/SFTP key fingerprint and its role in server authentication
When users attempt to connect to your Secure File Transfer Protocol (SFTP) server for the first time, they’ll see an alert indicating…
Learn More
-

How to automate SFTP downloads on the MFT server
Overview An automated SFTP download is one of the most efficient ways of downloading data from a remote server over a secure,…
Learn More
Browse by category
-
(23)
-
(43)
-
(7)
-
(37)
-
(57)
-
(40)
-
(19)
-
(622)
-
(3)
-
(390)
-
(106)
-
(5)
-
(19)
-
(199)
-
(22)
-
(86)