Why Your Business Needs an SSH Secure File Transfer Client

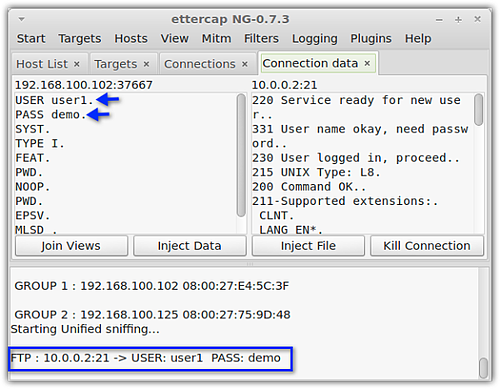
Once the crooks have obtained our login credentials, they can just simply login to our FTP server and grab whatever files they find.
To know more about sniffing, man-in-the-middle attacks, how such attacks are carried out, and how encrypted file transfers defeat them, read the article Countering Packet Sniffers Using Encrypted FTP.
What SFTP does
SFTP a.k.a. Secure File Transfer Protocol a.k.a. SSH File Transfer Protocol protects file transfers from various threats. It does this in two ways:
1. It encrypts the file transfer connection and
2. It provides stronger authentication
SFTP encryption
Encryption renders data unreadable. The data can only be made readable again after it has been decrypted. In an SSH file transfer, data is encrypted throughout the SSH connection. Decryption is done at both ends, i.e., at the server and at the client.
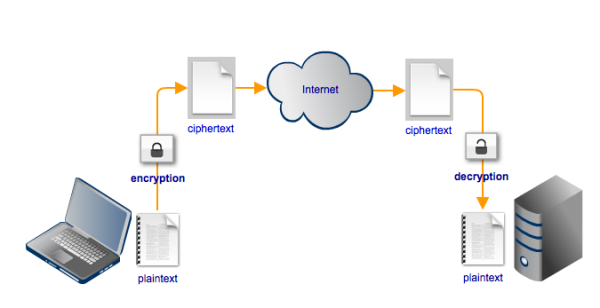
Thus, any attempt to eavesdrop on an SFTP file transfer using a man-in-the-middle attack will not succeed.
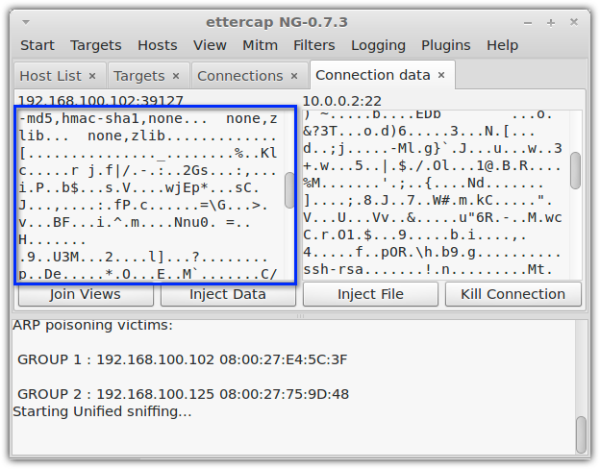
Here’s a screenshot of the same hacking tool shown earlier, this time displaying an attempt to eavesdrop on an SFTP connection. Notice how the transmitted data is no longer comprehensible.
SFTP authentication
To authenticate users connecting to the server, file transfer methods like FTP only require a username and password. Now we all know just how easy it is to obtain those login credentials using a packet sniffer. But if the connection is encrypted, then those login credentials are already safe, right? Wrong.
There are many sinister ways of obtaining passwords.
Crooks can perform various social engineering acts like shoulder surfing, phishing, or simply impersonating a legit user and calling a gullible Help Desk agent. More technically skilled individuals can even carry out a brute force attack on the server itself and steal a bunch of usernames and passwords.
SFTP can make things more difficult for them crooks. That’s because an SFTP server can apply two methods of authentication. The first one asks for something only the user is supposed to know: the user’s username and password. And the second one asks for something only the user is supposed to have: the user’s private key.
This second method, known as public key authentication, enhances the authentication process quite considerably. Even if an attacker is able to obtain a user’s login credentials, he won’t be able to login without the user’s private key.
The article Roles of Server and Client Keys in Secure File Transfers offers a very informative discussion on public key encryption and authentication.
The role of a SSH secure file transfer client
In order to upload or download files to/from a SFTP server, you would of course need a SFTP client or SSH secure file transfer client.
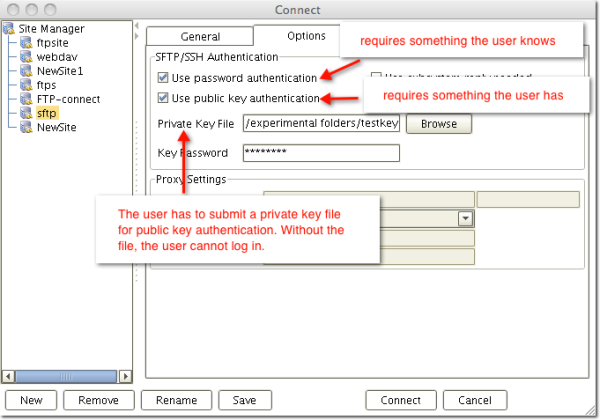
A SSH secure file transfer client typically supports not only SSH encryption but also public key authentication. In other words, it normally provides the option for attaching a private key file. In the SFTP client shown below, the user can enable password authentication, public key authentication, or both.
Considerations for Choosing a Secure File Transfer Client for Your Business
When choosing a SFTP client, it would be wise to pick a product that readily supports other secure file transfer protocols. That way, you could also use it to connect to other file transfer servers like FTPS, WebDAV, Amazon S3, and others.
Another consideration is support for the operating systems running on your users’ computers. If your SSH secure file transfer client only runs on Windows, users who work on Mac or Linux machines would be left out.
That means, your Network Administrator won’t be able to upload from his Linux desktop. Or, worse, your boss (who's out of town) won’t be able to download a financial report unto his MacBook Air.
Download a FREE SFTP Client
AnyClient is a free, platform-independent SSH secure file transfer client that runs on Windows, OS X, Linux, and Solaris. It supports a wide range of fast and secure file transfer protocols, including FTPS, SFTP, WebDAV/S, Amazon S3 and AFTP. Still using FTP? Yes, AnyClient supports that as well.