SFTP Client Connection Issues Involving Diffie-Hellman-Group1-SHA1

Overview
If you're running an SFTP service, chances are you've already received connectivity-related complaints involving the diffie-hellman-group1-sha1 key exchange algorithm. Here's how you fix that.
FileZilla can't connect to your SFTP server
We often hear this complaint from admins whose users are trying to connect through later versions of FileZilla. The specific error message they get goes like this:
Error: The first key exchange algorithm supported by the server is diffie-hellman-group1-sha1, which is no longer secure. Aborting connection.
Error: Could not connect to the server
Other SFTP client applications and SFTP servers acting as clients likewise generate similar error messages.
Where the problem lies
The error message gives us a hint. The problem lies in the SSH key exchange algorithm. During the SSH file transfer negotiation process, some SFTP servers recommend the Diffie-Hellman-Group1-SHA1 for the key exchange. Unfortunately, FileZilla has stopped supporting this particular algorithm due to vulnerability issues. Because the two (client and server) cannot negotiate a key exchange method, no connection is established.
Certain elements in the Diffie Hellman key exchange algorithm can have vulnerabilities. In this particular case, the root of the problem is in the group being used, i.e., Group 1. Each DH group corresponds to a bit length, which determines the key's strength to be used during the key exchange. The higher the bit length, the stronger. For example:
- Diffie-Hellman Group 1 uses 768-bit
- Diffie-Hellman Group 2 uses 1024-bit
- Diffie-Hellman group 14 uses 2048-bit
768-bit DH groups and even 1024-bit DH groups are vulnerable to precomputation attacks. Although these attacks require a great deal of processing power, the needed processing power is already considered within reach of nation-states and large cybercrime syndicates.
How to fix it
You have a couple of choices here:
1. Ask your users to use an older version of FileZilla or another SFTP client that still supports Diffie-Hellman-Group1-SHA1. We don't recommend this option. Since you're using SFTP, you value your data's security. Therefore, continuing to use any component that could undermine its security functions makes no sense.
or
2. Disable Diffie-Hellman-Group1-SHA1 on your server and only enable secure key exchange algorithms. If your server allows this, then this is the recommended option.
For those using the JSCAPE MFT Server, we recommend you upgrade to the latest version. Older versions of the JSCAPE MFT Server only support Diffie-Hellman-Group1-SHA1 and cannot accept other key exchange algorithms.
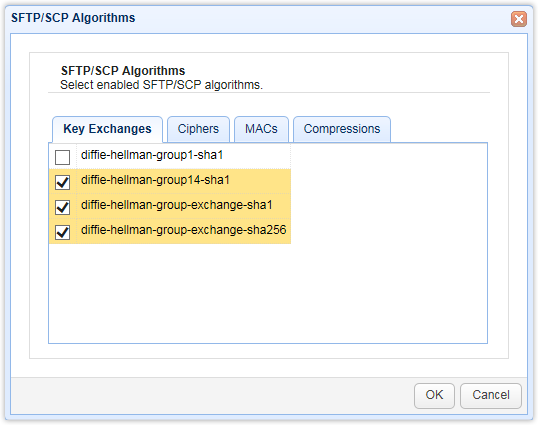
The latest version of JSCAPE MFT Server already supports multiple key exchange algorithms, including:
- diffie-hellman-group1-sha1
- diffie-hellman-group14-sha1
- diffie-hellman-group-exchange-sha1
- diffie-hellman-group-exchange-sha256
Note: For more information regarding diffie-hellman-group-exchange-sha1 and diffie-hellman-group-exchange-sha256, please refer to RFC 4419.
In addition, it offers the option to disable/enable algorithms. So, for example, you can choose to disable diffie-hellman-group1-sha1 and leave the rest enabled. You can do this by going to Services > SFTP/SCP tab > Algorithms > Key Exchanges tab.
Ensure your file transfers are secure and up to date. Schedule a free demo today to see how easy it is to maintain secure and efficient file transfers.
Why not just select the strongest DH group and leave out the rest?
Well, if only all computers were created equal, then this would be the logical solution. Alas, there are fast computers, and there are slow computers. As with cryptographic algorithms, a stronger DH group would require more processing power when generating keys. So, while higher diffie hellman groups can provide better security, the trade-off would be a drop in processing speed.
If you're using JSCAPE MFT Server and your users are experiencing the problem discussed above, you may download the latest version of JSCAPE MFT Server from here: