Note: This blog post was originally published on July 19, 2012 but was updated and republished on September 19, 2018
Overview
I’m now going to show you how to enable a reverse proxy service on JSCAPE MFT Gateway. By setting up a DMZ-based JSCAPE MFT Gateway to reverse proxy for one or more file transfer servers in your internal network, you can employ DMZ streaming. This will allow you to provide trading partners and other external users access to your sensitive data without placing the data on any DMZ-based server.
When used with multiple file transfer servers, the Gateway can provide load balancing as well. But that belongs to another post. To learn more about load balancing with JSCAPE MFT Gateway read the article Load Balancing File Transfer Services.
While the instructions on this article can apply to any TCP/IP service, my example will be of an FTP service running on JSCAPE MFT Server.
If you’re not yet familiar with the benefits of using a reverse proxy and DMZ streaming, I suggest you read the article Using a Reverse Proxy to Keep Sensitive Data out of the DMZ first. There you’ll learn more about the risks of storing data in the DMZ, the laws and regulations impacting data storage in the DMZ, and how a reverse proxy can help you achieve regulatory compliance. You might also want to familiarize yourself with the 3 Crucial Components for Enterprise File Transfers.
But if you’re already familiar with all that, you may proceed to the next section.
Setting up an FTP reverse proxy using JSCAPE MFT Gateway
To give you an idea how my IP addresses are assigned, here’s the network configuration in my lab. Notice how my client and file transfer server belong to separate networks. Notice also that my JSCAPE MFT Gateway machine has two NICs; one for each network. The client connects to 192.168.101.101, and JSCAPE MFT Gateway connects to JSCAPE MFT Server 1 through 192.168.100.104.
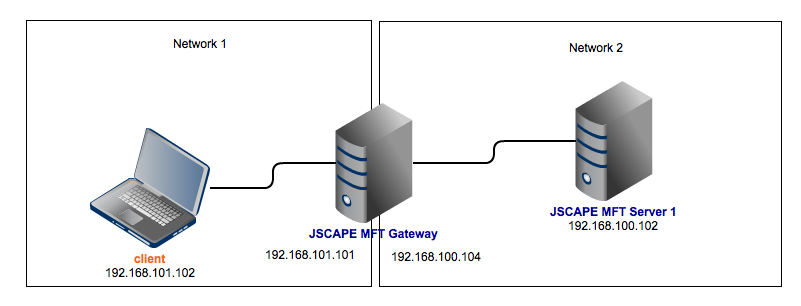
This is just a very simplified set up. A reverse proxy running in a production environment is usually deployed inside a DMZ, alongside one or two firewalls.
OK, let’s get started.
To begin, fire up the FTP service on your JSCAPE MFT Server and start JSCAPE MFT Gateway. Next, launch your favorite Web browser and login to MFT Gateway via the JSCAPE MFT Gateway Manager by entering MFT Gateway’s IP address and port number into your browser. See the documentation for more details.
The first thing we would like to do is add an FTP service to this reverse proxy. This is the FTP service the client will be connecting to. To set up the FTP service, go to the Services section of your JSCAPE MFT Gateway Manager and click the Add button.
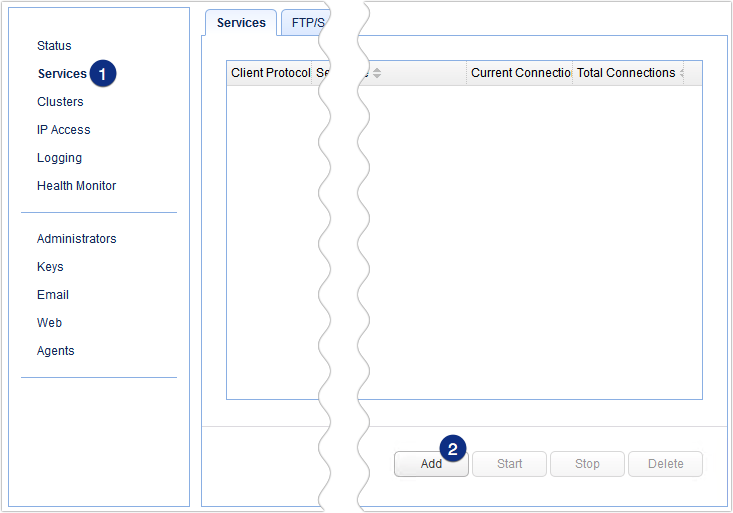
MFT Gateway supports a variety of reverse proxy configurations. Clients may connect using a protocol similar to or different from the protocol of the back-end server. For example, FTP-FTPS, FTP-SFTP, TCP(SSL)-TCP, and so on. For a complete list of supported client and server protocols, read this page in the online documentation.
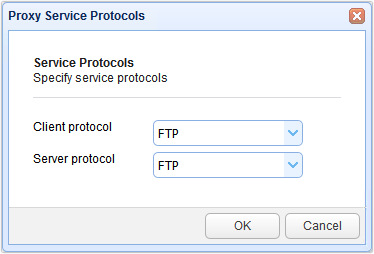
In our case, we simply want to set up a reverse proxy service that would allow FTP clients to connect to a FTP server. In the succeeding screen, select FTP from the Client protocol drop-down list and then FTP again for the Server protocol drop-down list.
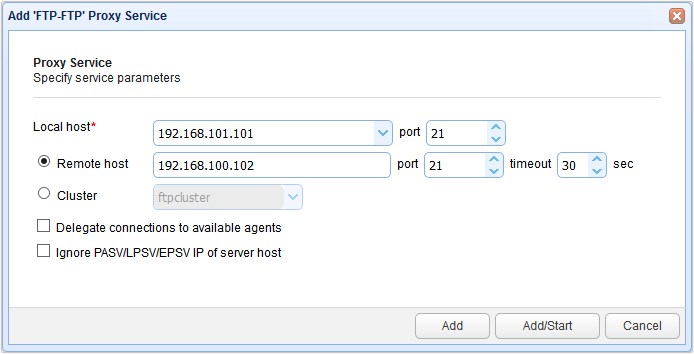
You’ll then be asked to specify the proxy service parameters. From the Local Host drop-down list, select the IP address of the NIC your client will be connecting to. In my case, that would be 192.168.101.101. Enter the Local port number of the service. Since this is a regular FTP service, we just enter 21.
Next, enter the IP address of the Remote host. In a production environment, this is would be the IP address of the file transfer server found in your internal network. In my case that would be 192.168.100.102. Also enter the Remote port number. Click Add or Add/Start (if you want to start the proxy service right now).
You’ll then be brought back to the main screen where you should see your newly added FTP revere proxy service.
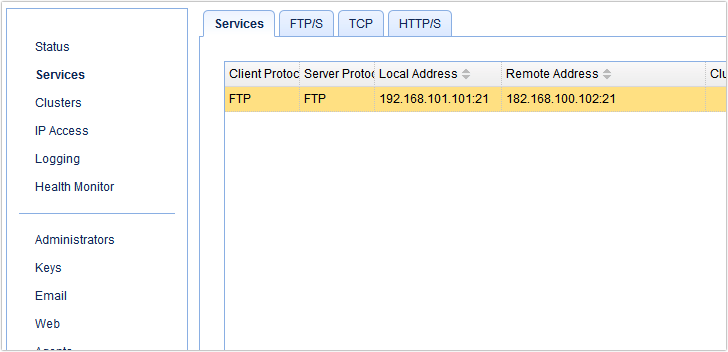
That’s it! That’s how easy it is to set up an FTP proxy using JSCAPE MFT Gateway. Anyone with the right credentials to the server in your internal network can now use an FTP client to connect to this FTP service just like he would with a regular FTP server. Notice there’s no need to set up user credentials on the reverse proxy!
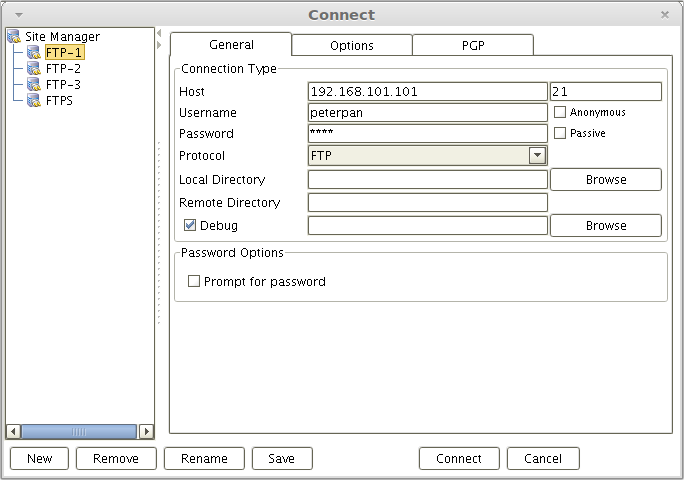
Here’s how I connect using AnyClient.
Request a risk-free JSCAPE trial
You just learned a safer way of providing file transfer services to your clients and trading partners without putting any data in your DMZ. Regulatory compliance is easily achieved with JSCAPE MFT Gateway’s reverse proxy feature and DMZ streaming.
Test it in your own environment when you request a risk-free trial here.





