Overview
The volume of sensitive information being exchanged among large organizations is growing at a tremendous pace. Unless these organizations beef up IT security, all that information could easily fall into the wrong hands. In this post, we take a look at three security solutions that are emerging as the most crucial components of highly secure, enterprise-class file transfers.

1. The Firewall
A firewall is your network’s first line of defense against external threats. If your network’s connected to the Internet, most of the threats will be coming from there. A firewall provides security by allowing limited access from the Internet to your network based on rules you specify.
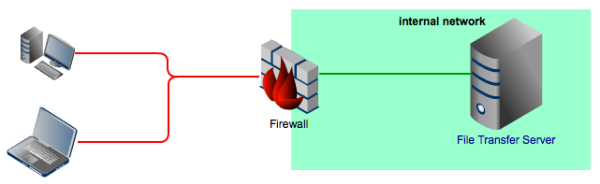
Basically, you can specify which connections between external clients and your servers should be ALLOWED or DENIED. Some firewalls are initially set to ALLOW ALL and then you’re required to specify which connections should be denied. Others, on the other hand, are instead set to DENY ALL. In which case, you would have to specify which connections should be allowed.
Being the more conservative option, the second one can provide better security.
Assuming you have a firewall initially set to DENY ALL, you would need to specify the following:
- Services (represented by ports) from within your network which you want external hosts to access,
- IP addresses/hostnames of hosts in your network providing those services, and
- (optionally) IP addresses/hostnames of external hosts whose inbound traffic you want to allow.
But how exactly can firewalls secure enterprise file transfers?
- Firewalls can limit requests directed at your file transfer servers to only those that are requesting file transfer services.
- Firewalls can limit connections only to those that use secure file transfer protocols (e.g. FTPS, SFTP).
- Firewalls can prevent unauthorized IP addresses from connecting at all.
- If a protocol requires multiple open ports (e.g. passive FTP), a firewall can be set to limit the number of open ports to a narrow range, thereby reducing the risk.
While firewalls provide protection by controlling traffic to your file transfer servers, sometimes you would have to implement security measures on the servers themselves. In this case, you would need the second component in this list.
2. The Managed File Transfer Server
Managed File Transfer (MFT) servers are network solutions purposefully designed for scalable, multi-protocol, automated, and highly secure file transfers. Ideally, an MFT server should be able to support a wide range of traditional file transfer protocols like FTP, FTPS, SFTP, HTTP and HTTPS as well as UDP file transfer protocols like AFTP (Accelerated File Transfer Protocol).
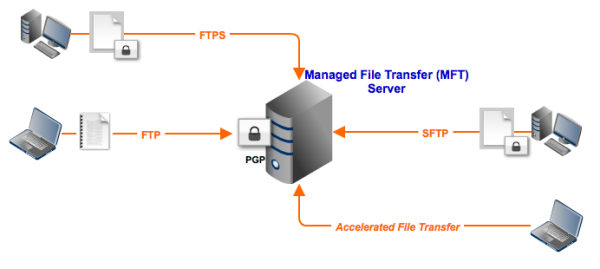
As the word “Managed” suggests, a Managed File Transfer server is capable of automating tasks common in file transfer server administration. In JSCAPE MFT Server, for instance, a variety of tasks are automated using triggers. This would allow you to schedule large file transfers during after-office hours, scan files as they are uploaded, or PGP-encrypt certain files — all without any human intervention.
For some businesses, a firewall and an MFT server should be enough to ensure secure file transfers. But for other businesses, a third component is needed.
3. The Reverse Proxy
Enterprises governed by certain regulations or standards have more stringent requirements when it comes to file transfers. For example, because businesses covered by PCI-DSS are not allowed to store credit card information in their DMZs, these businesses have a need for a network solution that would enable them to share files with trading partners without placing file transfer servers in the DMZ.
The best solution? A reverse proxy. A reverse proxy is a proxy server that can accept requests from external clients in behalf of servers (e.g. file transfer servers) stationed behind it.
To the clients, the reverse proxy is the file transfer server. But in reality, none of the files clients download from a reverse proxy really originate from the proxy. Rather, they are still stored in the file transfer server(s) and are just streamed to the clients through the reverse proxy. In the case of JSCAPE MFT Gateway, this is known as DMZ streaming.
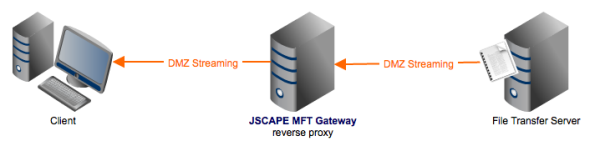
If the reverse proxy is placed in the company’s DMZ and the file transfer server in the company’s internal network, the PCI-DSS requirement is met.
All three components mentioned here can be combined to produce a network configuration ideal for enterprise file transfers.
An ideal setup for enterprise file transfers
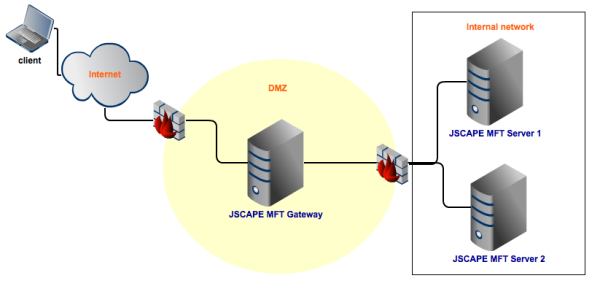
In the figure above, the reverse proxy (JSCAPE MFT Gateway) is placed in the DMZ. It accepts file transfer requests from clients on the Internet. To make sure that only legitimate requests reach the proxy (e.g. trusted source IP address, allowed protocol, etc.) and that all legitimate incoming traffic pass through the proxy, a firewall is placed right in front of it.
Another firewall is placed behind the reverse proxy. The function of this second firewall is to make sure that only requests from the reverse proxy make it to the internal network and that all allowed connections from the reverse proxy are directed to the MFT servers (JSCAPE MFT Server 1 and 2).
There are two MFT Servers because reverse proxies like JSCAPE MFT Gateway can support load balancing. But then that’s for another post.
Summary
In this article, we talked about three very important network security solutions: the firewall, the MFT server, and the reverse proxy. You can combine all three to set up a highly secure environment for enterprise file transfers.





