In one of our previous posts, we talked about the importance of authenticating an SFTP host before logging into it and how to use the host’s RSA key fingerprint to carry out the authentication. The same principle applies when you import a user’s client key for public key authentication. If you’d like to walk through it with an expert, request a free trial.
Before a user (or client application) can ever login to your SFTP server via public key authentication, you first need to either A) generate a client key and then assign that key to the user’s user account on your server or B) import that user’s SFTP key. The key to be imported should be the public key of a public-private key pair. In JSCAPE MFT Server, you would import that public key into the Client Keys module (Keys > Client Keys > Import).
Note: In this post, we’re more concerned with keys that are imported into your server rather than keys that are generated on the server.
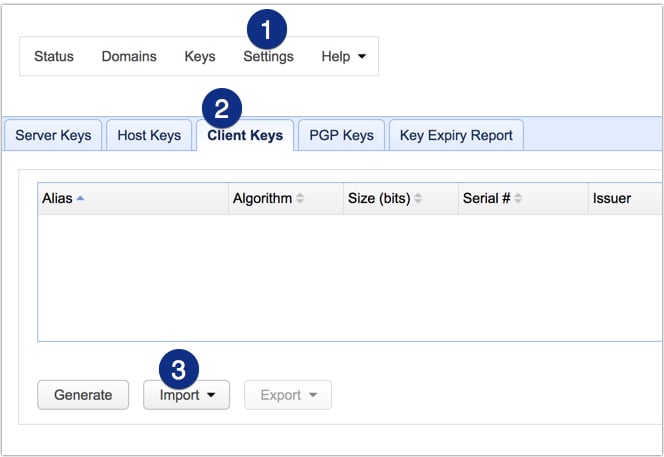
Once imported, the key can then be associated with an existing user account. Only then can the user use the corresponding private key at his/her end to perform public key authentication.
Before you ever get to that part (i.e. the user logging in via public key authentication), there’s one task, as a server admin, that you need to accomplish first. You need to first verify whether the client key you just imported actually belongs to a legitimate user. For all you know, that client key you just received via email might have come from a spoofed email account or a bogus user.
If that happens, you would be granting server access to an unauthorized user. Of course, that user will likely not have any administrative privileges and would only have access to folders you have assigned to him/her. However, if one of those folders happens to be a shared with a legitimate user and that legit user uploads sensitive data into that folder, you could have a data breach in your hands.
So, how do you verify an SFTP client key? Well, as with host keys, the easiest and most reliable way is to compare fingerprints.
On JSCAPE MFT Server you can view the fingerprint of an imported client key by selecting the key in the Client Keys tab and then clicking View.
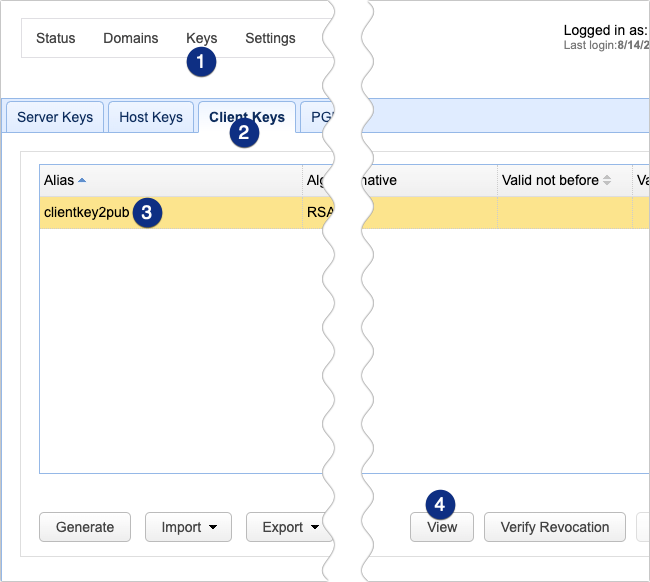
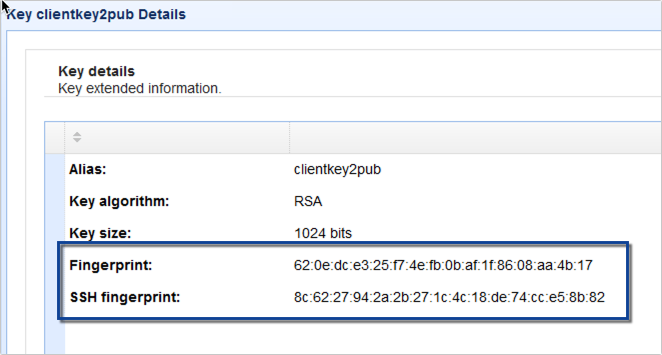
The fingerprint should then be displayed alongside the other key details. There are two versions of fingerprints. The first one is based on ASN.1 public key encoding, while the second one is based on OpenSSH MD5 hash.
You may also view the second (OpenSSH) fingerprint by running the ssh-keygen tool from the command line on the public key file likeso:
ssh-keygen -l -E md5 -f ./filenameofpublic key file
For example:
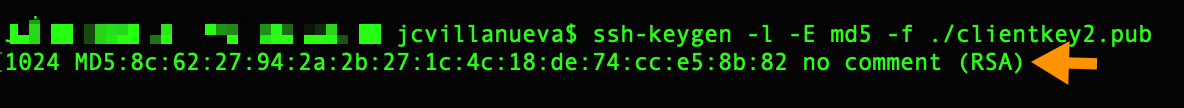
Users can use this method to view the fingerprint of their copy of that public key file. So, basically, you can call the user, ask them to view the fingerprint of their public key and compare the value with what you have. If the two values match, then you’re looking at the same public key.
That’s it. Now you know how to verify an SFTP client key’s fingerprint.
Related content
The SSH / SFTP Key Fingerprint And Its Role In Server Authentication
Setting Up SFTP Public Key Authentication On The Command Line
Fixing SSH/SFTP client connection issues involving Diffie-Hellman-Group1-SHA1





