Files you upload to an Amazon S3 trading partner through JSCAPE MFT Server are normally stored in plaintext. If you want to encrypt those files to minimize the risk of a data breach, one way to do that is by using the AWS Key Management Service or AWS KMS. We’ll show you how to use this particular service in this post.
Watch the video
Would you prefer to watch a video version of this tutorial instead? You can play the video below. Otherwise, just skip it if you wish to continue reading.
Note that there are costs associated with the AWS KMS service, so I suggest you read this page on the AWS website first.
Alright. The first thing you need to do is to create a customer master key or CMK. You can create this key through either the AWS KMS API or the AWS Management Console. We’ll be using the latter. Login to your AWS Management Console and go to the Key Management Service. If you haven’t used that service yet, the easiest way to find it is by simply typing it into the search box as shown in the screenshot below.
Pay attention to the region displayed at the upper-right corner of the screen. While you may change that region, just make sure it’s the same region you select in your JSCAPE MFT Server Amazon S3 trading partner object.
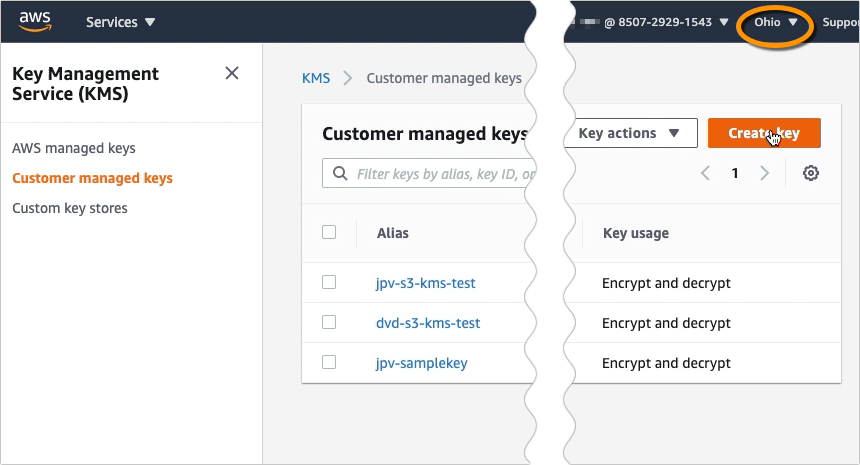
Click the Create key button to start creating your CMK. We’ll just be creating a very basic CMK, so if you want to know more about all the relevant concepts and advanced settings, I suggest you read the AWS KMS Developer Guide.
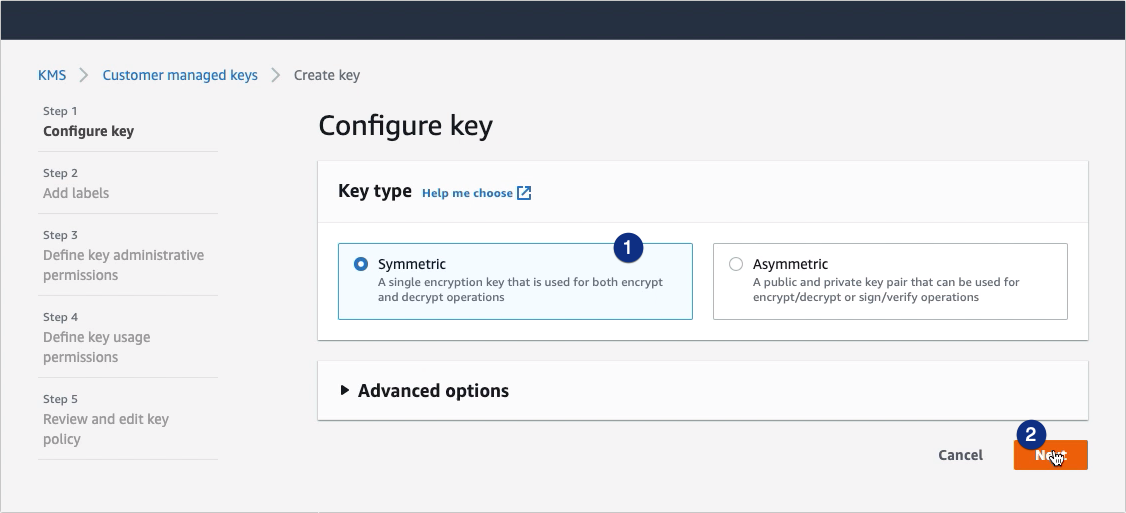
Select Symmetric and then click Next.
Recommended read: Symmetric vs Asymmetric Encryption
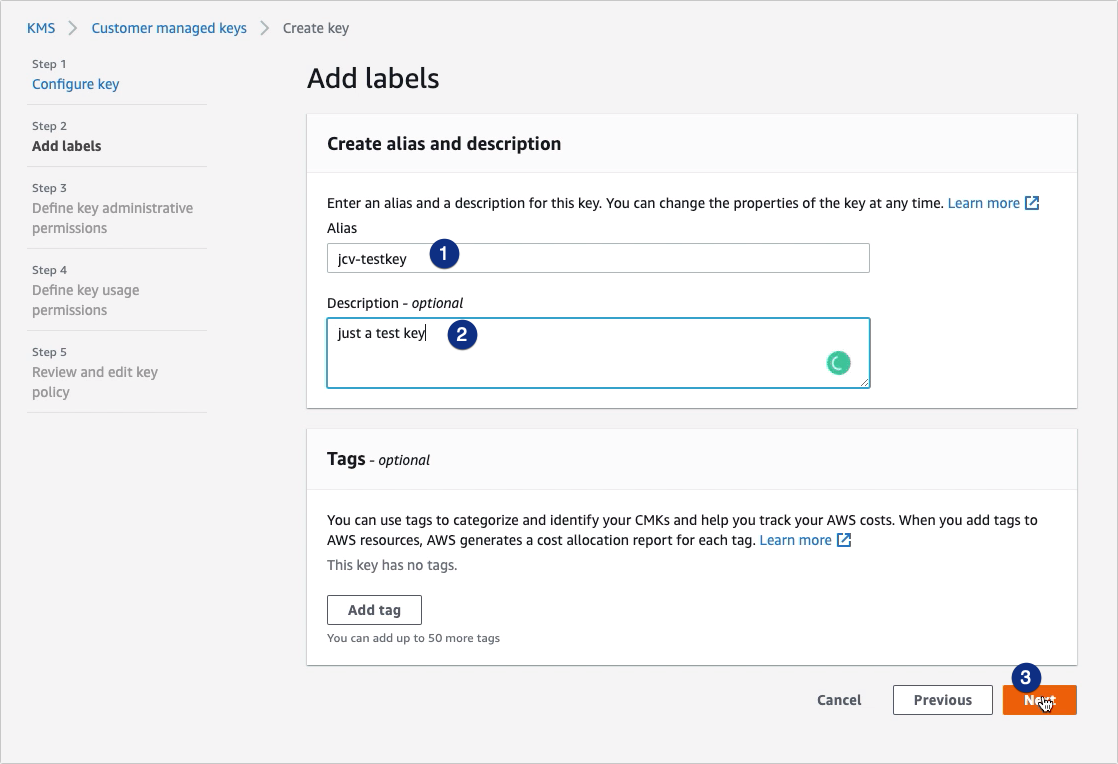
Enter an alias for this key. This is just an arbitrary human-friendly name you’ll be using to refer to this key here in the AWS environment and in your JSCAPE MFT Server Amazon S3 trading partner object.
You may also add a short description if you want. Click Next to proceed.
Next, select the IAM user who you want to administer this key. In my case, I’m just using my own user account.
After that, select the IAM user who you want to use this CMK in cryptographic operations. Again, I’m just choosing my own user account.
Click Next to proceed.
Lastly, click Finish to finalize the CMK creation process.
You should then see your newly created customer master key among your list of CMKs.
Want to try these steps in your own environment? Request a risk-free trial of JSCAPE here.
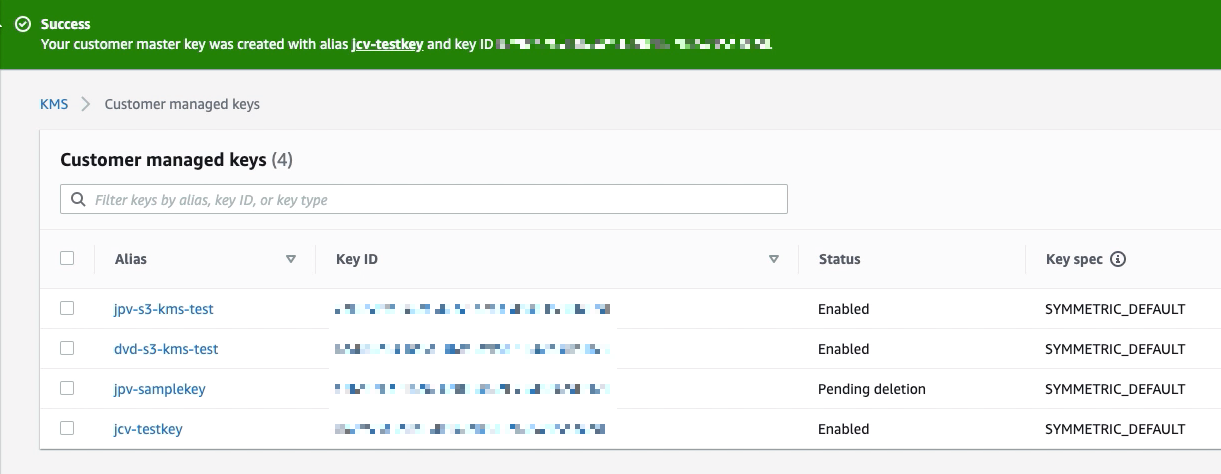
Now that you have your CMK ready, the next step is to assign that key to an Amazon S3 bucket. Go to the AWS S3 service

… and then click the bucket whose data you want to encrypt with AWS KMS.
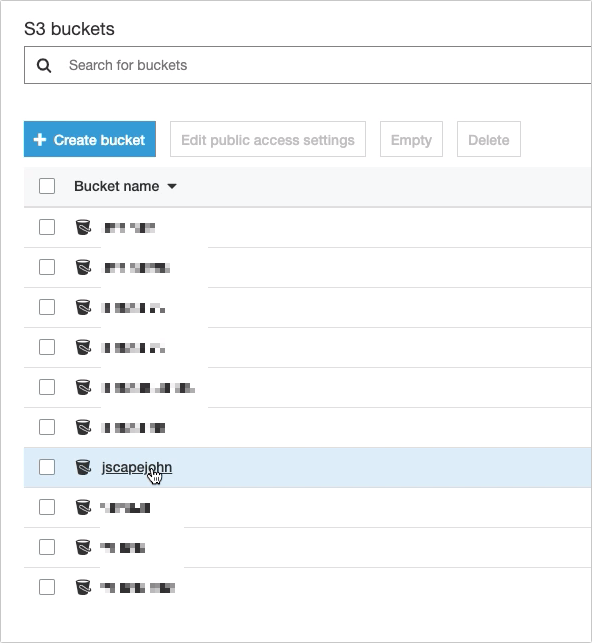
Navigate to the Default encryption section and then click the text at the bottom. Normally, that would be AES-256.
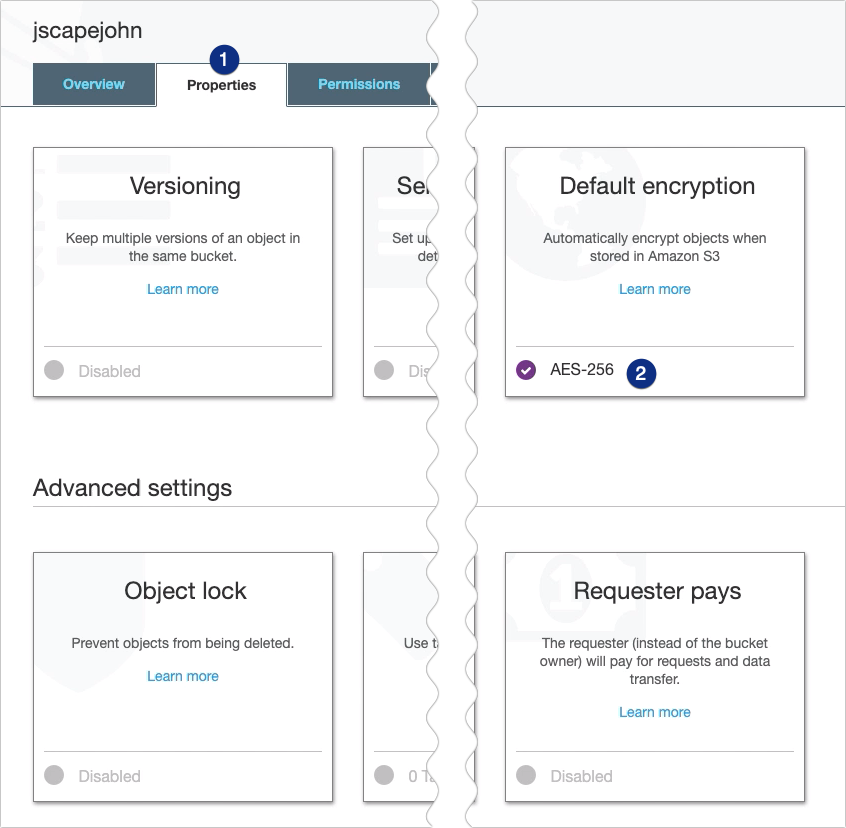
When the Default encryption dialog box pops up, select the AWS-KMS option and then click the alias of the CMK you created earlier. In my case, that would be ‘jcv-testkey‘.
Click Save to proceed.

The text at the bottom of the Default encryption section should now display AWS-KMS instead of AES-256.
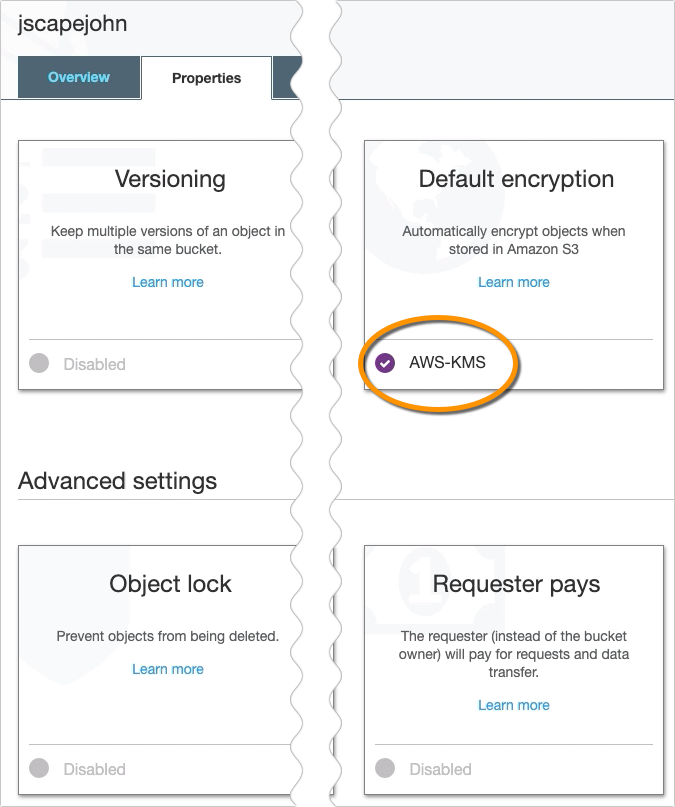
That’s all you need to do on the AWS Management Console. You may now proceed to your JSCAPE MFT Server instance and edit your Amazon S3 trading partner. In my case, the name of my S3 trading partner is ‘tp-s3’.
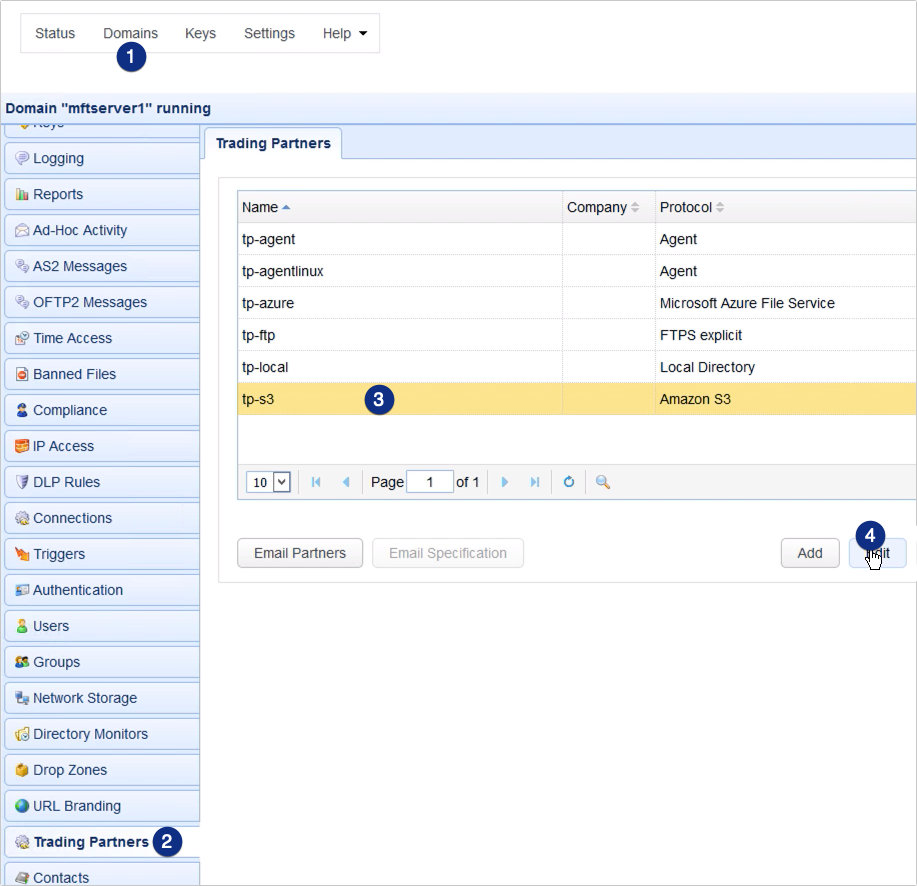
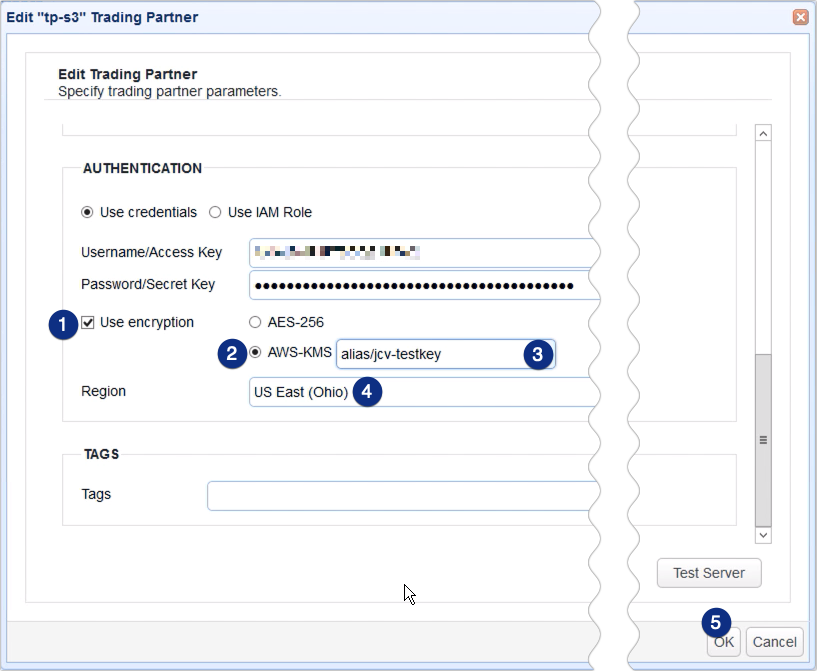
Once you’re inside your Amazon S3 trading partner parameters dialog, scroll down to the Authentication section. Make sure the Access Key ID of this S3 trading partner is the access key ID of the username you used in creating the CMK.
Tick the Use encryption check box and then select the region that matches the region displayed when you created your CMK. In my case, that would be US East (Ohio). After that, select the AWS-KMS option and expand the adjacent drop-down list. Click the alias of the CMK you created earlier and then click OK to apply the changes.
That’s all there is to it.
Before we end, let me just show you what happens when you upload a file to your AWS-KMS-protected Amazon S3 bucket from JSCAPE MFT Server.
What I have here is a trigger that uploads a file to my Amazon S3 bucket.
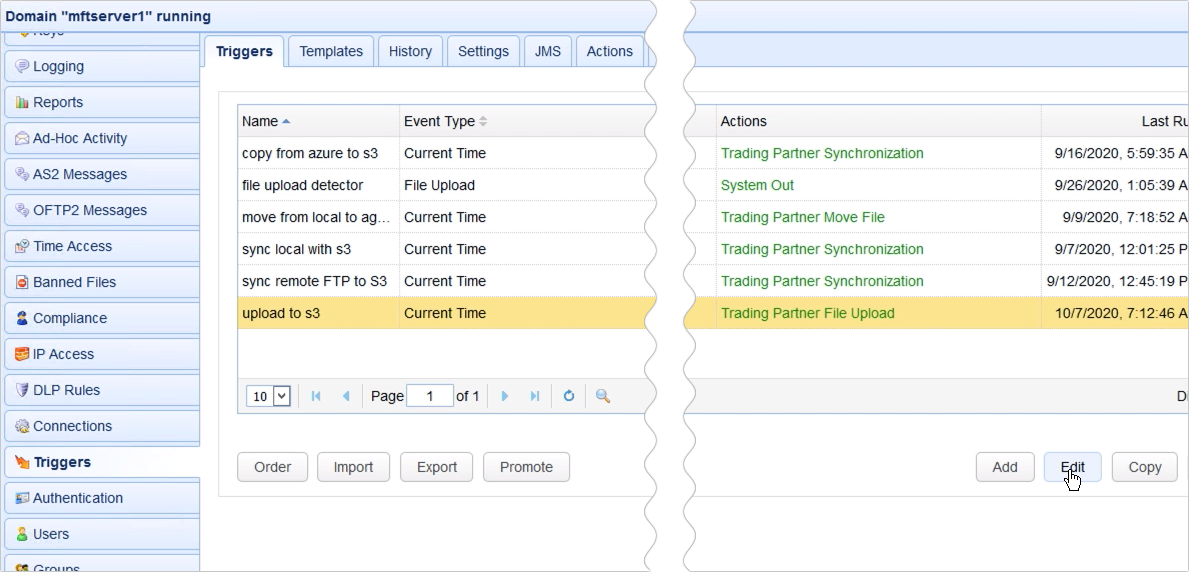
So, as you can see, the Partner setting is set to tp-s3, which is the name of my Amazon S3 trading partner object. The file this trigger is configured to upload is named file01.txt, and it’s going to be uploaded to the folder named ‘folder1’ under the S3 bucket named ‘jscapejohn’.

So, if I run this trigger…
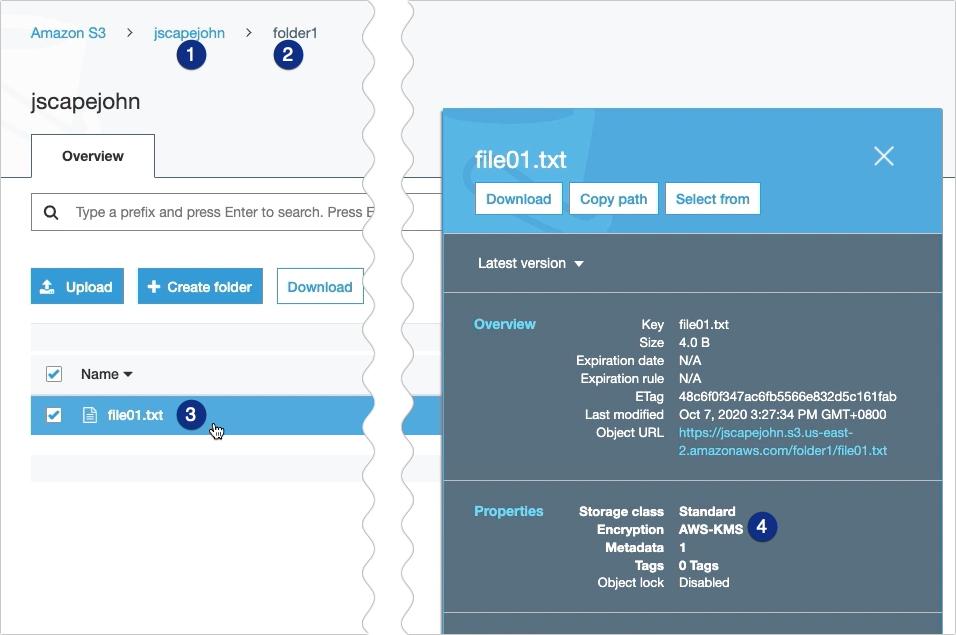
… and check inside the S3 bucket folder named folder1 through the AWS Management Console, I should see the newly uploaded file named file01.txt. If I click on that file and check its properties, I see that it has indeed been encrypted with AWS-KMS encryption.
That’s it. Now you know how to use AWS KMS to encrypt files uploaded to your S3 trading partner using JSCAPE MFT Server.
Get started
Get a JSCAPE free trial at no obligation. > Here’s the link < to request your trial experience.
Related content
How To Copy Data From Azure To AWS S3 | JSCAPE
How to Download Newly Added Files from an AWS S3 Folder
How To Schedule Automated File Uploads From Your Server To Box Cloud Storage
How To Use Amazon S3 As The File Storage System of Your MFT Server
Amazon S3 vs Local Storage – Where Should You Store Files Uploaded to Your File Transfer Server?





