Overview
In this post, we’ll discuss the algorithms in a typical SFTP server and explain their basic functions. We’ll cover algorithms for key exchanges, ciphers, MACs, and compressions. After that, we’ll dive into the JSCAPE MFT Server Manager Web GUI and show you where you can configure those SFTP algorithms.
Having a basic understanding of these algorithms and knowing where to configure them will enable you to strengthen your SFTP server’s security or troubleshoot certain client connection issues.
Note: SFTP runs on SSH, and the algorithms you’ll be setting are actually SSH algorithms.
What we’d like to do
Key exchanges, ciphers, MACs, and compressions
Whenever you send sensitive files over an insecure network like the Internet, you might want to make sure that:
1. Your data stays confidential throughout the transmission. You wouldn’t want valuable or sensitive information such as PII (personally identifiable information), trade secrets, customer lists, key employee salaries, marketing strategies, source codes, etc. to fall into the wrong hands.
2. Data integrity is upheld, i.e., it remains unchanged, or if ever it does undergo even the slightest accidental or intentional changes, that you have a way of knowing.
3. You are able to verify the authenticity of its source. You will want to make sure it came from the party you were expecting to be the sender (and not from an impostor).
That’s why SFTP is very suitable for transmitting sensitive files. It already comes with algorithms that help address these concerns.
For instance, to preserve confidentiality during transmission, SFTP provides data-in-motion encryption. The various algorithms used for this purpose are called ciphers.
To perform data integrity checks and discover possible modifications in the data, SFTP uses what are known as Message Authentication Codes or MACs. The algorithms designed for this security mechanism are aptly called MAC algorithms.
Like data integrity checks, authenticity checks are also carried out using MACs. So once again, the algorithms used in these kinds of tasks are the MAC algorithms.
In addition to those two algorithms already mentioned (i.e., ciphers and MAC algorithms), SFTP has two more that also play important roles in SFTP transmissions. They are the:
Compression algorithms – These are algorithms responsible for compressing files before transmission. Compression reduces the size of (compressible) files and, in turn, improves transmission times. Compression also adds another important benefit. It increases the data’s entropy, consequently making it more resistant to certain cryptanalysis attacks.
Key exchange algorithms – These algorithms are responsible for establishing secure exchange methods for the symmetric keys needed during encryption.
Basically, configuring these in your SFTP server entails going into the Algorithms module and selecting the algorithms you want to enable.
Then when a user connects to your server, that user’s SFTP client and your SFTP server will first negotiate which algorithms to use during the SFTP session. Whatever they arrive at would depend on the algorithms supported by the client and those algorithms you’ve enabled. If you haven’t enabled certain algorithms on the server and they’re the only algorithms the client supports, the client will have problems connecting.
So why, then, shouldn’t you enable all algorithms? The answer is this: certain algorithms are more secure than others. If you want your SFTP sessions to be highly secure, then you will have to force your sessions to employ only the most secure algorithms. We will compare algorithms in a future post, so stay tuned for that.
Remember, however, that in doing so, you may encounter interoperability issues with legacy SFTP clients (which understandably only support older, less secure algorithms). In other words, users with legacy SFTP clients might be unable to connect.
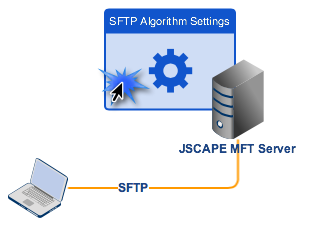
Now that you have a basic understanding of the various SFTP algorithms, it’s time to walk you through the process of setting them up on your SFTP server. Launch your JSCAPE MFT Server Manager now and follow the instructions below.
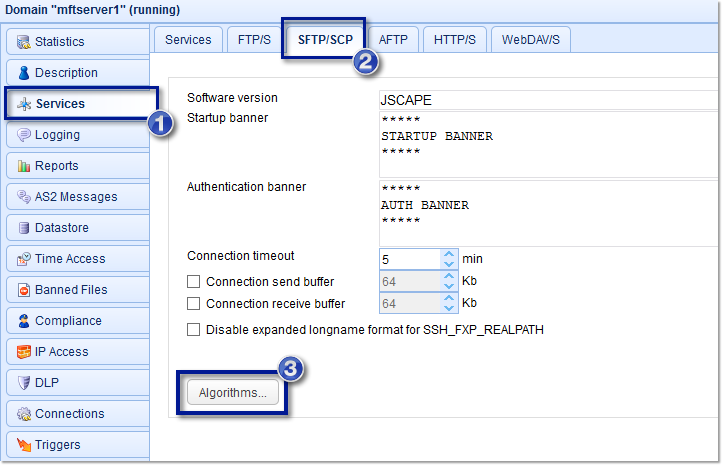
1. Open the Algorithms module.
To do that, go to the Services module, navigate to the SFTP/SCP tab, and then click the Algorithms button.
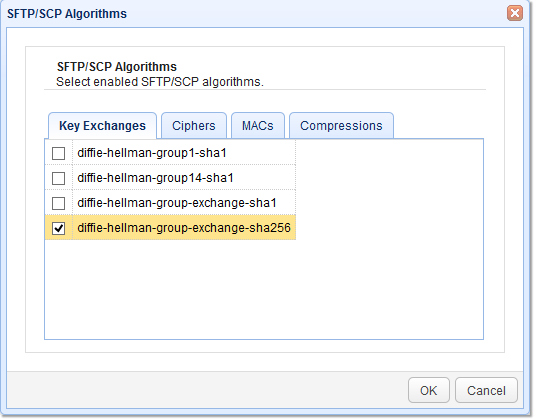
2. Select Key Exchange algorithms
The first set of algorithms you’ll be able to modify is the Key Exchanges algorithm. Some of the supported Key Exchange algorithms are the:
diffie-hellman-group1-sha1
diffie-hellman-group14-sha1
diffie-hellman-group-exchange-sha1
diffie-hellman-group-exchange-sha256
Tick the check box of the Key Exchange algorithm(s) you want to enable and then click the OK button.
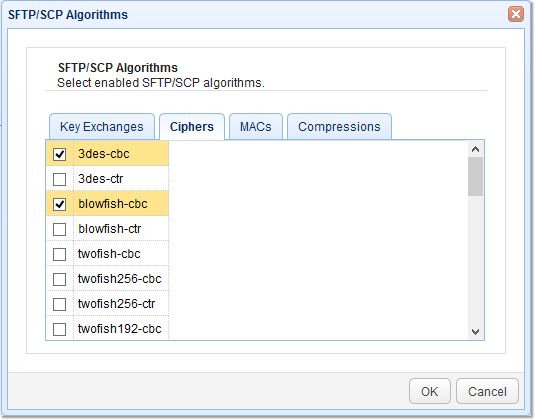
3. Select Ciphers
The next set of algorithms you may want to set are the ciphers. Some supported ciphers include the following:
| 3des-cbc | twofish192-cbc | aes128-ctr | idea-cbc |
| 3des-ctr | twofish192-ctr | serpent256-cbc | idea-ctr |
| blowfish-cbc | aes256-cbc | serpent256-ctr | cast128-cbc |
| blowfish-ctr | aes256-ctr | serpent192-cbc | cast128-ctr |
| twofish-cbc | aes192-cbc | serpent192-ctr | arcfour256 |
| twofish256-cbc | aes192-ctr | serpent128-cbc | arcfour128 |
| twofish256-ctr | aes128-cbc | serpent128-ctr | arcfour |
Tick the check box of the cipher you want to enable and then click the OK button.
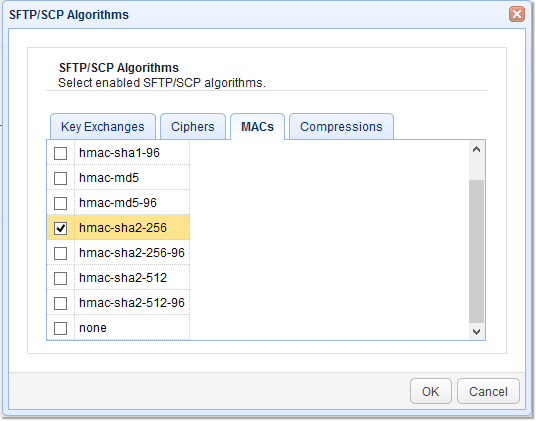
4. Select MAC algorithms
Some supported MACs include:
| hmac-sha1 | hmac-md5 | hmac-sha2-256 | hmac-sha2-512 |
| hmac-sha1-96 | hmac-md5-96 | hmac-sha2-256-96 | hmac-sha2-512-96 |
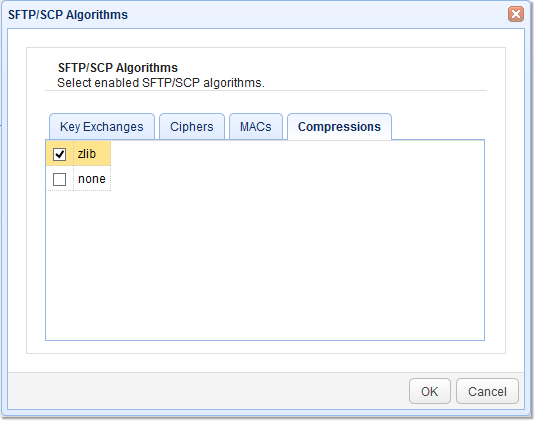
5. Select Compression algorithms
As of this writing, the supported compression is zlib, a widely used compression algorithm.
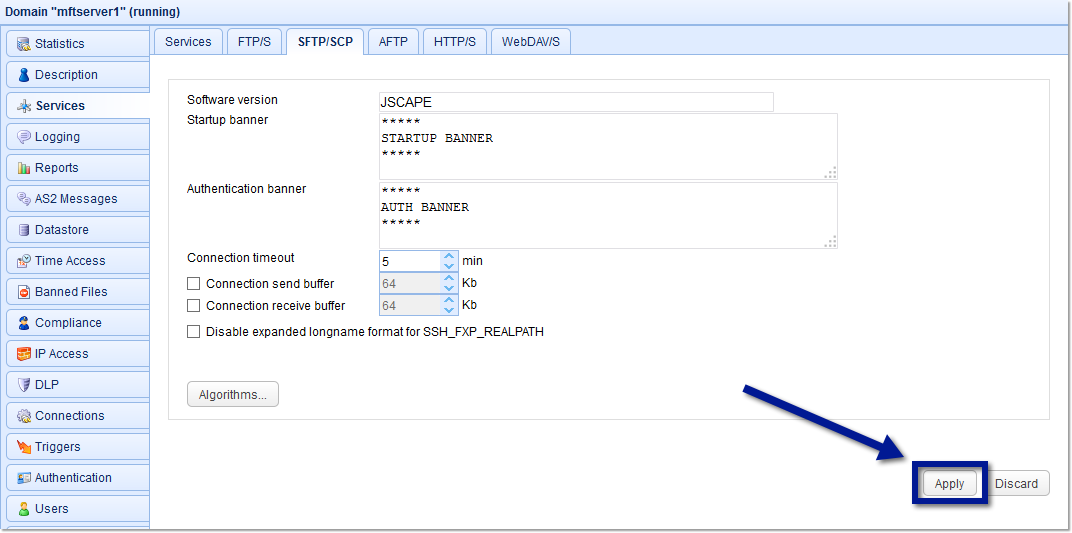
6. Apply the changes
As soon as you’re done making those changes and are back at the SFTP/SCP tab, click the Apply button.
That’s all there is to it! Interested in enhancing your SFTP server’s security with customized algorithms? Schedule a demoand see how easily you can optimize your file transfer security.
Other relevant articles you might find interesting
Using SFTP on the Command Line
Recommended download
Still haven’t tried JSCAPE MFT Server? Download the free evaluation edition now.
Download JSCAPE MFT Server Trial