Overview
Choosing a file transfer software might seem like a trivial exercise. Any application capable of delivering files to your intended recipient should fit the bill, right? Well, not all the time. If your company belongs to the healthcare or financial services industry, is publicly traded, or handles credit card information, then there are a couple of security requirements you need to take into consideration.
These requirements are mandated by laws and regulations that have stiff penalties for non-compliance, so it might be a good idea to know whether any of those laws apply to you. If there’s one that does, you might want to pick a file transfer software that would make it easier for you to achieve compliance. Let’s go over some of those laws now.
HIPAA
The Health Insurance Portability and Accountability Act or HIPAA covers certain organizations in the health care industry, including:
✔ Health plans (e.g. , Medical, Dental, and Vision Plans, HMOs, Medicare and Medicaid, most Long-Term Care Insurers, Veterans Health Plans, and certain Company Health Plans)
✔ Health care clearinghouses – These are companies who convert nonstandard health information into standard form or vice versa (e.g. billing services, repricing companies, value-added networks, and community health management information systems)
✔ Health care providers (e.g. doctors, clinics, dentists, nursing homes, pharmacies, psychologists and chiropractors) who transmit health information electronically.
There are two sets of provisions in HIPAA that could influence an organization’s choice of file transfer software. These are:
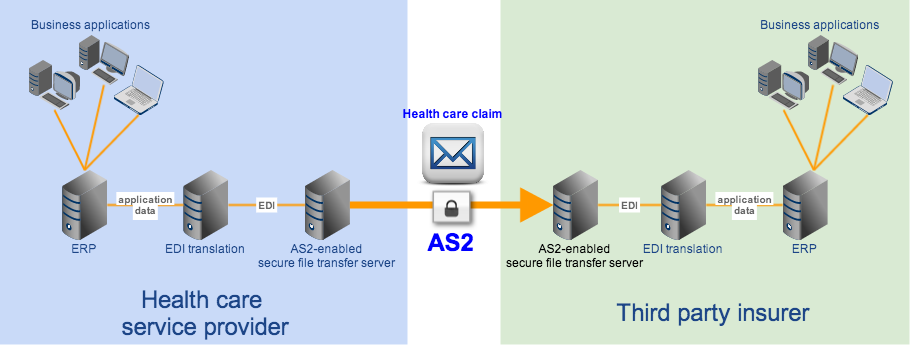
1) The Transactions Rule, which requires covered entities who perform certain electronic transactions to do them in a standardized way, e.g., through EDI or electronic data interchange. These transactions include: claims and encounter information, payment and remittance advice, claims status, eligibility, enrollment and disenrollment, referrals and authorizations, coordination of benefits and premium payment. Note that EDI usually involves automated server to server file transfers.
2) The Security Rule, which comes with a set of standards (known as Technical Safeguards) that aim to protect electronic Protected Health Information (ePHI). These standards include provisions for access controls, audit controls, encryption, data integrity, authentication, and transmission security. For a detailed discussion on HIPAA-compliant file transfers that focus on the Security Rule, read the Guide to HIPAA Compliant File Transfers.
So, if you need to comply with both the Transactions Rule and the Security Rule, your file transfer software must have built-in capability to:
1. Support automated, server-to-server transmissions and
2. Meet the necessary security standards.
One option would be to send out EDI messages through an AS2 server. AS2 is really designed for transmitting EDI messages in a secure manner. It already comes with a few security functions like encryption, authentication, and data integrity.
However, it is worth noting that there are also other security standards that have to be met (read Guide to HIPAA Compliant File Transfers – Part 2). Hence, it would be much better if you could find a file transfer server that supports not only automated transmissions but also the other security functions needed for achieving compliance.
GLBA
The GLBA or Gramm-Leach-Bliley Act is quite similar to HIPAA in that it’s designed to protect personally identifiable information. In HIPAA, such information is called PHI or protected health information. GLBA, on the other hand, refers to it as nonpublic personal information or NPI. Nonpublic personal information includes names, addresses, bank account numbers, phone numbers, credit histories, Social Security Numbers and other data that can be used to uniquely identify an individual.
While HIPAA covers organizations in the health care industry, GLBA governs financial institutions such as banks, loan brokers, debt collectors, non-bank mortgage lenders, real estate appraisers, and tax return preparers.
Another similarity with HIPAA – particularly in relation to covered entities and business associates – is that companies covered by the GLBA Safeguards Rule also need to make sure their affiliates and service providers likewise protect any nonpublic personal information that ends up in their hands.
Under the GLBA Safeguards Rule, financial institutions are required to inform consumers about their security plan. A security plan describes how a financial institution intends to secure the nonpublic personal information it obtains from consumers through transactions or through the services it performs. The presence of a plan naturally implies security measures stipulated in the plan should be in place.
Some of the technical aspects of file transfer security measures that are in line with those recommended by the Federal Trade Commission (FTC), the government agency tasked to draw up the Safeguards Rule, include the following:
✔ Limiting employee access to NPI to a need-to-know basis;
✔ Enforcing the use of strong passwords;
✔ Securing customer data that find their way into employee mobile devices;
✔ Transmitting customer information through SSL or other secure file transfer protocols; and
✔ Maintaining logs of activity;
Any file transfer software that readily supports these security measures can help immensely in achieving GLBA regulatory compliance.
SOX
Unlike HIPAA and GLBA, which are both aimed at protecting personally identifiable information, SOX or the Sarbanes-Oxley Act is mainly designed to ensure the reliability of financial reports. All US public companies are required to comply with SOX.
SOX is especially taxing for CEOs and CFOs, who, in accordance with Sections 302 and 404 of the Act, have to certify the accuracy, integrity, and completeness of each annual and quarterly financial report. In addition, they are also required to take charge in establishing internal controls on business processes that contribute to financial reporting, assess the effectiveness of those controls, and ultimately report on and certify the results of the assessment.
Any CEO or CFO caught making false certifications can be subject to criminal penalties such as fines of up to $5,000,000 or imprisonment of up to 20 years.
The purpose of these internal controls is to prevent malicious individuals from fraudulently manipulating financial data. What does this mean for file transfer software? It means, if you’re the CEO (or the person responsible for SOX compliance), you need to make sure that the file transfer software your employees use for transmitting financial report data is really capable of securing that data. For instance, it must be able to preserve the confidentiality and integrity of the data as it is sent over the network.
SOX compliance is a very expensive and tedious exercise. And so it is important to avoid practices and IT solutions that can only complicate matters.
That brings us to consumer-grade file sharing services. Consumer file sharing solutions like DropBox are often employed in lieu of traditional file transfer software. These cloud-based software are very easy to use. But if those files contain financial reporting information, these solutions can pose a big obstacle to compliance.
First of all, these solutions scatter “synced” copies of files all over the place – in your laptop, desktop, smartphone, tablet, you name it. And with mobile devices like smartphones and tablets, it would be so easy for sensitive financial data to wander off from the safety of your corporate network. To achieve SOX compliance, you would have to secure all those endpoints.
That’s not all you’d have to worry about. Cloud solutions like DropBox will be storing your files in their datacenters, not yours. That means, you would have no control over security.
The distributed and relatively unmanageable nature of these solutions would make it extremely difficult for you to enforce internal controls or even perform the necessary audits. Simply put, it would be almost impossible to achieve SOX compliance with these solutions.
A centralized secure file transfer server, administered by your own IT department, would certainly be a much better choice.
PCI-DSS
PCI-DSS stands for Payment Card Industry Data Security Standard, a regulation implemented by businesses who handle payment card information. It was engineered to bring down the incidence of payment card fraud. The term “payment card” is mostly associated with credit cards, but may also refer to debit, prepaid, e-purse, ATM, and POS cards.
This regulation consists of various requirements for implementing controls on system components like networks, servers, and applications. PCI-DSS version 2.0 (the current version as of this writing) consists of 12 major requirements and covers items such as:
1. Firewalls;
2. Passwords;
3. Secure data storage;
4. Data-in-motion encryption;
5. Anti-virus software;
6. Development of secure applications;
7. Need-to-know access;
8. Unique IDs;
9. Restricted physical access;
10. Network monitoring and tracking;
11. Security systems testing; and
12. Information security policies
To ensure PCI-DSS compliance, your file transfer software should meet these requirements wherever applicable.
Fortunately, we’ve already written a detailed discussion on PCI DSS-compliant file transfers. It’s a three-part article entitled Guide to PCI DSS Compliant File Transfers. We also have another three-part series that focuses specifically on the PCI DSS password requirements and how they can be enforced in our managed file transfer server. If you conduct inter or intra-organizational file/data transmissions involving credit card data, you should find those two articles very useful.
Your file transfer software should be built for compliance
Several commonly used ad hoc file transfer solutions already offer some security features. For example, email services like Gmail (which are often used for sharing files) may already employ SSL. SSL provides authentication and data-in-motion encryption.
But while encryption and authentication are certainly important security mechanisms, they are by no means the only ones required by most regulations. Just take that list of requirements under PCI-DSS, for example.
What if, in order to achieve full regulatory compliance, you also need to enforce other methods of security like say, strong passwords? If your existing file transfer software does not offer a comprehensive suite of password security settings , you’ll have a problem. And so to achieve compliance, you would be forced to acquire two or more additional software applications. Integrating all these applications and making them work seamlessly can be costly and time consuming.
It would be much easier and less expensive to achieve regulatory compliance if your file transfer software already includes practically all the needed security right out of the box. That’s why many companies who operate in heavily regulated industries find managed file transfer servers the perfect choice. A managed file transfer server like JSCAPE MFT Server is already packed with all the essential attributes of a secure file transfer and hence can help immensely in compliance endeavors.
Downloads
JSCAPE MFT Server is a powerful platform-independent managed file transfer server with installers for Windows, Mac OS X, Linux, Solaris and UNIX platforms. Download a free fully-functional evaluation today.
Download JSCAPE MFT Server Trial





