TOTP or Time-based One Time Password is an algorithm that factors in the current time to generate a unique one-time password. It is increasingly becoming an option for 2-factor authentication (where it is typically used alongside username/password authentication) in secure cloud / web-based applications.

Why TOTP?
The never ending string of data breach incidents caused by exploits on password-based authentication systems is telling us one thing – passwords alone can’t keep the bad guys out. That’s why an increasing number of businesses are starting to employ some form of two-factor authentication (2FA). The usual practice is to augment username/password logins with a second factor of authentication.
While 2FA significantly improves the authentication process and in turn makes it more difficult for the bad guys to break in, there’s always the challenge of making things easy for end users. If your end users find your controls too obstructive to their daily tasks, they might look for ways to circumvent them or, worse, start looking for working environments they perceive to be less-draconian.
Therefore, in order for a 2FA system to work, it must be both secure and user friendly. TOTP (defined in RFC 6328) ticks both boxes perfectly.
A Time-Based One-Time Password is secure because:
1) The one-time password changes every n number of seconds (usually, 30-seconds), thereby preventing eavesdroppers from using that same password later in the future if somehow they’re able to get hold of it.
2) The password may be generated by an app on the user’s own phone, thereby making it more difficult for an attacker to acquire the password, as the user’s phone is usually by his/her side most of the time and is usually locked when not in use.
It’s user-friendly because:
1) In mobile app implementations, the user only needs to launch the TOTP application and then key-in the TOTP that appears on-screen onto the web application’s login screen.
2) Unlike most mobile-based one-time passwords that need to be received via a text message or via the Internet through some wireless connection, TOTPs aren’t dependent on the presence of a cellular signal or data connection.
Let me now explain how a typical end user would login using a TOTP.
How TOTP works
There may be slight variations from one web app to another, but this is the basic methodology. The first time an end user arrives at a login screen of an application that employs TOTP, that user will first be asked to authenticate using the regular username/password method. If the login succeeds, he/she will be presented with a shared secret.
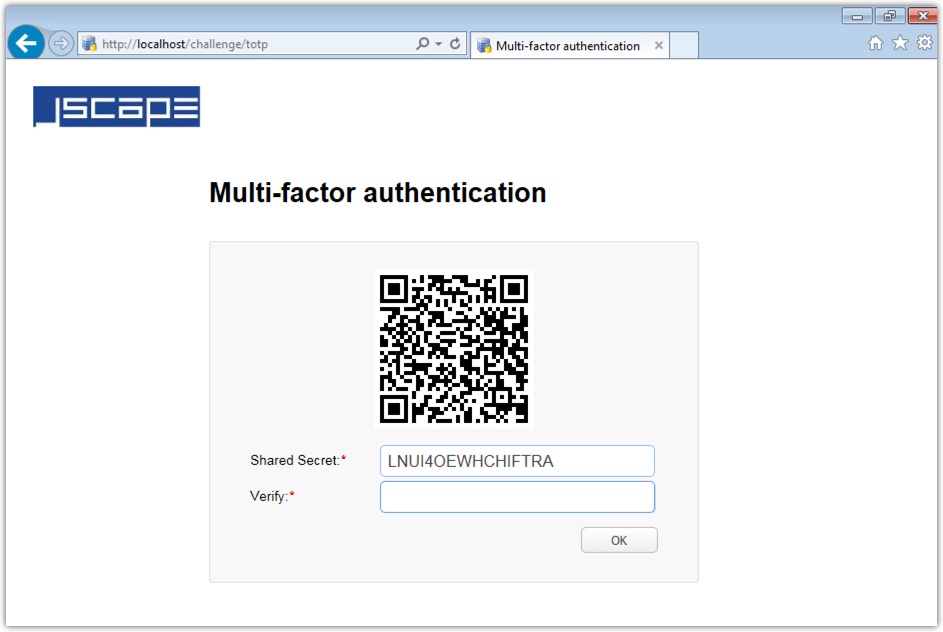
The user will then have to key-in that shared secret into a TOTP mobile app (e.g. Google Authenticator) installed in his/her phone. For convenience, the user will also be presented with a QR code. So, instead of manually keying-in the shared secret, the user can simply scan that QR code with his/her phone.
Figure 1. Sample shared secret key and corresponding QR code on a TOTP-equipped web application
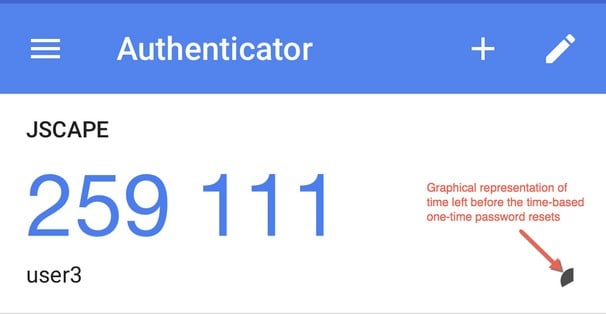
Once the scan completes, a new user account (along with the name of the web app) will be created in the TOTP mobile app. If you view that user account in the TOTP mobile app, you’ll notice that it’s accompanied by a password (e.g. 259111) that changes every n-number of seconds (usually 30 seconds). That’s the Time-based One Time Password or TOTP. There should be a graphical representation of the time remaining before the next TOTP will be generated.
Figure 2. Screenshot of a sample user on Google Authenticator
In order for the user to login, he/she should enter the current TOTP into the field provided on the web application’s login screen. In our example shown in Figure 1 above, it’s the field labeled Verify.
Once the user has verified, he/she will no longer have to enter a shared key or scan a QR code in succeeding logins. All the user has to do in succeeding logins is key-in the TOTP currently displayed on his/her mobile app into the Verify field.
JSCAPE MFT Server will start supporting TOTP-based 2FA authentication in version 11. Watch out for its release in the next few days!