Securing internal networks during eDiscovery using a reverse proxy

Overview
When your company undergoes eDiscovery, there can be numerous file exchanges between your organization and people who normally wouldn't have access to your internal network. In this post, we'll show you how you can carry out these exchanges without exposing other parts of your network to external users.

E-Discovery activities that may require file transfers
An e-Discovery process typically consists of the following stages:
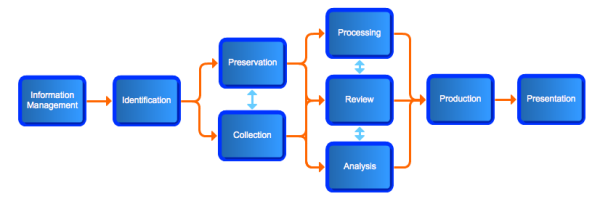
At various stages in the process, external service providers (e.g., attorneys, paralegals, forensics experts, IT consultants) and company employees (e.g., IT staff, HR, corporate in-house counsel) will be exchanging information needed in various e-discovery activities such as:
-
preservation and collection;
-
evaluation of collected ESI to determine relevance;
-
culling and deduplication;
-
language translation;
-
conversion of native files to other formats (e.g. PDF, TIFF, HTML)
Some of these activites may have to be carried out remotely, in which case ESI may have to be transmitted back and forth over an insecure WAN or the Internet. Because e-mail is not suitable for large file transfers and cloud-based file sharing does not have enough controls (e.g. role-based access control, user and event logs, encryption) for preserving data intergrity and security, you may be forced to employ a managed file transfer server for these sensitive exchanges.
Where to deploy your file transfer server
There are a couple of things to consider when picking the most strategic location to deploy your file transfer server. For one, you'll want to make sure you can easily implement optimal security and take advantage of your existing infrastructure's capabilities.
Since you'll be interfacing with separate entities and most of the file transfers will be originating from your company, it would be logical to position your file transfer server at your end.
Besides, the eDiscovery process could involve many individuals who will be working from within your organization's internal network. It would be wise to let them to take advantage of your internal network's relatively faster speed (compared to a typical Internet connection) and stronger security (since it will presumably be behind your firewall).

While the network configuration above can satisfy most of your e-Discovery file sharing needs, it can expose other machines in your internal network to external threats. As much as possible, your internal network shouldn't be accessible directly from the outside.
This is the reason why many large enterprises construct what is known as a DMZ and then position their corporate network behind it. All public-facing servers are then placed on the DMZ, thereby preventing direct inbound connections to their internal network.
Although this configuration is already very secure, it can also be very costly. This is because some users in the internal network will need to access some of the services that are being served in the DMZ. For example, in an e-Discovery process, IT staff, in-house legal counsel, HR, and many others may need to upload/download files to/from the file transfer server.
To cater to the needs of these internal users and to maintain data consistency, you will need to set up duplicate servers as shown below:
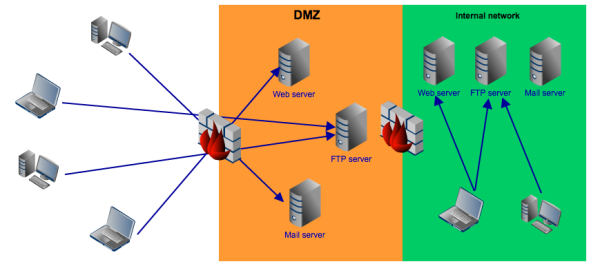
Deploying duplicate servers and keeping them synchronized can be very expensive and complicated. Those aren't the only issues. Some regulations explicitly prohibit certain types of information from being stored in the DMZ.
A better way to utilize a DMZ
A better way of utilizing a DMZ for this purpose is by setting up a reverse proxy server, deploying it in your DMZ, moving your file transfer servers inward, and then enabling access to them through the reverse proxy. Not only is this more economical, it is also simpler and more compliant to regulatory requirements.
Here is a simplified view of how such a configuration would look like:
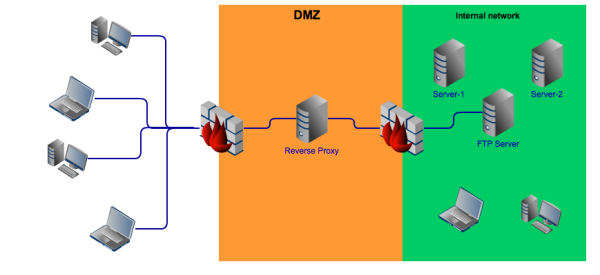
Our reverse proxy server, which we call JSCAPE MFT Gateway, makes use of DMZ streaming, a technology that transmits files securely through the reverse proxy without ever storing them there. When external users upload or download files, they'll think they're interacting with your file transfer server when in fact they'll be interacting directly with your reverse proxy.
To learn more about the advantages of deploying a reverse proxy, please click that link.
Summary
E-Discovery is one activity where you may have to reveal a great deal of information to people who don't belong to your organization. This alone can have unfavorable implications businesswise. Moreso if the opposing party is your competitor. Since there will still be a great deal of company information that won't be relevant to the case, you will want to keep that information safe from prying eyes. You now know how you can.
Would you like to try a reverse proxy for FREE?
JSCAPE MFT Gateway comes with a fully-functional evaluation edition which you can download right now.