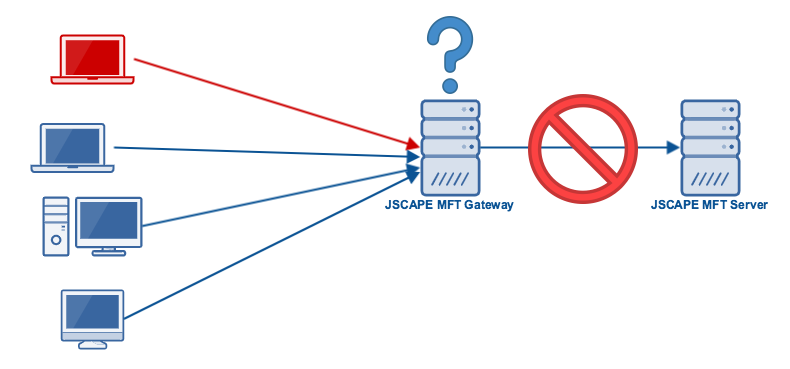
If you’ve been using JSCAPE MFT Server, you probably already know it has a built-in feature that enables it to block suspicious IP addresses. However, if your MFT Server instance is placed behind a NAT or reverse proxy like JSCAPE MFT Gateway, there can be a bit of a problem.
Prefer watching instead of reading? Play the video below.
Blocking suspicious IP addresses on MFT Server
The feature we’re talking about can be found in the Connections module. There you’ll find a couple of settings which, if enabled, can disable (block) an IP address. One of them blocks an IP if the client connecting from it has been making too many invalid password attempts. The second one blocks an IP address if the client has been making too many concurrent connections.
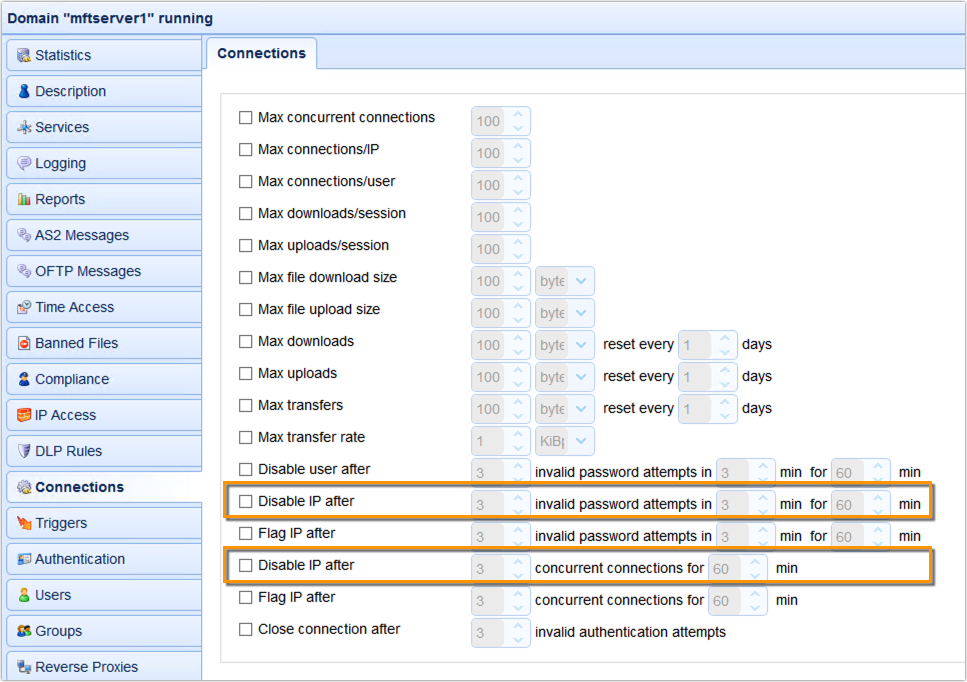
Let me explain how these settings can be useful. Let’s start with the first, i.e. blocking an IP address if the client connecting from it has been making too many invalid password attempts. This can be useful because, although a user that’s been making too many invalid password attempts might simply mean that that user might have forgotten his/her password, it could also be indicative of a brute force attack. And one way to counter such an attack is to simply block the attacker’s IP address.
The second one, which blocks an IP address if the client connecting from it has been making too many concurrent connections can also be useful because this behaviour is symptomatic of a Denial-of-Service (DoS) attack.
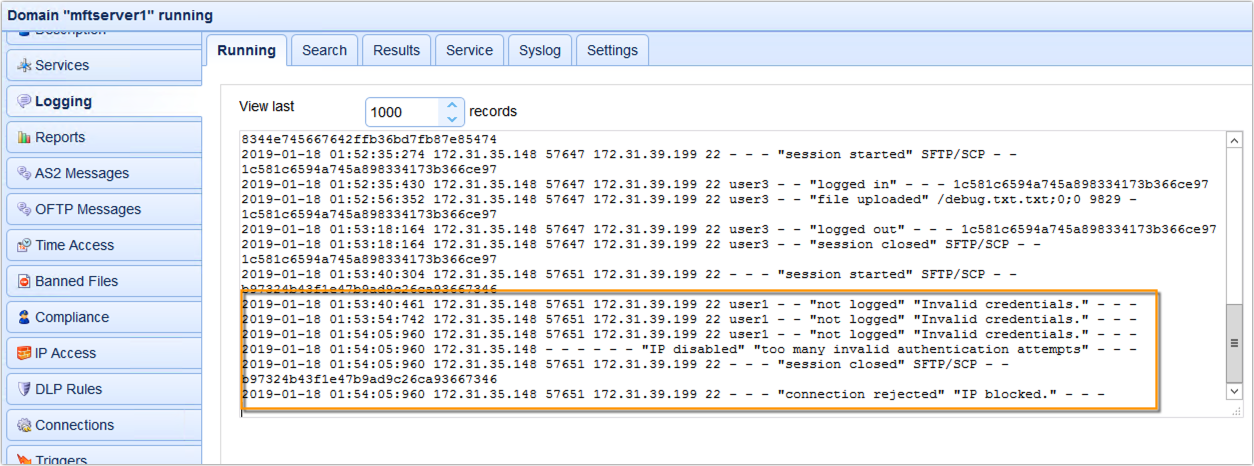
Here’s a portion of the domain log showing 3 invalid login attempts and a subsequent IP block.
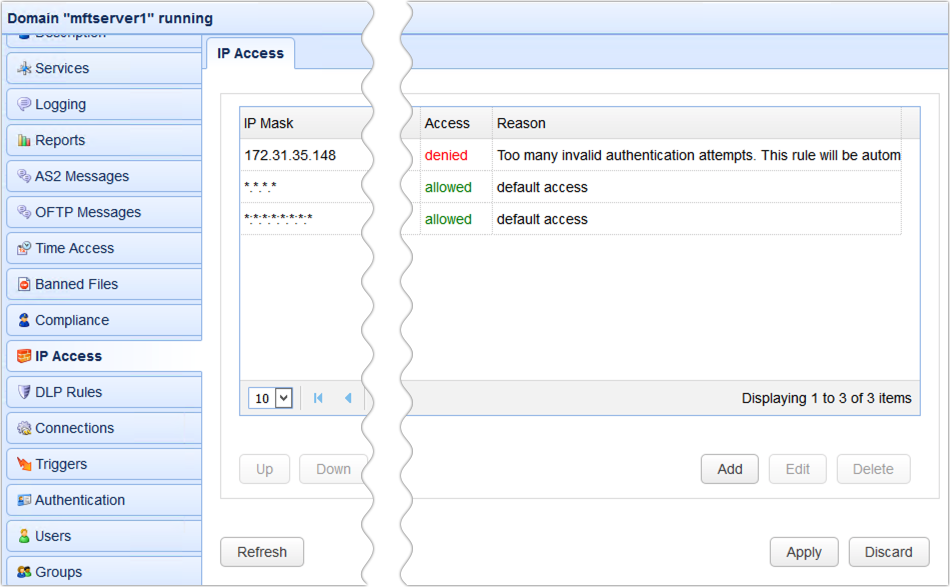
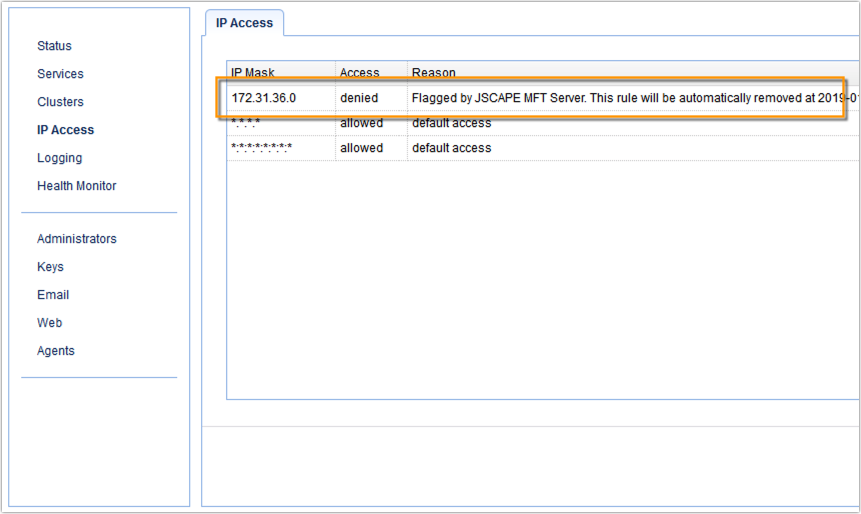
You can see all blocked IP addresses in the IP Access module.
So, to counter these two types of attacks, you just simply enable and configure those two settings. Problem solved. Umm, not so fast. If your MFT Server is deployed behind a NAT or reverse proxy like MFT Gateway, all source addresses of all incoming connections will be the IP address of MFT Gateway. As a consequence, those settings will end up blocking that IP address and, consequently, all clients (including legitimate ones) that wish to connect to MFT Server but have to go through MFT Gateway.
Not a good thing. So, here’s the proper way to do it.
The proper way to block IP addresses
What we need to do involves the following steps. First, we need to change the ‘Disable IP…’ setting with the ‘Flag IP after…’ setting. So, instead of immediately blocking the suspicious IP, MFT Server will just flag it first.
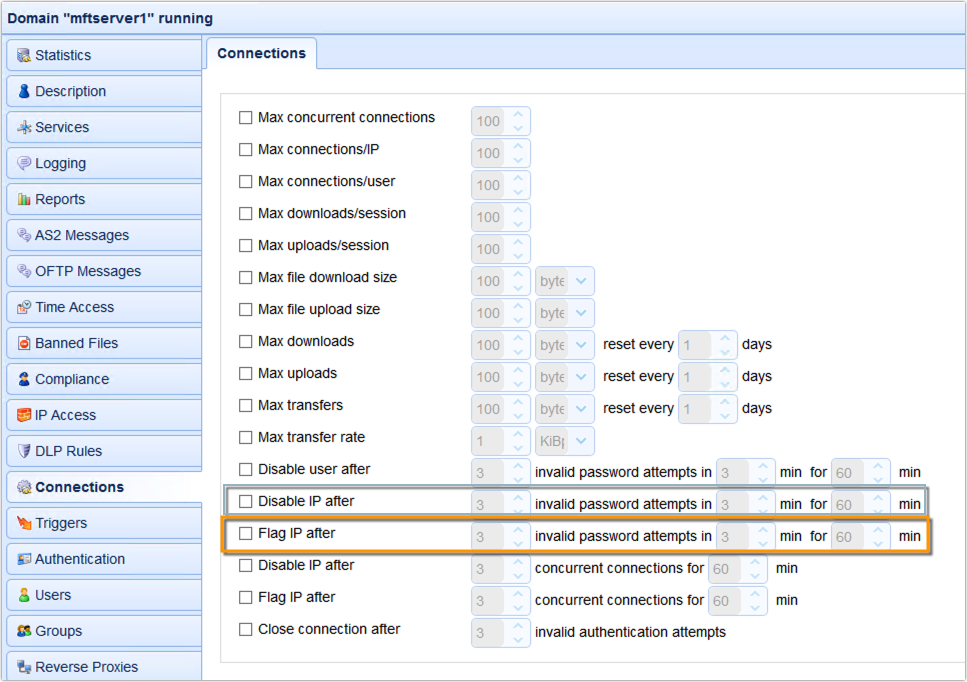
Second, we need to create a trigger that would listen to the ‘IP Flagged’ event type and then respond with a ‘Gateway Block IP’ trigger action. The ‘Gateway Block IP’ trigger action is designed to work with MFT Gateway so that, instead of having to block the IP address at MFT Server, that responsibility will be delegated to MFT Gateway. This is actually a good thing because MFT Gateway would have knowledge of the actual source IP address of the client that’s doing all these invalid login attempts. As such, it would be able to block that IP address itself.
So, let’s just create a new trigger…
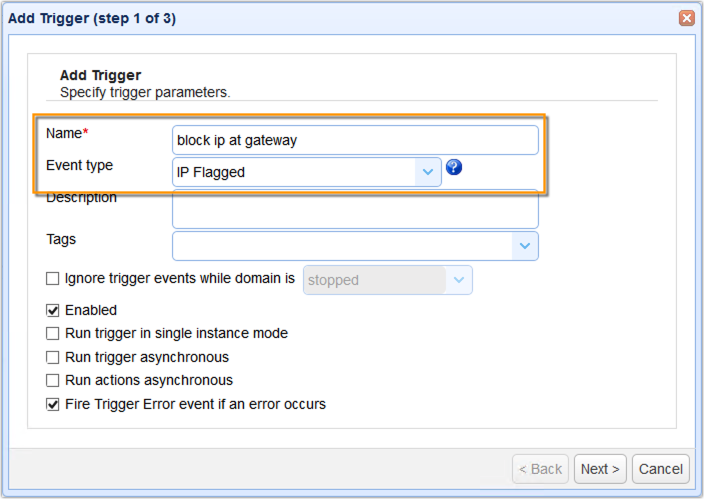
Give it a name and select the IP Flagged event type…
We can just click Next for now…
Add the ‘Gateway Block IP’ trigger action…
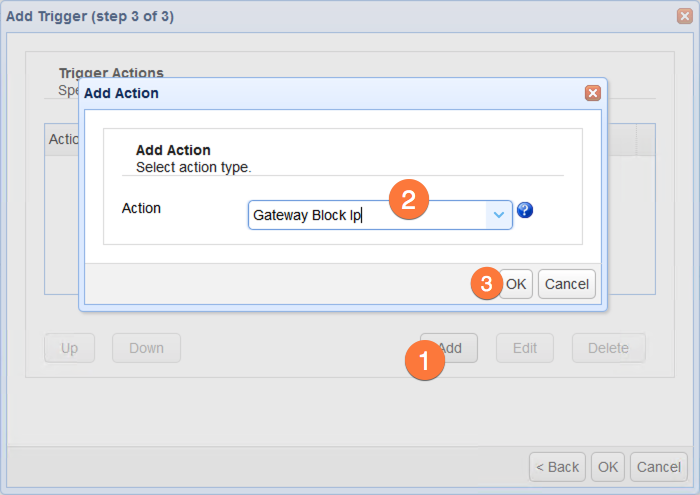
And specify the action parameters…
First parameters to enter are the MFT Gateway’s IP address and the administrative login credentials.
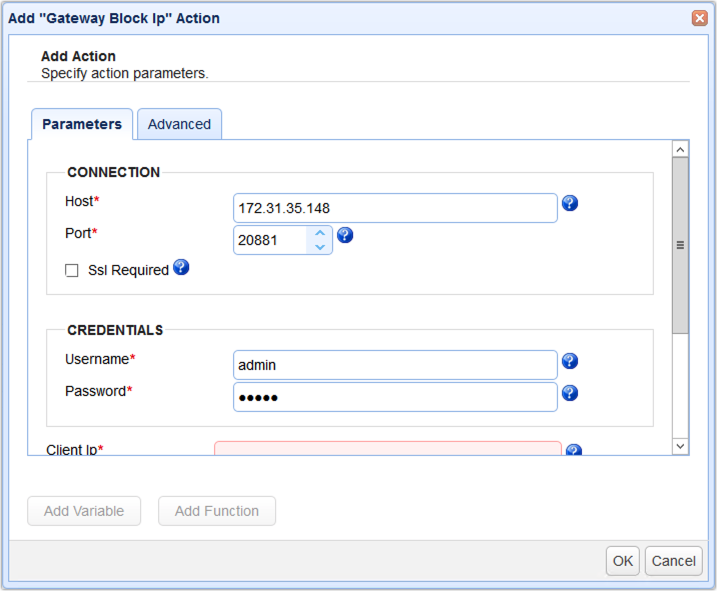
You would also need to enter the Client IP, Client Port, Server IP, and Server Port. The easiest way would be to just use the variables for those values from the Add Variable dialog.
And so, once you’ve created that trigger, every time a client makes too many invalid login attempts, the IP address of that client will be blocked on the MFT Gateway instance. You can see that trigger being activated in the logs…
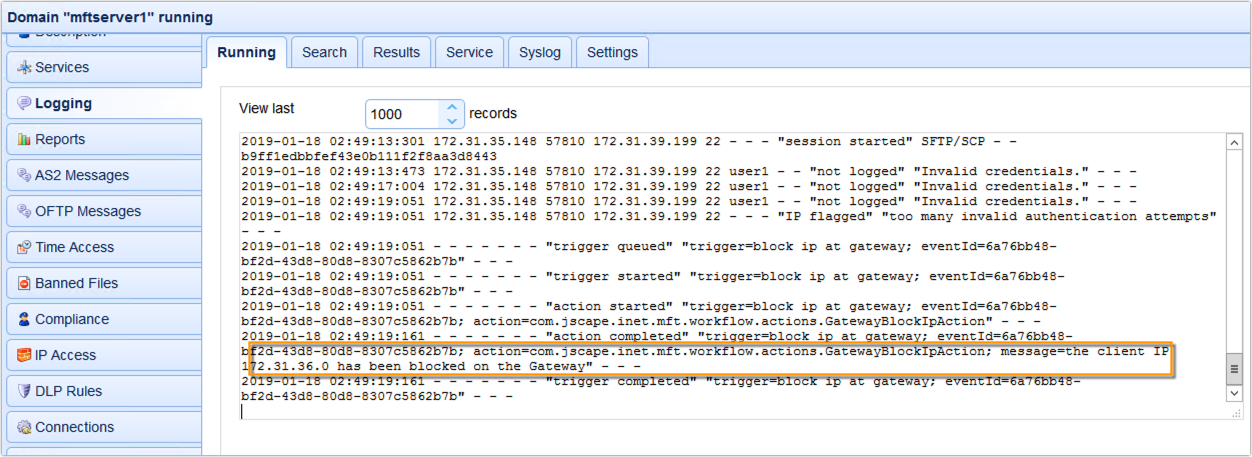
And see the actual client IP address being blocked in the IP Access module of MFT Gateway.
Would you like to try this out yourself? Request the free trial of JSCAPE MFT Server and JSCAPE MFT Gateway now; click the image below.





