Guide to PCI DSS Compliant File Transfers - Part 3


In Part 1 and Part 2 of this series we focused on the basics of PCI DSS. Now that you've become familiar with the general requirements for achieving PCI DSS compliance, your next step would be to scout for solutions that would help you meet them. In that regard, allow us to present JSCAPE MFT Server and JSCAPE MFT Gateway, two products that already have the necessary features to meet practically all technical requirements specified in PCI DSS that affect file transfer systems.
What you saw in Part 2 were only the general requirements of PCI DSS. But if you've seen the complete "PCI DSS Requirements and Security Assessment Procedures, Version 3.0" document, then you know that there are still quite a number of sub-requirements (which I shall sometimes refer to in this post as 'requirement details') under each of those 12 we already mentioned.
Although we can't go through every single sub-requirement here, we've picked some of those that directly affect file transfers and pointed out the specific JSCAPE solutions that can help you meet them.
Note: You might want to open Part 2 in a separate tab on your browser so you can easily refer to the general requirement definitions from there.
1. Install and maintain a firewall configuration to protect cardholder data
1.1.5 Establish firewall and router configuration standards that include ... documentation and business justification for use of all services, protocols, and ports allowed, including documentation of security features implemented for those protocols considered to be insecure.
JSCAPE Solution: This requirement detail implies that you should conduct a thorough assessment as to which specific file transfer services are absolutely necessary for your business. Because JSCAPE MFT Server supports a wide range of file transfer services and protocols (FTP, FTPS, SFTP, HTTPS, HTTP, AS2, WebDAV, etc.) as well as a host of security features, you can have more flexibility in choosing secure file transfer services that best suit your operations from a single product.
1.2.1 Restrict inbound and outbound traffic to that which is necessary for the cardholder data environment.
JSCAPE Solution: Once you've established which file transfers are necessary for your CDE, you can proceed to define Trading Partners in your JSCAPE MFT Server Manager. Trading Partners are entities with whom you want to exchange data regularly. You can even set specific IP addresses that should be granted access so that all other traffic will be blocked.
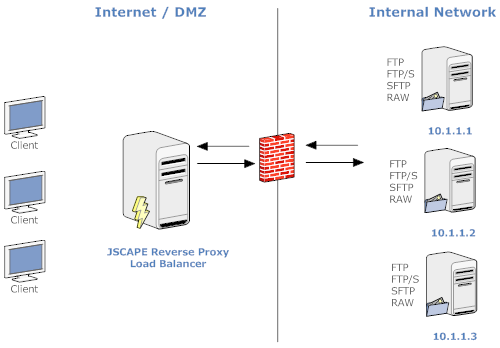
1.3 Prohibit direct public access between the Internet and any system component in the CDE.
Sub-requirement 1.3 is largely about DMZ implementation and how it should be used to insulate your CDE from the Internet.
JSCAPE Solution: JSCAPE MFT Gateway supports DMZ streaming, which can stream sensitive content from the server in your internal network to Internet-based users without storing any of that content in your DMZ. So, by placing 1) JSCAPE MFT Gateway in your DMZ and 2) the server containing your sensitive data in your internal network (which may be part of your CDE), you can restrict all cardholder data to your internal network and out of your DMZ, and therefore out of direct reach from public access.
JSCAPE MFT Gateway's reverse proxy capabilities obscure internal network IP addresses from external sources. This allows it to satisfy PCI DSS sub-requirement 1.3.8, which prohibits the disclosure of private IP addresses and routing information to unauthorized parties.
To learn more about the security capabilities of JSCAPE MFT Gateway, click that link.
2. Do not use vendor-supplied defaults for system passwords and other security parameters.
2.1 Always change vendor-supplied defaults before installing a system on the network, including but not limited to passwords, simple network management protocol (SNMP) community strings, and elimination of unnecessary accounts.
JSCAPE Solution: JSCAPE does not supply any default system password, neither does it include an anonymous account by default. You have to come up with your own password upon installation of your managed file transfer server. You also have to create an anonymous account if you want one.
2.2 Develop configuration standards for all system components. Assure that these standards address all known security vulnerabilities and are consistent with industry-accepted system hardening standards.
JSCAPE Solution: With a plethora of secure file transfer features that include access controls, logs, authentication, encryption, server resource constraints, and others, JSCAPE has enough configurable settings to help you adhere to best practices and configuration standards specified by bodies like CIS (Center for Internet Security), ISO (International Organization for Standardization), SANS (SysAdmin Audit Network Security), and NIST (National Institute of Standards Technology).
JSCAPE MFT Server's extensive support for various secure file transfer protocols allows it to easily satisfy 2.2.3, which calls for the use of secured technologies like SFTP or FTPS over insecure services like FTP.
2.3 Encrypt all non-console administrative access using strong cryptography. Use technologies such as SSH, VPN, or SSL/TLS for web-based management and other non-console administrative access.
JSCAPE Solution: All remote communications between JSCAPE MFT Server and its admin client, JSCAPE MFT Server Manager, are encrypted using SSL.
3. Protect stored cardholder data.
3.1 Keep cardholder data storage to a minimum by implementing data retention and disposal policies, procedures, and processes that include:
-
limiting data storage amount and retention time to that which is required for legal, regulatory, and business requirements;
-
processes for secure deletion of data when no longer needed;
-
specific retention requirements for cardholder data;
-
a quarterly automatic or manual process for identifying and securely deleting stored cardholder data that exceeds defined retention requirements.
JSCAPE Solution: A crucial step in implementing these policies is in identifying what data needs to be retained and where that particular data resides. JSCAPE's managed file transfer server is already equipped with DLP (Data Loss Prevention). DLP can find certain types of data in files by matching regular expressions you specify. This will expedite the identification phase and reduce false-positives and false-negatives.
In addition, JSCAPE MFT Server is equipped with Triggers that can monitor a file's age and enable automatic deletion or archiving as soon as a certain age is reached.
Together, JSCAPE MFT Server's DLP and Trigger features can help you implement data retention and disposal policies with ease.
3.4 Render PAN unreadable anywhere it is stored by using strong cryptography with associated key-management processes and procedures.
JSCAPE Solution: PAN (Primary Account Number) is actually what we often refer to as the credit card number. You can apply DLP Rules to automatically identify stored credit card numbers. A JSCAPE MFT Server installation already comes with a set of DLP Rules for major credit cards like American Express, Diners, MasterCard, and Visa. When used in conjunction with the OpenPGP encryption feature, you can also automatically encrypt files that contain these sensitive information as soon as they are detected.
3.6 Fully document and implement all key-management processes and procedures for cryptographics keys used for encryption of cardholder data.
JSCAPE Solution: JSCAPE MFT Server's built-in Key Manager will allow you to implement a variety of key-management processes from a single panel. These processes include generating, importing, exporting, and deleting of server keys, host keys, client keys, and OpenPGP keys.
PCI DSS requires the use of "strong cryptography" as defined in the PCI DSS Glossary of Terms. The definition provides examples of encryption algorithms which PCI DSS considers acceptable. Among them are AES (128 bits and higher) and RSA (1024 bits and higher), both of which are supported by JSCAPE MFT Server.
When you generate a key in the Key Manager, you'll be asked to specify the key's Validity, i.e., the number of days the key can be used. You can also replace keys or delete keys that are no longer needed. These features make it easy to comply with sub-requirements 3.6.4 and 3.6.5, which emphasize the importance of changing keys at the end of their cryptoperiod and of retiring or replacing keys whenever their integrity is deemed to have weakened.
4. Encrypt transmission of cardholder data across open, public networks.
4.1 Use strong cryptography and security protocols (for example, SSL/TLS, IPSec, SSH, etc.) to safeguard sensitive cardholder data during transmission over open, public networks.
JSCAPE Solution: By using JSCAPE MFT Server, you can offer SSL or SSH-enabled file transfer services like SFTP, SCP, FTPS, and HTTPS. This will allow you to secure your Internet-based cardholder data transmissions.
When you generate keys using JSCAPE MFT Server's Key Manager, you can actually choose between 1024 and 2048-bit key lengths. Thus, the shortest key length supported by JSCAPE MFT Server already meets the minimum key length required by the standard. You can likewise set cipher strengths for SFTP and FTPS in the SFTP and FTP/S service modules, respectively.
5. Protect all systems against malware and regularly update anti-virus software or programs
5.1 Deploy anti-virus software on all systems commonly affected by malicious software (particularly personal computers and servers)
JSCAPE Solution: As mentioned in Part 2 of this post, file transfer servers are very susceptible to virus infections. To counter viruses on JSCAPE MFT Server, you can create Triggers that work with your antivirus software to enable automatic virus detection and quarantine/removal capabilities. This will allow your server to quickly act on viruses whenever an infected file is uploaded.
5.2 Ensure that all anti-virus mechanisms are current, actively running, and generating audit logs.
JSCAPE Solution: JSCAPE MFT Server also has the ability to prompt antivirus software installed in your server to perform automatic antivirus database updates. If you are able to configure your server this way, your antivirus will be up to date. Furthermore, JSCAPE MFT Server can also keep logs of events associated with antivirus activities.
5.3 Ensure that anti-virus mechanisms are actively running and cannot be disabled or altered by users....
Antivirus mechanisms on JSCAPE MFT Server, which come in the form of Triggers, can only be altered by those with administrative access.
6. Develop and maintain secure systems and applications.
6.1 Ensure that all system components and software are protected from known vulnerabilities by having the latest vendor-supplied patches installed. Install critical security patches within one month of release.
JSCAPE Solution: Since its first release in 2006, we have provided multiple releases for JSCAPE MFT Server every year and will continue to do so. Each release consists of enhancements, changes, and bug fixes. Because the product itself is specifically designed to provide secure file transfers, you can be sure that making security improvements is always the first thing we have in mind.
Once you purchase a copy of JSCAPE MFT Server, you will be entitled to free upgrades for a period of one year. After that, you can then purchase a very affordable maintenance agreement that will entitle you to another year of free upgrades. So if you take advantage of these privileges, you can improve the security of your file transfer system at very minimal cost.
The latest version of JSCAPE MFT Server can be found here.
7. Restrict access to cardholder data by business need-to-know.
7.1 Limit access to system components and cardholder data to only those individuals whose job requires such access.
JSCAPE Solution: As mentioned in Part 2, one solution that can help you meet this requirement is to implement RBAC. In JSCAPE MFT Server, you can easily implement RBAC in your file transfer server by assigning users to "groups". A group is just a named set of virtual directories and file system permissions (in the context of your file transfer system) that you can assign to user accounts.
So, for example, you can limit access to directories that contain cardholder data only to users who belong to a particular group. JSCAPE's virtual file system is designed so that a user who logs in to your file transfer service will only see the directories assigned to him. To that user, it will appear that all other directories do not exist.
8. Identify and authenticate access to system components
Note: Passwords and authentication are among those areas that are being given more emphases in PCI DSS 3.0. Since we already have a detailed article on Required MFT Server Password Settings for PCI DSS Compliance, we'll just be discussing a few of the relevant requirements here. Click that link to dig deeper into that particular area of PCI DSS compliance.
8.1 Define and implement policies and procedures to ensure proper user identification management for non-consumer users (e.g. employees, administrators, and third parties) and administrators on all system components
JSCAPE Solution: By design, each user created on JSCAPE MFT Server is associated with a single person. When creating a new user, you'll find fields for the person's name, login name, email address, and phone (among others). No two users can have the same login name, so this can serve as the unique ID. Assigning all users a unique ID is an essential sub-requirement that's stipulated in 8.1.1.
Each user's file transfer session is logged, so you can trace back that particular user's actions later on in an audit.
8.2 In addition to assigning a unique ID, employ at least one of the following methods to authenticate all users: 1) something they know, e.g. a password or passphrase, 2) something they have, e.g. a token device or smart card, or 3) something they are, e.g. a biometric.
JSCAPE Solution: JSCAPE MFT server supports two of the authentication methods mentioned: 1) something they know - a password, and 2) something they have - a token (which takes the form of a client key). So if you want more secure logins, you can require the user to authenticate his identity using both his password and his client key.
You can set certain requirements for passwords. For example, a minimum password length, maximum password age, and that a password must not match previous n number of passwords, among others. If your requirements are not met during login, the user will be denied access even if his password is correct.
It is also possible to authenticate users against existing LDAP, NTLM, Active Directory, PAM, or relational database servers.
Furthermore, 8.2.1 requires the use of "strong cryptography to render all passwords unreadable during transmission and storage on all system components using strong cryptography." This can be met by requiring each user to login using secure and encryption-enhanced protocols like FTPS, SFTP, or HTTPS
8.3 Incorporate two-factor authentication for remote access to the network by employees, admins, and third parties.
JSCAPE Solution: While the password + client key combination may be considered as two-factor authentication, JSCAPE also provides an even stronger form of two-factor authentication. The Phone Authentication module provides two-factor authentication for a user by combining the user's password (something he knows) with his telephone or cellphone (something he has). It works this way:
-
A user logs in as usual,
-
he receives a phone call asking him to confirm whether a valid login was made,
-
the user confirms,
-
the system verifies, and
-
the user is granted access.
9. Restrict physical access to cardholder data.
JSCAPE Solution: Since JSCAPE MFT Server is a software application, it doesn't have controls that can restrict physical access. However, what it does have is an encryption feature. Thus, even if an intruder is able to acquire the hard disks of your file transfer server, for as long as you have encrypted your data, it will be virtually impossible for that intruder to view the information inside.
10. Track and monitor all access to network resources and cardholder data.
10.1 Implement audit trails to link all access to system components to each individual user.
JSCAPE Solution: Logs are kept for each individual user. You can even conduct a search on the logs against a specific username to trace activities associated with that user. If you've implemented RBAC, you can narrow down your investigation to users who have access to cardholder data in your file transfer server.
10.3 Record at least the following audit trail entries for all system components for each event: user identification, type of event, date and time, success or failure indication, origination of event, identity or name of affected data, system component, or resource
JSCAPE Solution: All these entries are collected by JSCAPE MFT Server and can be viewed in the Logging panel. Note that the JSCAPEs logs allow you to track events either as they happen or by looking into a specific time duration in the past.
10.6 Review logs and security events for all system components to identify anomalies or suspicious activity.
JSCAPE Solution: When reinforced with the Reports module, JSCAPE MFT Server's Logging module can greatly enhance the reviewing process. It features a large selection of metrics and has the ability to generate graphs, enabling you to work more efficiently and to spot anomalies and suspicious activities faster.
11. Regularly test security systems and processes.
11.4 Use intrusion-detection systems, and/or intrusion-prevention systems to monitor all traffic at the perimeter of the cardholder data environment as well as at critical points inside of the cardholder data environment, and alert personnel to suspected compromises.
JSCAPE Solution: You can configure JSCAPE MFT Server to detect brute force password attacks and automatically disable the account in question or block its corresponding client IP address from future requests. In addition, you may configure JSCAPE MFT Server to send automatic email notifications to a system admin, informing him about the account disabling or IP blocking. This should prompt him to conduct an investigation on the matter.
12. Maintain a policy that addresses information security for all personnel.
12.3 Develop usage policies for critical technologies and define proper use of these technologies. Ensure these usage policies require ...
... 12.3.8 Automatic disconnect of sessions for remote-access technologies after a specific period of inactivity.
JSCAPE Solution: JSCAPE MFT Server can help your users "comply" with this usage policy because it can automatically disconnect file transfer sessions after a specific period of inactivity. Basically, you can set a Connection Timeout value. This is the number of minutes that a client connection can stay inactive before JSCAPE MFT Server will forcefully disconnect it.
Thus, even if a user forgets to log out (although he shouldn't), your file transfer system won't remain vulnerable for long.