The SSH File Transfer Protocol (SFTP) uses TCP port 22 as its default port number. However, if you or your server administrator wishes to assign a different port number for your SFTP service, the protocol allows it. In this post, we’ll take a closer look at the default SFTP port number and tackle some key considerations when choosing alternate port numbers for your SFTP server.
Before we do that, let’s review what SFTP is.
What is SFTP? A brief review
Also known as Secure File Transfer Protocol, SFTP is an extension of Secure Shell (SSH). It was introduced in SSH v2 or SSH-2 as a method for transferring files. Since SFTP runs over SSH, every SSH server is technically an SFTP server as well. In addition, since SSH listens on port 22 by default, SFTP listens on that port number too.
You must bear in mind that SSH also supports Secure Copy Protocol (SCP), another protocol for transferring files. Like SFTP, SCP also uses the same SSH port number — 22. However, SCP has fewer capabilities compared to the SFTP protocol. If you wish to know the key differences between these two protocols, you can read our article “SCP vs SFTP – 5 Key Comparisons.”
SFTP is a popular alternative to the standard File Transfer Protocol (FTP) due to the former’s array of security features. The FTP protocol’s lack of security features makes it unsuitable for today’s business processes, which often involve personal information, financial data and other sensitive information.
SFTP is equipped with public key cryptography, a cryptographic system that uses pairs of private keys and public keys. Public key cryptography enables data-in-motion encryption, authentication, digital signing and data integrity mechanisms. The same cryptographic system allows you to augment passwords with SSH keys (a.k.a. SFTP keys), thereby allowing you to implement two-factor authentication (2FA). These security features make SFTP perfect for meeting stringent security policies and regulatory requirements.
Don’t confuse SFTP with FTPS. They’re both secure FTP alternatives, but are two different protocols. FTPS stands for FTP-over-SSL, with SSL being the acronym for Secure Sockets Layer, a now-obsolete cryptographic system that used to be a popular choice for securing network-based transactions.
SSL has already been replaced by Transport Layer Security (TLS). However, many security solutions have opted to retain the ‘s’ in relevant acronyms. So, for example, FTPS still uses ‘S’ even if it actually uses TLS under the hood.
When is an SFTP port number needed?
You would mostly need an SFTP port number when you connect to an SFTP service from graphical SFTP clients like WinSCP or FileZilla, or from command-line clients like those built into endpoint device platforms such as Windows, Linux or Mac. You normally submit the port number along with the SFTP service’s IP address or hostname. For example, if your SFTP server is using port 2222, you would typically execute the following SFTP command from the terminal:
sftp -oPort=2222 username@hostname
Note, however, if the remote SFTP service is just using the default port number, 22, you normally won’t have to enter any port number anymore. Port number 22 will be submitted by default. So, for example, when you execute the following SFTP command to connect, you’ll no longer need to specify the port number:
sftp username@hostname
You’ll only need to specify a port number if the SFTP service is using a non-standard port number.
You would also need an SFTP port number when you connect any application to an SFTP service. For instance, when you set up a server-to-server file transfer, you would need an SFTP port number if your trading partner’s server is an SFTP server.
Lastly, you need an SFTP port number if you have to open that port in a network solution such as a firewall or Network Address Translation (NAT) device. Opening that port number on your network solution allows SFTP connections to pass through. Later in this article, we’ll show you how to open port 22 on Windows Server’s built-in firewall.
Picking an alternative to the SFTP default port for SFTP connection
While you can theoretically use a non-standard port number for your SFTP service, there are a few things to consider.
- Avoid reserved ports. If possible, avoid selecting port numbers in the range of 0-1023, as these are reserved for well-known services. For example, 80 is reserved for HTTP, 443 is reserved for HTTPS, 21 is reserved for FTP, 25 is reserved for SMTP and so on.
- Check port availability. Even if you use a port number outside the range of known reserved ports, make sure you check that port number’s availability. You may use netstat or any similar tool for this purpose.
- Document and disseminate. If you have to use a non-standard port, make sure you document it. That way, you or anyone who needs it in the future can easily look it up. Also, make sure you inform everyone who needs to access your SFTP service about the change. Some users might assume you’re using port 22, and will have difficulty connecting to your server.
- Update firewalls and network devices. If you have network devices along the path of your SFTP connection that allow or deny access, make sure the settings of those devices are updated with the right port number. Otherwise, you’ll encounter connection issues.
Essential How-Tos involving the SFTP port number
How to check the SFTP port number in Linux?
You have several options for checking the SFTP port number on Linux. We mentioned netstat earlier, so let’s use that command-line tool as an example. Run the following command in the terminal:
sudo netstat -tuln | grep ssh
This command will list all TCP and UDP listening ports along with the numeric addresses and names. The output will then be filtered with grep so that it only shows lines containing “ssh.”
How to change the SFTP port in Windows?
We already know that SFTP uses port 22, but you can change that to a different port. To do that, you would need to modify the SSH server configuration file, sshd_config. Follow these steps to make the necessary changes:
- Open the sshd_config file with Notepad or ant text editor. In most cases, you’ll find that file in
‘C:\ProgramData\ssh\’ or ‘C:\Program Files\OpenSSH\’.
- Search for the line that includes ‘Port 22’.
- Change 22 to your desired port number, say for example, ‘Port 2222’.
- Save the changes.
- Restart your SSH server.
How to change the SFTP port in Linux?
You may follow the same steps as in the previous section, except that you’ll have to look for the sshd_config file in the directory ‘/etc/ssh’ and you’ll have to use nano, vi or some Linux-based text editor.
How to open SFTP port 22 in Windows Server?
To open port 22 in Windows Server, you need to open that port on Windows Server’s built-in firewall. Follow these steps to do that:
- Launch “Windows Defender Firewall with Advanced Security”
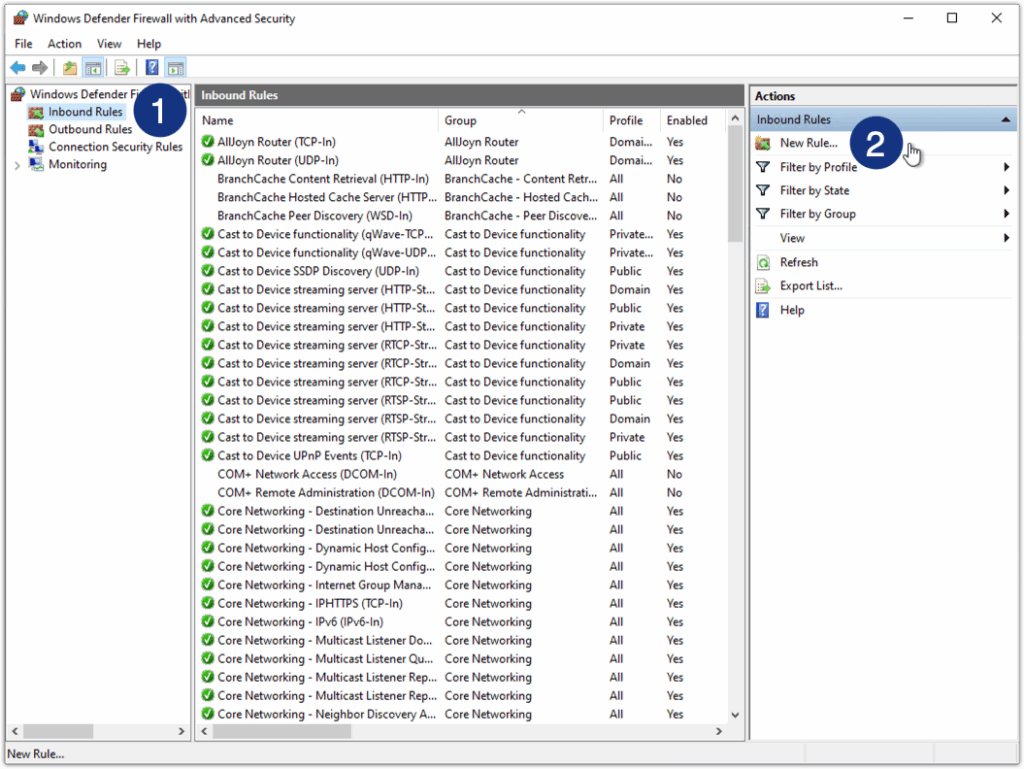
- Create an inbound rule. Go to Inbound Rules > New Rule.
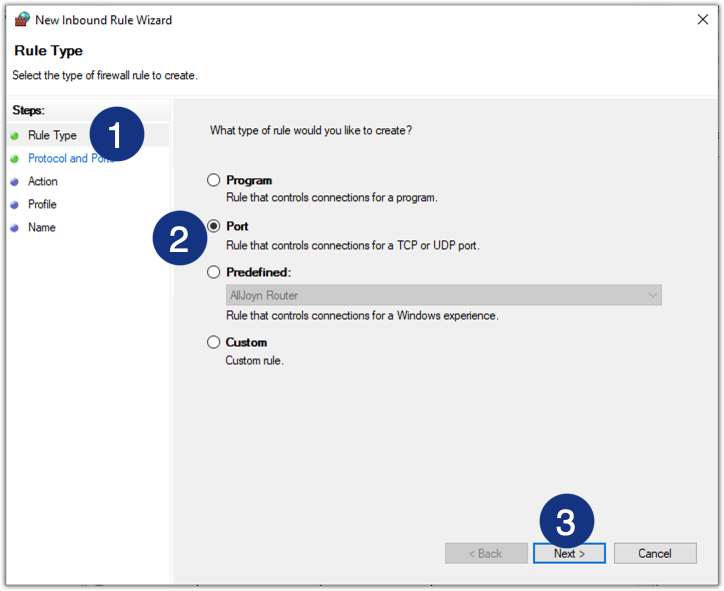
- Select Port as the rule type.
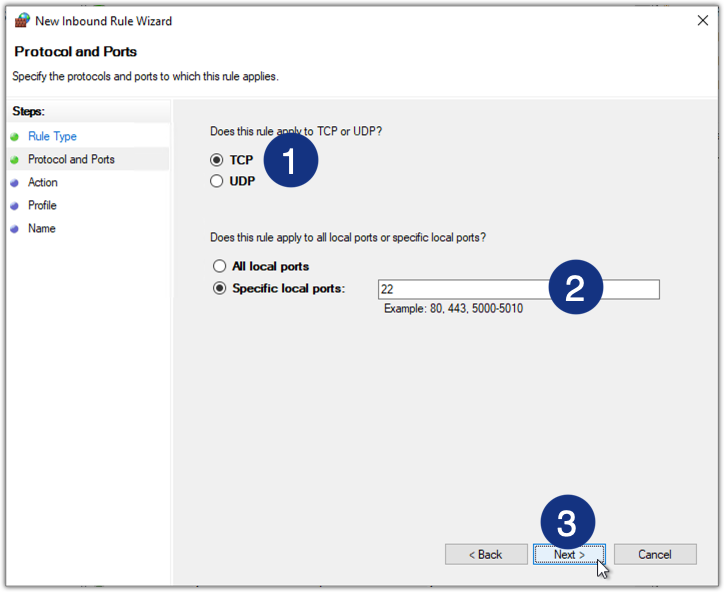
- Specify the port number. Select TCP > Specific local ports and then enter 22.
- Select Allow the connection.

- Specify the profile for which the rule applies. In most cases, you’ll want to apply this rule to all profiles, so tick all checkboxes.
- Give the inbound rule a name, say, “Allow SFTP,” and then click Finish.
Can you use the default FTP port numbers for SFTP?
The default port number for standard FTP is 21. While it’s technically possible to use port 21 for your SFTP service, it’s not recommended. If you review our discussion about picking alternative ports for your SFTP service above, you should see that we discourage the use of reserved ports. Not only can it confuse end users, it can also cause interoperability and connectivity issues with applications that are supposed to connect to that SFTP service.
Next-Level SFTP: Revolutionize your file transfers with JSCAPE MFT by Redwood
Many businesses like to use the SFTP protocol to facilitate business processes, especially those that rely on data transfer and file sharing workflows. However, while regular SFTP servers do a good job at providing data-in-motion security, their capabilities are limited to that. A typical business-to-business (B2B) file transfer demands so much more.
For instance, most B2B file transfers require automation, high availability and system integrations. A regular SFTP server can’t offer you these capabilities out of the box. What you need is a managed file transfer (MFT) solution like JSCAPE MFT by Redwood. JSCAPE MFT supports SFTP along with several other business-grade file transfer protocols like FTP/S, HTTP/S, Applicability Statement 2 (AS2), Odette File Transfer Protocol (OFTP) and many others.
Not only that, JSCAPE MFT also comes with built-in automation, high availability and integration functionality. A JSCAPE MFT deployment is fully equipped to facilitate any B2B file transfer workflow on its own.
JSCAPE MFT can be installed on all major operating systems, including Windows, Linux, UNIX, AIX and macOS. It’s also offered as a cloud-based Software as a Service solution, JSCAPE MFTaaS.
Get Your Free Trial
Would you like to try this yourself? JSCAPE enables you to handle any file type, including batch files and XML.
Related Content
How To Automate An SFTP File Transfer
Install A Linux SFTP Server Via Command Line And Configure Via Web UI
How To Automatically Transfer Files From SFTP To Azure Blob Storage
That Free FTP Server Might Cost More Than You Think
Frequently Asked Questions
What are the features of SFTP?
There are many benefits to using SFTP to transfer files over the internet. SFTP was purpose-built to ensure the safe and secure transfer of data. These built-in security features include single-port transfer to reduce attack points, data encryption, authentication via SSH as well as username/password, and data integrity and authentication checks. Advanced features of SFTP include the ability to pause and resume a file transfer, as well as allowing users to remotely perform basic admin tasks. Finally, unlike other file transfer protocols, SFTP transfers file metadata (file size, date, time, and permissions) by default.
How does SFTP authenticate credentials?
To transfer files via SFTP, you first need to use a client that supports SSH. Then, you can use one of the following three ways to configure an authentication procedure. The first method is to use a traditional username and password combination. The second is to use public key authentication, where the client uses public and private key pairs to identify itself to the server. The final way SFTP can authenticate credentials is by using a public key authentication with an additional password/passphrase. This way, if someone accesses the locally stored private key, they can’t use it until they enter the password to unencrypt it.
Why do you need Managed File Transfer Software for SFTP?
Managed file transfer (MFT) software enables users to design and maintain transfers between endpoints, providing support for multiple secure protocols. Managed file transfer (MFT) tools, like JSCAPE, support SFTP, while also providing IT and security teams with additional layers of security and features.






