Overview
An SFTP reverse proxy adds another layer of security to SFTP services. In addition to SFTP’s ability to encrypt data in transit and provide 2-factor authentication, an SFTP reverse proxy brings in several other security-related benefits such as hiding user credentials and the identities of your internal servers. An SFTP reverse proxy can be easy to set up and this post will show you how.
What we’d like to do

How to Set Up an SFTP Reverse Proxy
Believe it or not, assuming you already have an SFTP server running in the background, you’ll only need 3 simple steps to set up an SFTP reverse proxy in JSCAPE MFT Gateway.
1. Add a reverse proxy service
To add an SFTP service, go to the Services module and then click the Add button.
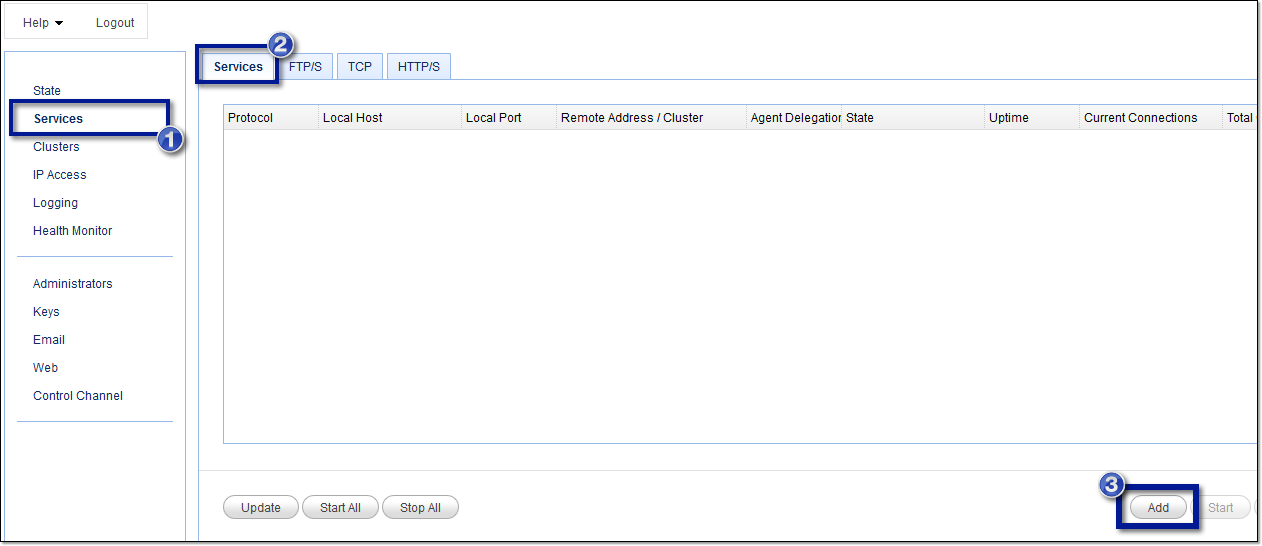
2. Select the SFTP protocol
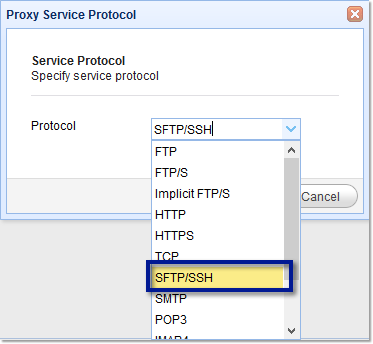
That should bring up the Proxy Service Protocol window. Expand the drop-down list and select SFTP/SSH. Notice that there are several other protocols supported.
Click the OK button when you’re done selecting.
3. Specify the SFTP reverse proxy parameters
The parameters you need to specify for now include the following:
Local host and port – This is the listening IP address and port for the SFTP service on your JSCAPE MFT Gateway instance.
Remote host – The IP address and port number of your target SFTP server. This will be used by JSCAPE MFT Gateway to establish a reverse proxy connection.
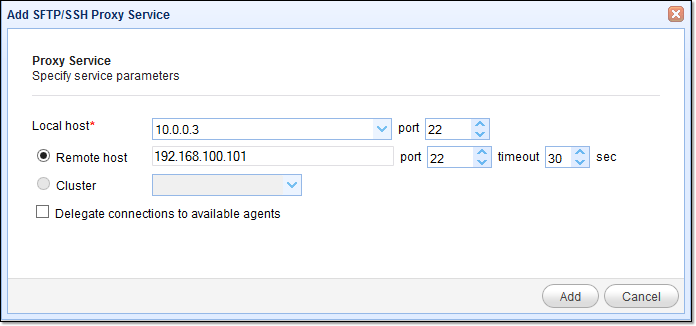
As soon as you’re done, click the Add button. If everything goes well, you should be back at your main screen, where you’ll see your newly created SFTP reverse proxy service.
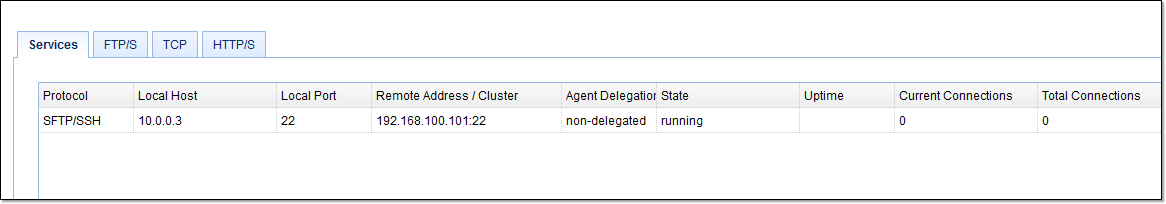
What about public key authentication?
People who have tried setting up an SFTP reverse proxy on JSCAPE MFT Gateway often ask the question: How do we configure our reverse proxy to support public key authentication? SFTP public key authentication provides 2-factor authentication by allowing users to login using something they know (their password) and something they have (their SFTP private key).
The answer is this: you don’t have to configure anything. As long as you already enabled public key authentication on your SFTP server, your users can simply power up their SFTP client, attach their private key, and connect to JSCAPE MFT Gateway.
Want to follow the steps we showed you earlier? Download a free evaluation of JSCAPE MFT Gateway secure file transfer software by clicking the download button below.





