Overview
Some organizations that deal with exceptionally sensitive information need to employ very stringent access restrictions to their internal networks. While a DMZ consisting of firewalls and reverse proxies can, in most cases, meet such requirements, providing network services from the internal network to external clients while also prohibiting inbound connections can be quite challenging. This little reverse proxy enhancement can simplify things.
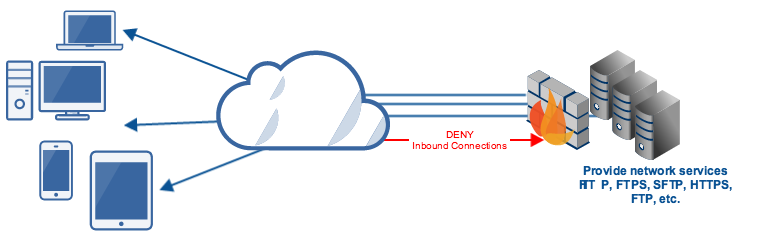
A reverse proxy like JSCAPE MFT Gateway deployed in the DMZ offers a secure way of providing network services (FTP, SFTP, FTPS, HTTP, HTTPS, etc) from internal networks to external clients. With this configuration, it’s possible to just stream data straight from the internal network, through the DMZ, and right to the requesting client. No data will need to be stored in the DMZ.

Coupled with a well-planned DMZ firewall policy, this configuration will allow you to:
- Create a single point of access to your internal servers;
- Simplify access control tasks;
- Move user credentials to a more secure zone;
- Reduce risks to sensitive data;
- Help achieve regulatory compliance;
- Bring down capital and operational expenses; and
- Allow transparent maintenance of backend servers
For more information about these benefits, read the article Top 8 Benefits of a Reverse Proxy.
A reverse proxy like JSCAPE MFT Gateway typically listens on a public-facing network interface for incoming connections. When a valid incoming connection is received from an external client, this reverse proxy will promptly connect to the appropriate internal-network-based server in behalf of the client and then facilitate secure data exchanges between the two.
Notice that, in this configuration, the reverse proxy will still have to make an inbound connection to the internal server. To make this happen, you’ll need to open some ports on your DMZ firewall. The problem is, open ports can be exploited. You can mitigate the risks by employing complex firewall configurations but you can’t totally eliminate the vulnerability.
Achieving zero inbound connections
But is it really possible to fully restrict inbound connections while still offering network services from within? The answer is yes. One way to do this is by employing MFT Gateway Agents. First introduced in JSCAPE MFT Gateway 3.0, an MFT Gateway Agent is an optional component that you install on one or more servers within your internal network.
Its primary purpose is to perform network requests on behalf of JSCAPE MFT Gateway Server. Upon startup, an agent establishes an outbound connection to JSCAPE MFT Gateway Server via a control channel. This connection is maintained while both MFT Gateway and the agent is running. At no instance will there be an inbound connection from the reverse proxy to the agent.
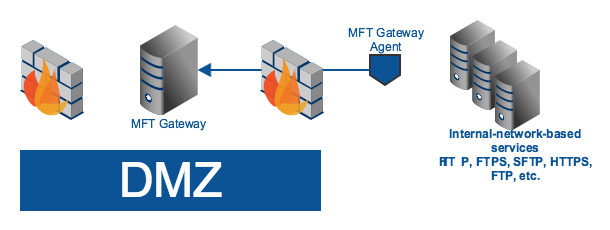
When a client application connects to MFT Gateway, the reverse proxy forwards a request to the agent and instructs the agent to establish a connection between the target internal server. Once the connection is established, the agent then creates a tunnel between the internal server, the agent, MFT Gateway, and the external client. It is through this tunnel that data exchanges will be made.
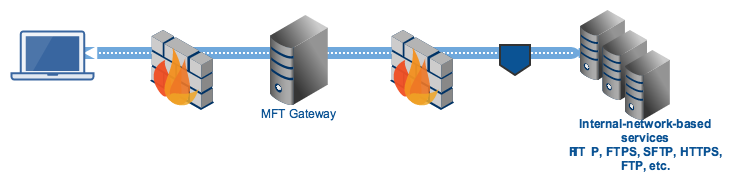
If you’re interested in trying this out, you may download a free, fully-functional evaluation edition of JSCAPE MFT Gateway and follow the installation instructions in the documentation.





