How to Use Reverse Proxy to Keep Sensitive Data Out of the DMZ

Overview
Deploying a reverse proxy and making use of DMZ streaming is an excellent way of keeping sensitive data out of your DMZ. Consequently, it can also help in achieving regulatory compliance.
In this post, we'll take a look at the risks of storing data in the DMZ, the regulatory issues you may run into, and how a reverse proxy can help resolve those issues.
The risks of storing data in the DMZ
Many companies share data with trading partners, customers, and other external users by placing managed file transfer servers providing FTP/S, SFTP, and HTTP/S in their DMZs. They put the servers there to prevent outsiders from gaining access to their private networks and sensitive data.
Although those managed file transfer servers may still have to retrieve data from databases in the internal network, only files containing the needed information are normally forwarded to the DMZ. Thus, trading partners and customers will be able to connect to the file transfer servers but not to the database server.
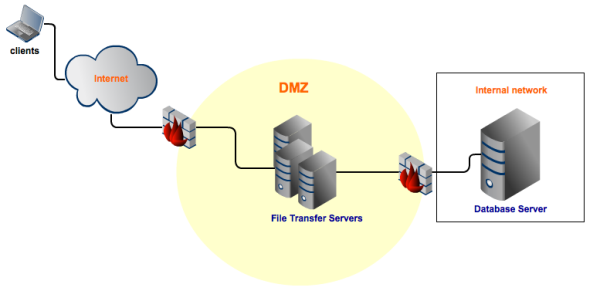
Obviously, by design, DMZs are not totally insulated from the outside world. So, attacks from the outside can still be mounted on file transfer servers placed there. Once attackers are able to gain access, they can easily obtain, destroy, or alter not only the data stored there, but also login credentials (usernames and passwords) and certificates, which may be found there as well.
Some companies might be able to afford this level of risk. But not all organizations have that luxury. If your company
-
handles credit card information,
-
is publicly traded,
-
belongs to the healthcare industry,
-
is considered a financial institution, or
-
if it simply conducts business in a US state that has a data breach notification law,
then you may encounter legislative / regulatory issues if you share data in this manner.
Laws and Regulations impacting data stored in the DMZ
No other law or regulation mentioned here is as explicit in prohibiting data from being stored in the DMZ as the Payment Card Industry - Data Security Standard (PCI-DSS).
PCI-DSS Requirement 1.3.7 instructs all covered entities to:
Place system components that store cardholder data in an internal network zone, segregated from the DMZ and other untrusted networks."
"System components" include file transfer servers, so you can't get any clearer than that.
PCI-DSS applies to all merchants, processors, acquirers, issuers, service providers, and all other entities involved in credit/debit card processing. If you're one of them, you should never store cardholder data in your DMZ.
Not all laws and regulations mentioned here contain equally explicit provisions against the storage of data in the DMZ. Nevertheless they do have onerous provisions that should make you seriously consider avoiding this practice.
One of these laws is SOX.
SOX or the Sarbanes-Oxley Act of 2002, which covers all publicly traded companies, has stringent data-related requirements for CEOs, CFOs, as well as for members of the Board of Directors and the Audit Committee. CEOs and CFOs, for example, are required to certify (among others) that:
1. Their company's periodic financial reports are accurate and reliable, and
2. They have designed, established, and maintained adequate internal controls over financial reporting.
CEOs and CFOs who are found to have made false statements in their certifications can be meted severe criminal penalties such as: a $1,000,000 fine or a 10-year imprisonment.
Let's assume you were a CEO or CFO of a publicly traded company. Knowing how vulnerable data in the DMZ can be, I don't think you would want to risk putting any financial reporting data there, where fraudulent individuals can alter them and, in turn, possibly render your finanical report inaccurate and unreliable.
Since we can't thoroughly discuss every single piece of legislation that impacts data stored in the DMZ in one post, here's a table summarizing: relevant laws and regulations, the data they aim to protect, and the businesses they apply to.
| Law/Regulation | Data protected | Businesses affected |
| PCI-DSS | cardholder information | merchants, processors, acquirers, issuers, service providers, and all other entities involved in credit/debit card processing |
| SOX | financial reporting data | publicly traded companies |
| HIPAA | personal health information | Individual and group plans that provide or pay the cost of medical care such as: health, dental, vision, and prescription drug insurers, health maintenance organizations, and Medicare; healthcare clearinghouses; and health care providers such as: nursing homes, doctors, and psychologists. |
| GLBA | nonpublic personal information | banks, non-bank mortgage lenders, real estate appraisers, professional tax preparers, debt collectors, payday lenders, check-cashing businesses, courier services, credit reporting agencies, ATM operators, and traditional and non-traditional financial institutions. |
| state data breach notification laws | personal information | All businesses that handle certain types of personal information (this varies from one state to another) |
How a reverse proxy in the DMZ can help you achieve regulatory compliance
Clearly, in order to ensure regulatory compliance, what you need here is a solution that will allow you to store all your sensitive data in your internal network but, at the same time, still make them securely accessible to associates who need to access them from the Internet.
One highly recommended method is DMZ streaming. It will allow you to stream data securely between external clients and the managed file transfers servers in your internal network. DMZ streaming can be carried out by using a reverse proxy like JSCAPE MFT Gateway, which will reside in your DMZ like this:
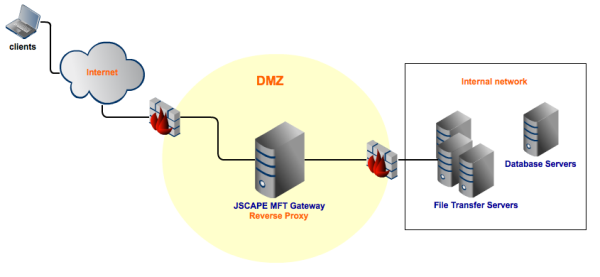
Files transmitted through your reverse proxy server via DMZ streaming never stay in that server. Upon receipt, they are forwarded directly by your reverse proxy to the client or to your file transfer servers, depending on whether the transfer is an upload or a download.
All this takes place transparently. Your external clients will carry out exactly the same steps and connect using the same port numbers and login credentials as if they were still interacting directly with your file transfer servers. They won't need additional software, hardware, or technical know-how.
The best part? Those clients won't be connecting directly to your file transfer server. In fact, they won't even know anything about your file transfer server. So all your sensitive data can stay secure.
Summary
You just learned a better way of providing secure file transfer services to your clients and trading partners without putting any data in your DMZ. This is done through the use of a reverse proxy like JSCAPE MFT Gateway.
You can give our reverse proxy a test run for FREE
JSCAPE MFT Gateway comes with a fully-functional evaluation edition which you can download right now.
Download Now