Taking Advantage of Amazon S3 Server Side Encryption

Just a couple of months ago, Amazon rolled out Server Side Encryption (SSE) on its online storage web service, S3. Amazon S3 Server Side Encryption allows you to encrypt files you upload to S3. Companies who are looking for better protection for data at rest and those who need to comply with regulations like HIPAA or data breach notification laws may find this bit of information very useful.
We'll show you how to set things up on the server and client side shortly. But first, a little background for those who aren't familiar with Amazon S3 Server Side Encryption.
Amazon S3 Server Side Encryption already employs AES-256, an encryption standard being adopted by the US government and is even used to protect government TOP SECRET information. In other words, it provides a considerably high level of protection.
When Amazon first announced this feature, it declared that it (Amazon) would be managing the encryption keys. This understandably drew criticisms from some security experts, who pointed out that, if the encryption keys are stored in the same location as the data, then anyone who can get a hold of the hard disks may be able to get a hold of the encryption keys as well. This would make it easy for that person to acquire the protected information.
Personally, I don't think it's as bad as some people assumed it would be. According to Amazon, every object is encrypted with a unique key. Secondly, the object key itself is encrypted by a separate master key. Third, a new master key is generated at least once a month. And lastly, which is the most crucial, the encrypted data, encryption keys, and master keys are actually securely stored on separate hosts.
Perfect for laws and regulations requiring encryption for data at rest
With the encryption keys stored separately from the encrypted data, plus the fact that AES-256 encryption is being employed, Amazon S3 SSE can very well help companies achieve regulatory compliance. In particular, it is well suited for laws and regulations that explicitly require not only strong encryption for protecting sensitive information but also that the encryption keys not be stored in the same location as the encrypted data.
In other words, it is very suitable for HIPAA and a number of state data breach notification laws. More so for those laws and regulations that don't require the encryption keys and encrypted data to be stored separately.
Other advantages of server side encryption
Server side encryption relieves end users from the hassle of having to carry out the encryption themselves. Your users can just upload files as is and then Amazon will take care of encrypting them. And because Amazon can take care of the encryption keys for your users, your users will be free of key management tasks as well. This is actually just the default arrangement. If you really want to manage those keys, Amazon has provided client libraries for that.
Another advantage of moving encryption from the client to the server is that it reduces network congestion. You see, encryption normally increases the size of your data. So if you upload data in encrypted form to your file server, it will consume more bandwidth than if it is uploaded in its original form. Hence, uploading very large objects won't be as big of a problem if you use server side encryption.
What could be a problem with server side encryption though is that, if the data has to go through an unprotected network, the privacy of your data can be compromised even before it reaches your server. It is therefore important to add a layer of protection during data transmission.
How to add protection for data in motion
On its way to the S3 servers and back, your data may be exposed to possible attacks. To mitigate the risks during transmission, Amazon allows users to upload and download their files via the secure HTTPS protocol. Of course, you would need a file transfer client that supports this protocol. I use AnyClient, our free FTP client that also supports a host of other protocols.
In a short while, I'll show you how easy it is to enable your S3 folders for server side encryption. After that, I'll demonstrate how equally easy it also is to configure AnyClient to work with the Amazon S3 SSE feature.
Ready?
There are two ways of encrypting files when you're logged into the S3 environment. If you want to do things in one go, i.e. if you want to encrypt all files that are already inside one particular folder, do the following:
- Choose the bucket that contains the folder you want to enable encryption on.
- Select the specific folder you want to enable encryption on.
- Click the Properties button
- Click the option button labeled AES-256
- Click Save.
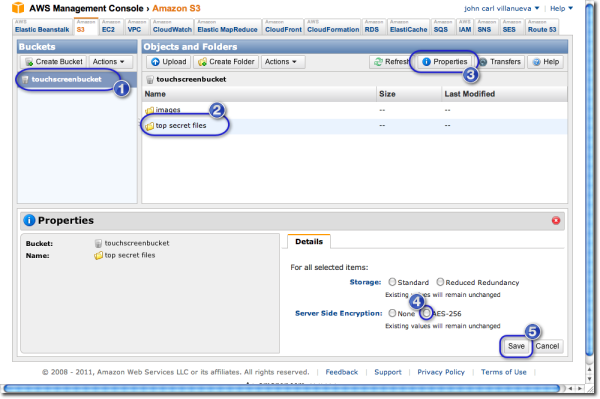
The steps shown would therefore encrypt all files found in the folder named "top secret files". However, if you only want to encrypt a particular file in that folder, then do practically the same thing but select a file instead of an entire folder. Of course, you will have to enter the folder to do that.
Still, this is not how you'd normally do things. In a real world scenario, you'll want files to be encrypted as they go in; not after they've been sitting there for some time. That means, in most cases, you'll be uploading files using your favorite file transfer client and you'll want to tell Amazon whether or not to encrypt those uploaded files right from that client.
I'll show you how to do that using JSCAPE AnyClient.
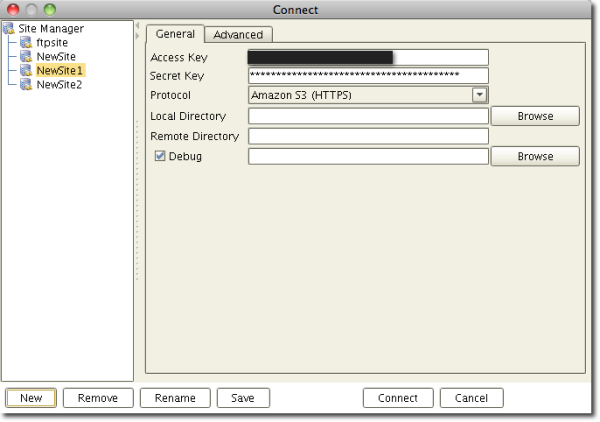
Here's a screenshot of the Connect (or Site Manager) screen in JSCAPE AnyClient. We've created a new connection (or site). In addition, we already entered the Access Key and Secret Key, which are also known as the Access Key ID and the Secret Access Key, respectively. We've also selected the HTTPS protocol to provide optimal secure file transfer protection once our data goes on its way through the network.
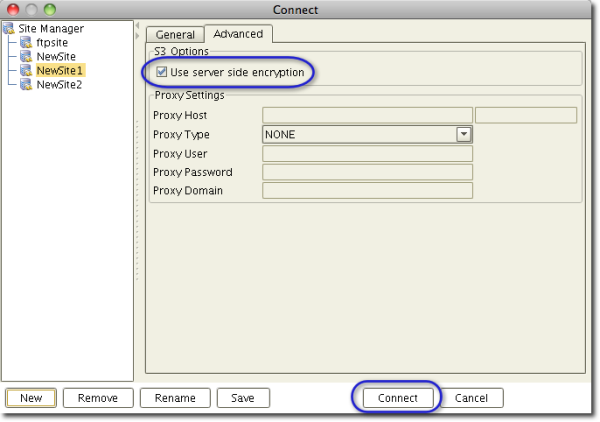
Now, in order to apply server side encryption to all files that will be uploaded through this connection, go to the Advanced tab and check the checkbox labeled "Use server side encryption." After that, click Connect.
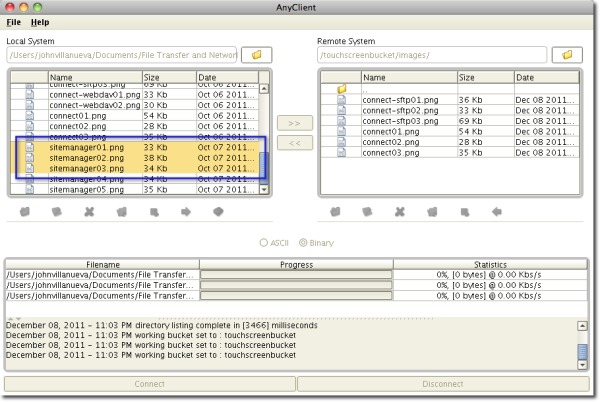
Once the client connects, you can then proceed uploading files just like before. Here's a screenshot showing 3 files being uploaded to the folder named "images".
Now, here are the properties of one of those uploaded files as viewed from the AWS Management Console. Notice that it has already been encrypted with AES-256 encryption.
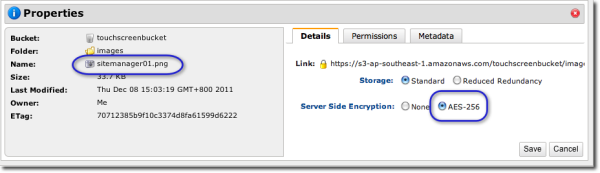
As you can see, the file was automatically encrypted once it got uploaded unto Amazon S3. Like it? Download the latest version of AnyClient now. It's free.