Excluding Passive IP for Internal FTP/S Connections To Your Reverse Proxy

Overview
Last time, we tackled the problem system administrators encounter when their passive FTP or FTPS connections have to pass through a NAT firewall or router. A similar problem can happen when you're dealing with the same type of connections and a reverse proxy. It gets even more complicated when you have to deal with both external and internal users. Let me show you how to deal with that.
To understand the problem better, I suggest you read the article "Setting Up An FTPS Server Behind A Firewall or NAT For PASV Mode Data Transfers" first. Notice that that article teaches you how to address the issue on the FTP/S server side.
Unfortunately, a similar issue can happen with a reverse proxy. More specifically, if your FTP/S reverse proxy is listening on an internal IP address but has to be reachable to external users. These users will likely have to go through your NAT-enabled router or firewall.
Here's a more concrete example. Let's say your FTP/S reverse proxy is listening on the non-routable address 192.168.1.1 but it can only be reached by external users through the external IP address 200.200.200.200. External users are those who connect over the Internet.
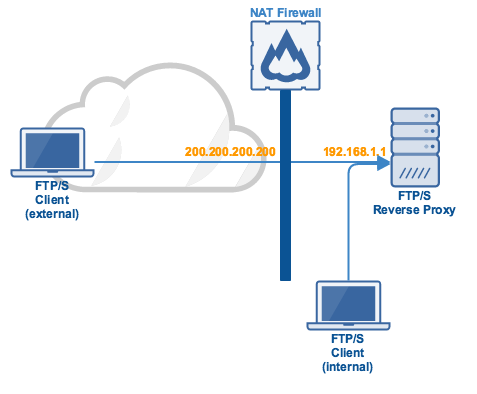
As soon as these users switch on passive mode while attempting to perform a directory listing, an upload, or a download, the connection will likely time out.
We already explained why this happens and how to deal with it in the previous article (see link above). A similar approach can be used to address this issue on your reverse proxy. That is, you need to configure your proxy to use the passive IP address 200.200.200.200 instead of 192.168.1.1 when responding to passive requests.
In JSCAPE MFT Gateway, this particular setting can be specified in the Services > FTP/S > Passive IP field.
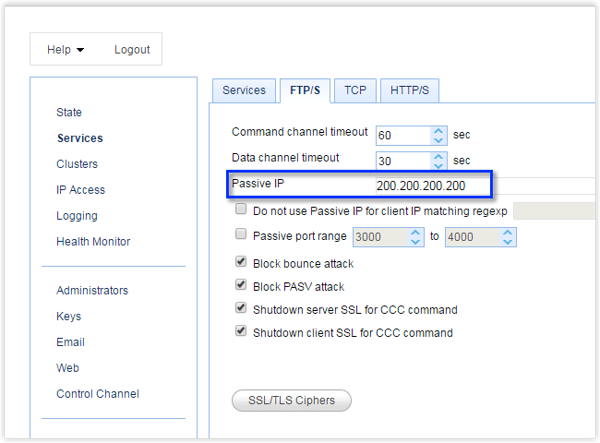
Perfect. That should now allow your external users to connect.
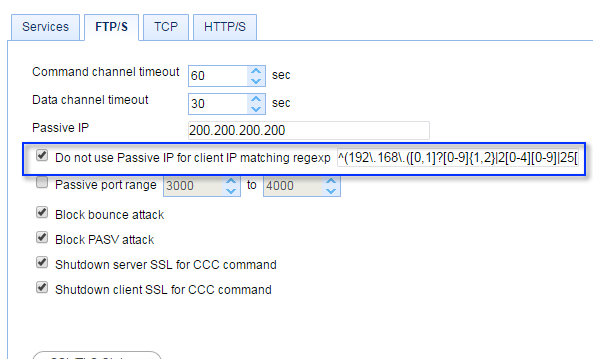
But how about your internal users? Surely, they're not supposed to use that passive IP address, right? To deal with internal users, you need to instruct your reverse proxy to exempt internal clients from using the passive IP address. That way, internal users will simply connect to your reverse proxy's internal IP address 192.168.1.1.
In JSCAPE MFT Gateway, you can do this by ticking the "Do not use Passive IP for client IP matching regex" check box and entering a suitable regular expression. For example, if you want to exempt all IP addresses within the range 192.168.0.0 to 192.168.255.255, then just enter:
^(192\.168\.([0,1]?[0-9]{1,2}|2[0-4][0-9]|25[0-5])\.([0,1]?[0-9]{1,2}|2[0-4][0-9]|25[0-5]))$
Other regular expressions you can use:
Note: I copied these regular expressions from here. While I have reviewed and tested these regexes, I strongly suggest you double-check,in case I missed something.
For the Range - 10.0.0.0 to 10.255.255.255:
^(10\.(([0,1]?[0-9]{1,2}|2[0-4][0-9]|25[0-5])\.){2}([0,1]?[0-9]{1,2}|2[0-4][0-9]|25[0-5]))$
For the Range - 172.16.0.0 to 172.31.255.255:
^(172\.(1[6-9]|2[0-9]|3[0-1])\.([0,1]?[0-9]{1,2}|2[0-4][0-9]|25[0-5])\.([0,1]?[0-9]{1,2}|2[0-4][0-9]|25[0-5]))$
That's all there is to it.
If you want to try this out yourself, download a free, fully-functional evaluation edition of JSCAPE MFT Gateway now.
Related articles
Active v.s. Passive FTP Simplified - Understanding FTP Ports
Mapping FTP, FTPS, or SFTP Server User Directories To Samba Shares
Understanding Key Differences Between FTP, FTPS and SFTP
Securing Trading Partner File Transfers w/ Auto PGP Encryption & FTPS
How To Set Up SSL Client Authentication on an HTTPS and FTPS Server