Required MFT Server Password Settings for PCI DSS Compliance - Part 2

In part 1, we enumerated all PCI-DSS requirements that directly affected password settings and practices. Here, we're going to show you how and where in JSCAPE MFT Server you can configure settings in order to meet those requirements.
All I'll have here are the numbers corresponding to those PCI DSS requirements, each immediately followed by the setting that will help you meet them. So I suggest you open Part 1 in another tab so it will be easier for you to refer to the details of a requirement on which a particular setting is based on.
Ready? Let's begin.
Requirement #2
Although JSCAPE's managed file transfer server does not come with any default system username and password, you might be tempted to enter the example admin username and password written in the documentation's installation instructions.
For example, in the installation instructions for Linux, there's a part in the online documentation that says:
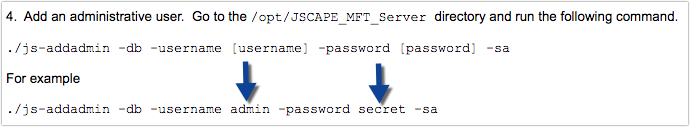
Don't use " secret " for your admin password. In fact, if possible, don't use "admin" for your admin username either. Because these instructions are available online, these sample administrative login credentials are available for all to see.
Requirement 2.3
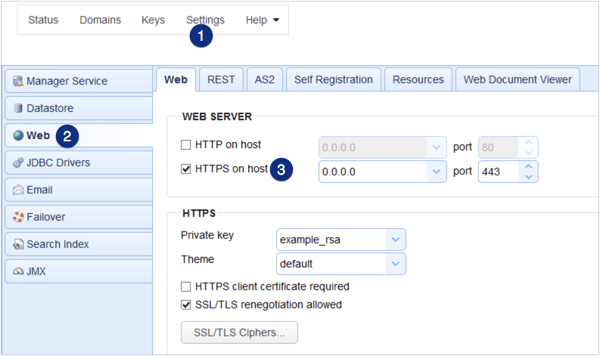
All communications between the JSCAPE MFT Server Web-based Administrative user interface and the server itself may be carried out via HTTPS, which in turn may be protected with TLS. Consequently, when HTTPS is used, administrative passwords are encrypted during transmission.
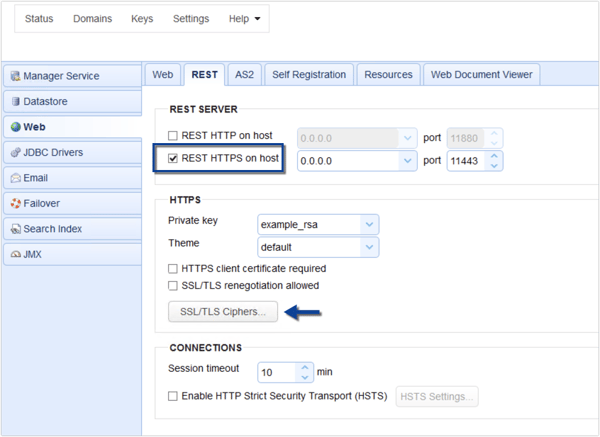
To force administrators to access the server using HTTPS, go to Settings > Web > REST tab.
Uncheck 'REST HTTP on host'
and
check 'REST HTTPS on host'
You can then select the ciphers that are considered strong (refer to part 1 of this article for guidance on what can be considered strong cryptography) by clicking the SSL/TLS Ciphers button.
For information regarding MFT Server support for TLS 1.2, read this.
Instructions for disabling SSL, TLSv1, and/or TLSv1.1 can be found here.
Requirement 6.3.1
A fresh installation of JSCAPE MFT Server does not come with any custom accounts and passwords.
Requirement 6.5.5
The error message displayed as a result of a failed login attempt on MFT Server's web user interface (whether the user enters a wrong username, a wrong password, or both) looks like this:
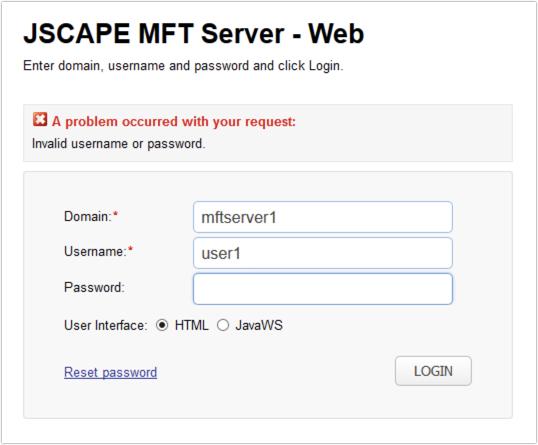
This kind of vague information isn't going to be very helpful to a hacker as he wouldn't know whether he was able to guess at least one login detail (username or password) or not.
Requirements 8.1.6 and 8.1.7
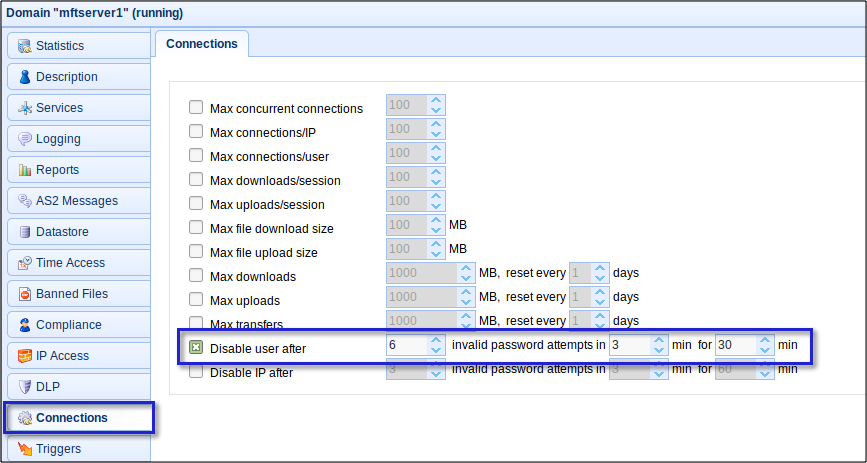
To lock out a user account for 30 minutes (or more) after 6 failed access attempts, navigate to the Connections node, tick the "Disable account after" check box, select 6 (or less) invalid password attempts, select a time duration over which the 6 failed attempts can be carried out (in _ min), and select the number of minutes the account should be locked out (for _ min).
Want to learn more about the consequences of having weak passwords? We recommend the blog post: Protecting FTP Passwords from Brute Force Attacks.
Requirement 8.2
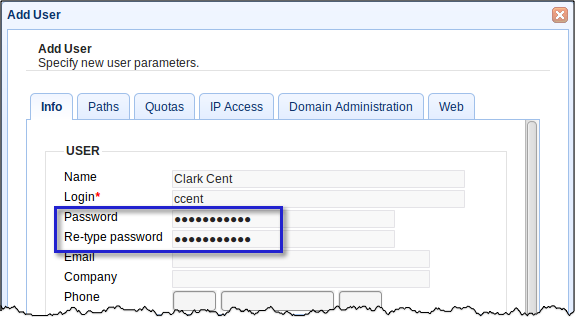
Every time you create a user account on your server, make sure you supply a password. If you don't, unauthorized personnel will be able to log in using that user account without anything barring their way.
In addition to passwords, MFT Server also supports other factors of authentication and even multi-factor authentication, wherein 2 or more methods of authentication are used to authenticate a user account.
Requirement 8.2.1
Some network protocols, like FTP and HTTP, send usernames and passwords in the clear. So you really have to avoid them. To comply with Requirement 8.4, stick with secure protocols like HTTPS, FTPS and SFTP, which encrypt your login credentials before transmission.
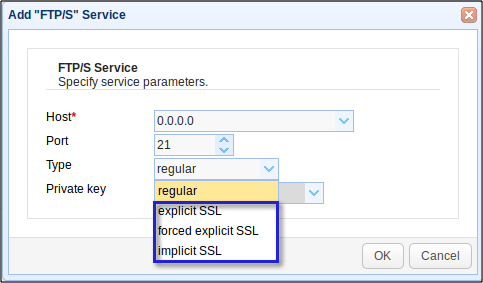
If you choose FTP/S for your Service Type when adding a new service, make sure you avoid regular, which is plain FTP. Instead, select explicit SSL, forced explicit SSL, or implicit SSL. The connections used by any of these three types are protected with SSL/TLS encryption.
Likewise, if you're using HTTP-based file transfer protocols (e.g. HTTP, WebDAV, AS2), make sure you protect them with SSL/TLS. In other words, enable HTTPS and configure your service to use it.
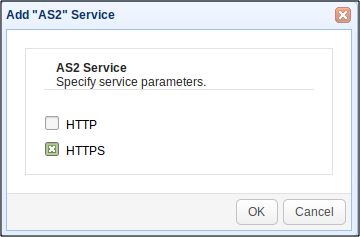
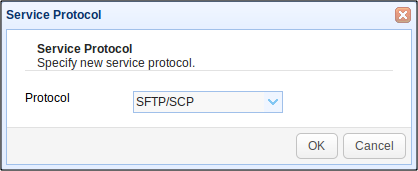
Another option would be to choose SFTP/SCP for the Service Type. SFTP/SCP connections are encrypted through SSH.
Requirement 8.2.2
There are a couple of ways to meet this requirement. If you are not face to face with the person requesting the password reset, you should throw him/her a challenge question. Of course, you would need to have a separate database containing challenge questions associated with your end users.
Alternatively, you can ask the person to send a text message from a phone number associated with that person. It would be less likely that an impersonator would also have the legit user's cell phone on hand. But like in the challenge question option described above, this verification option requires the presence of a separate database containing your users and cellphone numbers associated with them.
Now, there's actually an automated method for resetting passwords. It's a feature that comes with the JSCAPE MFT Server Web Gateway, which supports web-based secure file transfers.
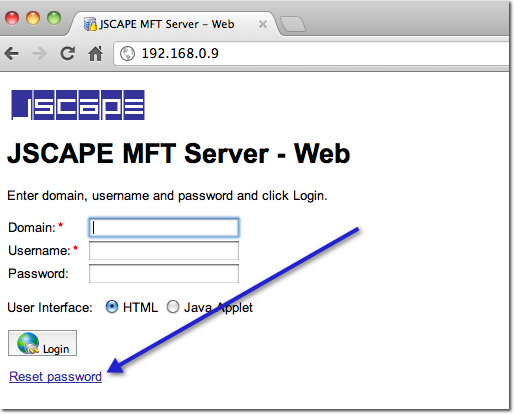
Like most modern web-based applications, the password reset is done automatically via email. I'll cover this in more detail in a separate post. In the meantime, here's a sample email notification a user would receive after that user requests for a password reset.
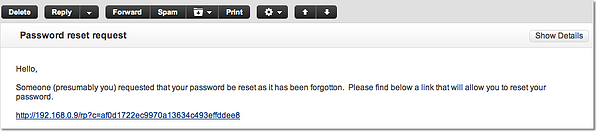
Please note however that this automated password reset method may not have the stringent identity verification process that PCI DSS requires. There's no challenge question here. If the email account is compromised, anyone can easily pose as a legit user. To be sure about the acceptability of this method, please consult your PCI-DSS QSA or ISA.
One way to mitigate the risk in this automated process is by creating a trigger that uses the 'User Password Reset Requested' event type in conjunction with a trigger action that sends out a notification to your server administrator. It's a bit similar to the trigger described in the article "How To Get An Email Each Time An Admin Account Logs In To Your Server" This will make your admin aware each time a user requests for a password reset and allow him/her to verify the validity of the request.
Requirements 8.2.3 - 8.2.5
To comply with requirements 8.5.9 to 8.5.12, just navigate to the Compliance node (see screenshot below) and do the following:
for 8.2.3:
Tick the "Minimum password length of" check box and set it to 7 characters (or more),
and
Tick the "Numeric (0-9)" check box.
Note that you can even require a combination of uppercase & lowercase characters, numeric characters, and even non-alphanumeric characters.
for 8.2.4:
Tick the "Maximum password age of" check box and set it to 90 days (or less).
for 8.2.5:
Tick the "Password must not match previous" check box and set it to 4 passwords (or more).
Here's a bonus feature. In case you want to send an automated notice reminding your users of an approaching password expiration date, tick the check box Email password change reminder and then select the number of days before expiration you want the reminder to be sent.
for 8.2.6
As mentioned in Requirement 8.2.6, when you create a new user, you always need to assign a password to it. But even that is not enough. 8.2.6 adds that that temporary password has to be unique and that the user should change it immediately after first use. The same should hold true for passwords temporarily assigned after password reset requests.
In JSCAPE MFT Server, new users can be forced to change their passwords during their first logins. This would require activation of the JSCAPE MFT Server Web Client. Once that feature has already been activated and the user has already been assigned a working email account, you can go to the Compliance node and tick the Require password reset on first time login check box.
Before the user can start using his JSCAPE MFT Server account, he should first go to the web interface described earlier, click the Reset password link, and then change the password as instructed.
Finally, to make sure all these password rules are enforced, tick the "Deny login for password non-compliance" check box, and then click Apply.
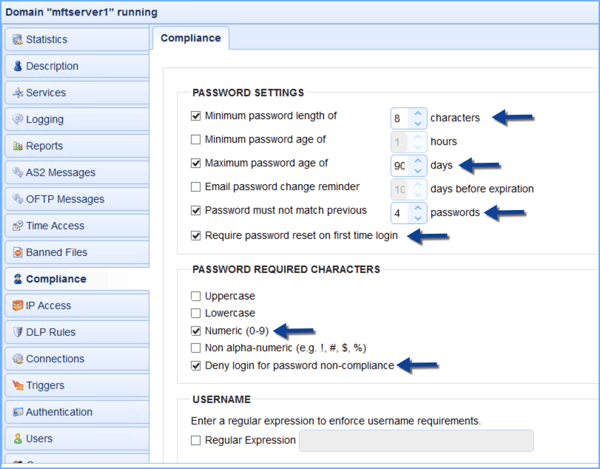
Notice that we've ticked " Require password reset on first time login ". This setting will ensure that your users will be forced to set their passwords according to the rules starting from their first login and whenever they request for a password reset.
Here's the error message a user will get upon entering a password that fails to meet one of those password rules.
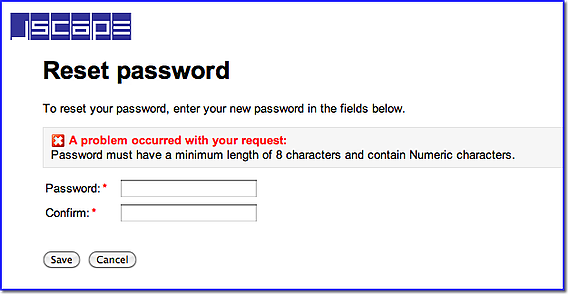
See to it that all users are given proper guidance regarding these stringent password rules. Otherwise, your Help Desk will be receiving a lot of calls from irate users.
Requirement 8.3
As mentioned earlier, when we talked about how to address Requirement 8.2, MFT Server supports several methods of authentication and allows you to combine them to achieve multi-factor authentication.
Requirement 8.5.8
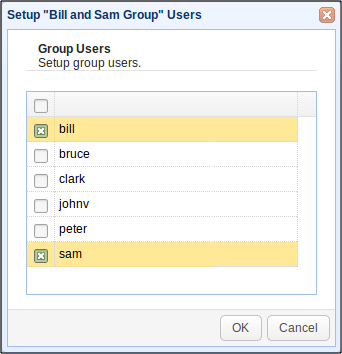
In JSCAPE MFT Server, it's possible to create Groups to which certain user accounts belong. But that doesn't mean those accounts share the same username and password. Each of those accounts still retain their own username and password. They even retain their individual identities in the logs. All that's actually shared between group members are directories and the files stored in them.
So, for example, even if Bill and Sam belong to the Bill and Sam Group,
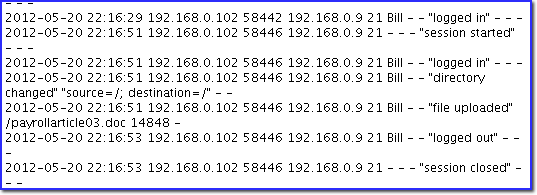
Bill's activities are logged separate from Sam's. Thus, accountability can still be readily enforced.
Summary
In this 2-part article, we started by talking about the PCI-DSS requirements that dealt with passwords and then showed you how you could meet those requirements in a JSCAPE MFT Server environment. Be aware that I am not a certified PCI-DSS specialist, and my views are based on my own interpretation of the PCI-DSS requirements. For proper guidance whether these features do meet PCI-DSS requirements, please consult your PCI-DSS QSA or ISA.
Build a PCI-DSS compliant file transfer server
Not all file transfer servers have built-in capabilities that help you easily adhere with PCI-DSS requirements. In most cases, you would have to perform a lot of integrations using disparate solutions before you can arrive at a fully-compliant system. In comparison, JSCAPE MFT Server comes with a comprehensive suite of security features that can help you easily build a PCI DSS-compliant file transfer system. If you haven't tried it out yet, you may download a free, fully-functional Starter Edition of JSCAPE MFT Server now.
Download JSCAPE MFT Server Trial