Using DLP to Protect Credit Card Data - Part 3

Applying OpenPGP encryption to a file containing credit card numbers
In Part 1, we showed you how to configure DLP on a group directory in order to detect uploaded files that contained credit card numbers. Then in Part 2, we laid out the steps for sending an automatic email notification whenever such files were detected. This time, we're going to teach you how to protect those files using OpenPGP encryption.
If you prefer to watch a video version of this blog post, click play below. Otherwise, please proceed.
First, let me explain why we need to go through this "encryption step". It would seem totally unnecessary considering that you already know how to configure JSCAPE MFT Server to "deny all access" once a DLP match is found.
Well, you really can't be too careful with sensitive data these days. Identity thieves are getting more skilled at breaking into IT systems. And so if they couldn't get to your data through a file transfer client, they certainly could try other options. Regardless of what option they take, the moment they are able to hack into your managed file transfer server and gain access to the file in question, they could easily obtain the information they need.
That's going to be easy for them because, most likely, your file is going to be in plaintext. They could simply copy the file and open it in their own computer using the needed software application.
For example, if the file in question is a .doc, then all they'll need is MS Word, OpenOffice, or any word processor that can open .doc files. If the file is .txt, then they'll just need a text editor. And so on and so forth.
So to prevent them from viewing the contents of the file even if they are able to somehow get hold of the file itself, the best solution would be to encrypt the file. This would render the file unreadable to those who don't have the required decryption key.
This is how you do it in JSCAPE MFT Server.

First you need to generate an encyption key. In the main screen of your JSCAPE managed file transfer server Manager, navigate to Sever > Key Manager.
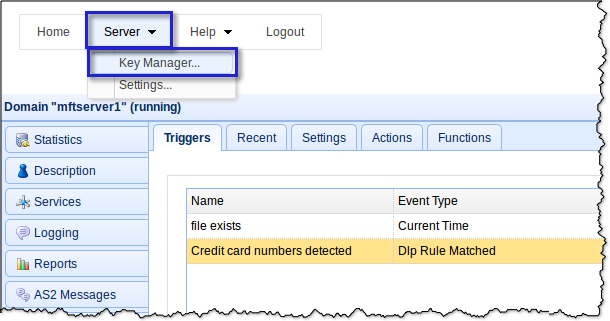
Next, go to the PGP Keys tab and click the Generate button.
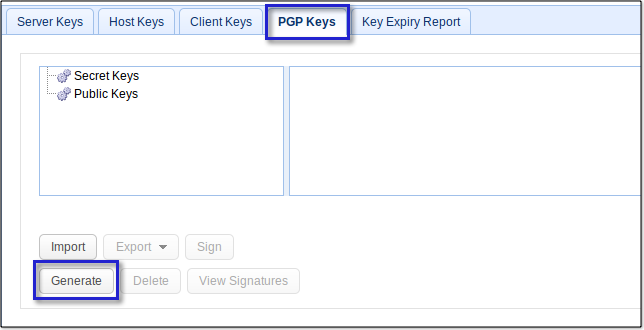
Assign a person's name to the PGP key (This might be the same person whom you've set the server to notify regarding the DLP match). Enter that person's email address and then select both a key algorithm (DSA or RSA) and a suitable key length. For some insights on choosing key lengths, read Choosing Key Lengths For Encrypted File Transfers.
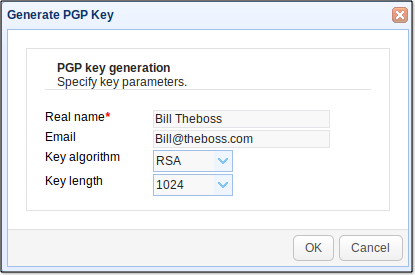
After you click OK, your newly created key will be added to the list of PGP keys.
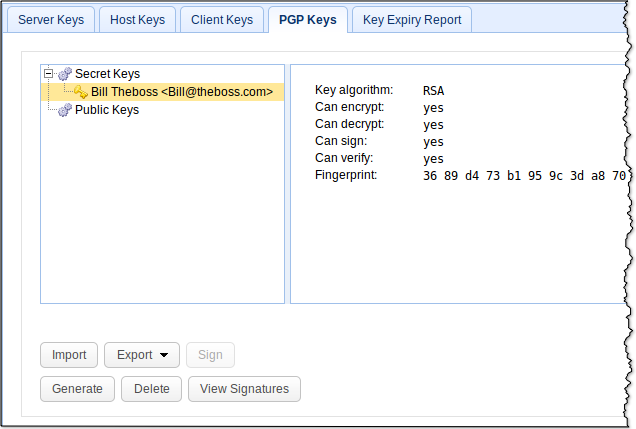
Now, go back to the Triggers module so you can add PGP encryption to the trigger actions of the "Credit card numbers detected" trigger you created earlier. Select the trigger and click Edit.
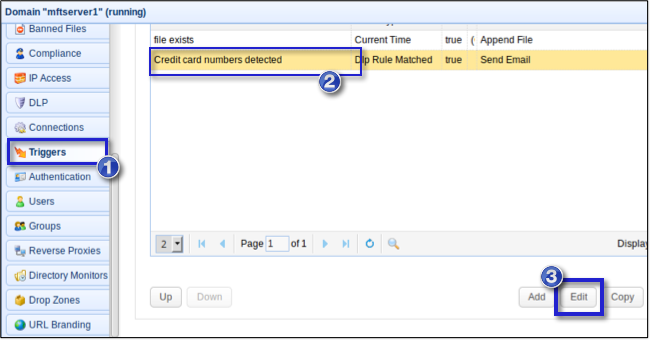
Click Next on each succeeding screen until you arrive at the list of Trigger Actions for that particular trigger. Click the Add button.
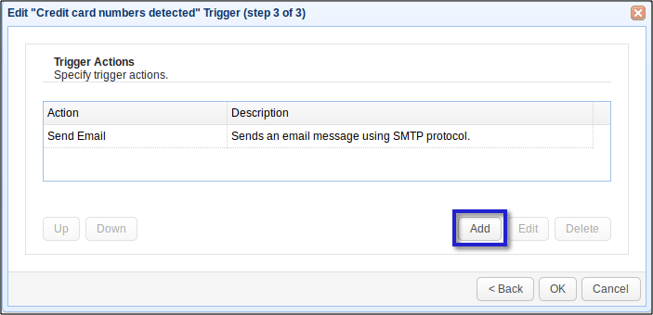
Select PGP Encrypt File from the Action drop-down list.
Enter %LocalPath% into the File field, and select the PGP encryption key you created just recently.
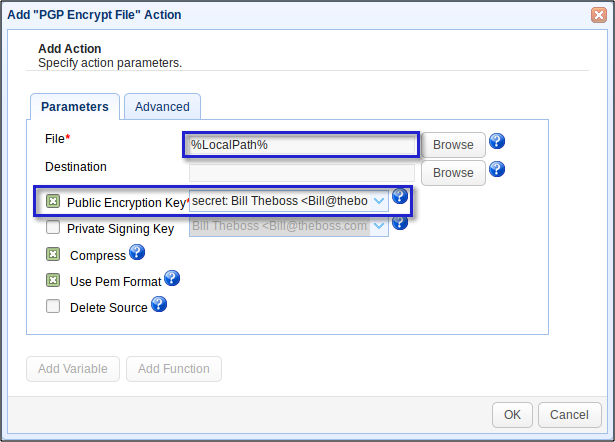
This is actually going to create a PGP-encrypted copy of the original file. Of course, the original file will still be vulnerable to attacks. To delete the original file and just leave the PGP-encrypted copy, just tick the the Delete Source check box.
After clicking OK, you'll see you're newly created Trigger Action (PGP Encrypt File) placed under the Trigger Action you created earlier (Send Email). This means, the email notification trigger action will be performed before the PGP encryption.
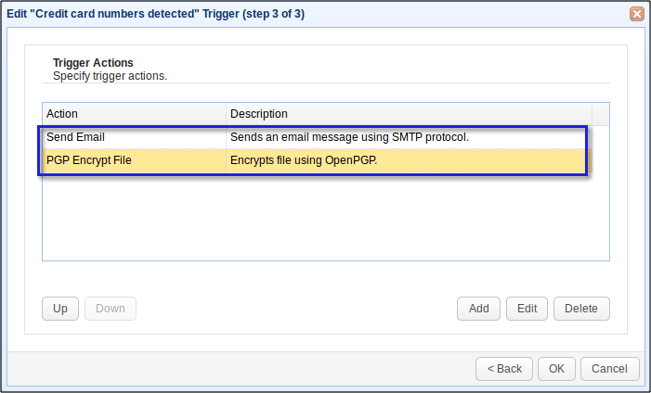
Click OK until you reach your domain's main screen. Again, you have to click Apply on that screen for the changes to take effect.
From this point onward, every file a user attempts to download from this group directory will be scanned for MasterCard numbers by the Server's DLP feature. Once a DLP match occurs, an email notification will be sent to the intendend recipient. The server will then create a copy of the file in question, encrypt that copy, and then delete the original file, leaving the PGP-encrypted copy in its place.
Note that the server will not be encrypting the entire group directory. It won't necessarily encrypt all uploaded files either. Rather, only those files that have DLP matches are going to be encrypted. This is actually a cost-saving feature because encryption can considerably increase a file's size. If you encrypt everything, including non-sensitive files, you'll run out of disk space in no time.
Another important thing to note is that the server will likewise prevent a user from downloading any file located in a DLP-protected directory, regardless whether that file has DLP-matching content or not, if that directory has not yet been indexed. Indexing settings can be configured in Settings > Search Index.
So, when a user attempts to download a file that has not yet been indexed, the server will unconditionally block that download and then index the file. Once the file has been indexed, the server will be able to determine whether the file contains DLP-matching content or not. In turn, the server will be able to take appropriate action (i.e., deny or allow) on all succeeding download attempts on the same file.
Summary
We've covered a lot of ground here. If you've read the entire article from Part 1 through Part 3, then you should now know why you would need to detect credit card information in uploaded files using DLP. You should also now be able to:
-
Create a DLP rule;
-
Notify a person through email once a DLP match on a file occurs; and
-
Enable your MFT server to perform selective auto-encryption on certain uploaded files.
Get Started Now
Would you like to try an FTP server that allows you to add DLP rules, send out email notifications, and PGP-encrypt sensitive files? Try the free, fully-functional evaluation edition of JSCAPE MFT Server. It supports FTP, FTPS, SFTP, WebDAV, OFTP, AS2, HTTP, HTTPS, and other file transfer protocols.
Download JSCAPE MFT Server Trial
You might also want to read:
How To Set Up a Server To Server File Transfer