How do Digital Certificates Work - An Overview

In our previous post, we discussed what a digital certificate is. But how do digital certificates work? Today, we will give you an overview of the basic process involving creating, signing, deploying, and using digital certificates.

Server Certificates
There are different types of digital certificates, but we'll focus on the server certificates used in secure web servers since they're the most common. You come across these kinds of certificates on the Web daily, particularly when connecting to sites that support HTTPS. A CA-signed server certificate is the kind of certificate you would need to deploy if you don't want Web browsers to display a warning when users attempt to connect to your secure file transfer server.
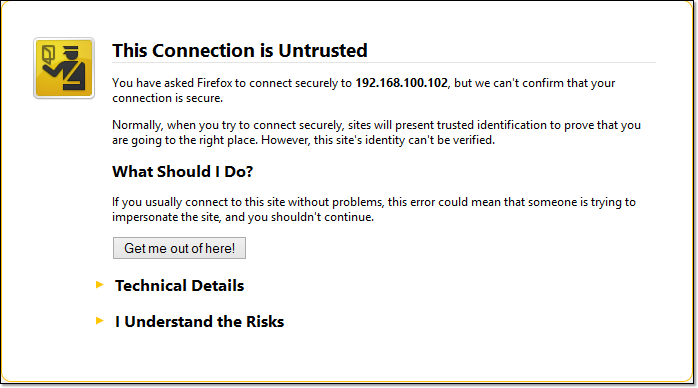
CA Certificates - the certificates in your browser
Before any major Web browser like Chrome, Firefox, Safari, or Internet Explorer connects to your server via HTTPS, it already has in its possession a set of certificates that can be used to verify the digital signature that will be found on your server certificate. These web browser digital certificates are called CA (Certificate Authority) certificates. On these certificates is a copy of the public key of the CA who might issue (sign) your server certificate.
CA certificates of widely accepted certificate authorities are already pre-installed on popular Web browsers, so we no longer worry about installing them. This explains how CA certificates can verify the digital signature on server certificates (more about this process later). The private keys that are used for signing the server certificates already have their corresponding public key pairs on our users' Web browsers.
Generating CSRs and having your cert signed by a CA
You can create your own digital certificate if you want. You can use free tools like OpenSSL. Alternatively, you can also use built-in tools that come with secure file transfer software like JSCAPE MFT Server.
You usually start by generating a private key / public key pair, followed by a CSR (Certificate Signing Request). The CSR would contain a copy of the public key and basic information about the subject. Once you've generated a CSR, you would then submit that CSR to a CA.
The article How To Set Up A HTTPS File Transfer includes a nice discussion detailing the steps of creating a digital certificate in JSCAPE MFT Server. Once the CA is done signing the cert, the CA would then return the cert to you and you would then import that signed certificate to your server.
If we recall our discussion on digital certificates, the signed cert would contain some basic information regarding the subject (your site), the issuer, the validity period, the public key (of your site), and a digital signature of the cert signed using the CA's private key.
In summary,
- You generate a private key / public key pair and submit a CSR to a Certificate Authority. The contents of the CSR will form part of the final server certificate.
- The CA verifies whether the certificate's information is correct and signs it using its (the CA's) private key. It then returns the signed server certificate to you.
- You import the signed server certificate into your server.
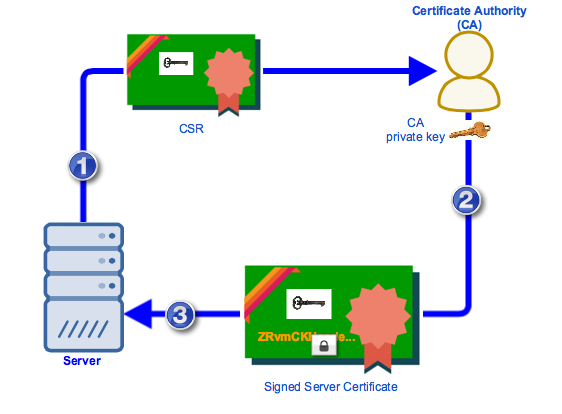
After submitting your CSR and getting your certificate signed, you're well on your way to enhancing your server's security. Want to see how this integrates into a broader security strategy? Book a demo with us to explore advanced security solutions tailored to your needs.
Sending of server certificate during SSL Handshake
Before a browser and an HTTPS server can exchange data over an encrypted connection, they first engage in a process known as the SSL handshake. One important part in the SSL handshake is sending the server certificate to the web browser. It's here when the Web browser is able to authenticate the identity of the server it's connecting to.
When the browser receives a copy of the server certificate, it checks which CA signed the server cert and then retrieves the CA certificate of that particular Certificate Authority. It then uses the CA certificate's public key to verify the server cert's digital signature.
To illustrate,
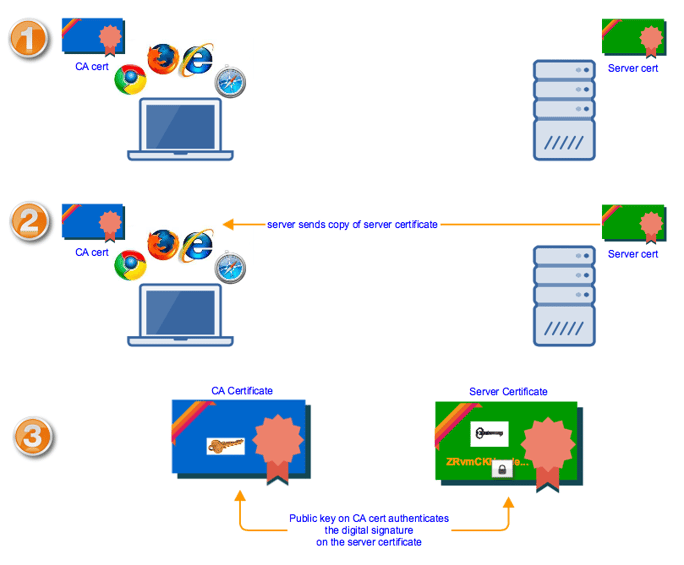
Once the digital signature has been authenticated, the browser and server can proceed with the rest of the SSL process. If you want to know how the public key on the server certificate is used, I suggest you read the article Roles of Server and Client Keys in Secure File Transfers.
Now that you have a basic understanding of digital certificates, you can start enhancing the security of your web file transfer.
Get Started
Looking for a secure web file transfer server? Download a free, fully functional evaluation edition of JSCAPE MFT Server today.